Posted on 10/10/2016 11:56:27 PM PDT by Swordmaker
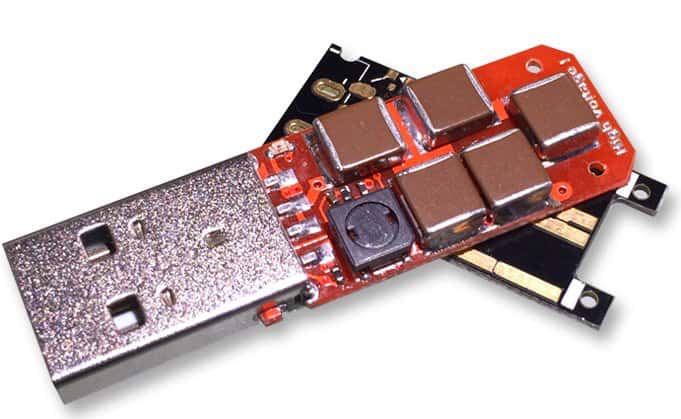
There’s a device out there called USB Kill 2.0 (or USB Killer and other variants) that can fry an electronic device with a USB port. While it looks like an every day USB flash drive, rather than memory, these devices have capacitors that can store up juice being transmitted over the USB bus and then discharge at once. The result is a high-voltage attack on your PC, Mac, smartphone, or other device that can fry the electronics.
YouTuber EverythingApplePro posted a demonstration video with one of these devices where he fried a PC and tried to fry an iPhone 7 Plus and a Samsung Galaxy Note 7. Yes, that’s the same Galaxy Note 7 that has been exploding in the wild, making EverythingApplePro a brave lad.
The short version is that this device appeared to fry the Lightning circuitry on an iPhone 7 Plus, but that device appears to have surge protection preventing broader damage. The Galaxy Note 7 didn’t appear to suffer any damage. The PC demonstrated on early in the video was fried lickety-split.
The interesting thing is that this is the kind of device you might see in a movie and shake your head because that’s now how things works. You can walk up to a PC, stick in a thumb drive, and destory it. Right?
But the principle here is sound: capacitors store up juice from the USB port and discharge it all at once. High voltage death then rains down on your device. It’s scary, and I’m glad that iPhones and the soon-to-be-extinct Note 7 are both protected.

Inside the USB Kill 2.0 – those circuits are capacitors
TheHackerNews reported in August that recent MacBook models are designed to protect against this kind of attack. Apple optically isolated the USB ports. My educated guess is that such protections will become de rigueur sooner, rather than later. But until then, one of these £49.95 (US$55.80) devices allows any miscreant or ne’er-do-well to wreck your day.
So be careful.
A 9mm is the only safe way to insure the data is not recoverable.
A D9 dropping it’s blade and a few back and forth passes would too. Preferably on a hard surface.
If I could understand your post perhaps I could apply for a mini degree in electrical engineering :)
Thanks much for the explanation.
Kind of like a personalized EMP.
The theory of operation is that USB traffic, by spec deals with POSTED commands. Essentially, this means that upstream there is a “Did younget this?” request that MUST be answered. It cannot be ignored.
By blowing out the data transmit/receive buffers, the bus and thereby the PC is permanently hung. Everything stops. With the transmit/buffers blown nothing gets communicated about a timeout or bad device.
That said, there is nothing that would lead one to assume that any data on a SSD would be affected as the Solid state drive is on a SATA bus, which is on a totally different bus hub structure than the USB bus. Further, PCI buses can be like a tree and have 3+ branches. Any of these branches could support multiple USB hubs, so depending which USB hub was blown, could mean limited loss of functionality or total.
That said, the opto-isolators are the best protection you will find for this type of attack.
Have a great fall day!
True. More economical. The malicious part I guess is that it could be done to a computer someone had been entrusted access to and the owner might not realize for a while, and thus might not know who had done it. A hammer is more honest.

Thanks to Swordmaker for the ping!!
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.