Posted on 01/03/2005 1:51:12 AM PST by goldstategop
Users have a lot to worry about when downloading and playing media files. Are the files legal? Can their computers play the required file formats? Now there's yet another problem to add to the list: Will a media file try to install spyware?
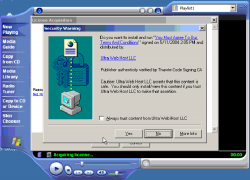
When Windows Media Player encounters a file with certain "rights management" features enabled, it opens the web page specified by the file's creator. This page is intended to help a content providers promote its products -- perhaps other music by the same artist or label. But the specified web page can show deceptive messages, including pop-ups that try to install software on users' PCs. User with all the latest updates (Windows XP Service Pack 2 plus Windows Media Player 10) won't get these popups. But with older software, confusing and misleading messages can trick users into installing software they don't want and don't need -- potentially so many programs that otherwise-satisfactory computers become slow and unreliable.
I recently tested a WindowsMedia video file, reportedly circulating through P2P networks, that displays a misleading pop-up which in turn attempts to install unwanted software onto users' computers. I consider the installation misleading for at least three reasons.

1) The pop-up fails to name the software to be installed or the company providing the software, and it fails to give even a general description of the function of the software.
2) The pop-up claims "You must agree to our terms and conditions" -- falsely suggesting that accepting the installation is necessary to view the requested WindowsMedia video. (It's not.)
3) Even when a user specifically requests more information about the program to be installed, the pop-up does not provide the requested information -- not even in euphemisms or in provisions hidden mid-way through a long license. Clicking the pop-up's hyperlink opens SpiderSearch's Terms and Conditions -- a page that mentions "receiving ads of adult nature" and that disclaims warranty over any third-party software "accessed in conjunction with or through" SpiderSearch, but that does not disclose installation of any third-party software.
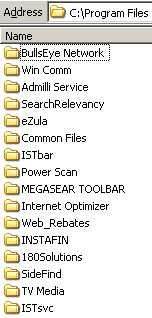
On a fresh test computer, I pressed Yes once to allow the installation. My computer quickly became contaminated with the most spyware programs I have ever received in a single sitting, including at least the following 31 programs: 180solutions, Addictive Technologies, AdMilli, BargainBuddy, begin2search, BookedSpace, BullsEye, CoolWebSearch, DealHelper, DyFuca, EliteBar, Elitum, Ezula, Favoriteman, HotSearchBar, I-Lookup, Instafin, Internet Optimizer, ISTbar, Megasearch, PowerScan, ShopAtHome Select, SearchRelevancy, SideFind, TargetSavers, TrafficHog, TV Media, WebRebates, WindUpdates, Winpup32, and VX2 (DirectRevenue). (Most product names are as detected by Lavasoft Ad-Aware.) All told, the infection added 58 folders, 786 files, and an incredible 11,915 registry entries to my test computer. Not one of these programs had showed me any license agreement, nor had I consented to their installation on my computer.
I retained video, packet log, registry, and file system logs of what occurred. As in my prior video of spyware installing through security holes, my records make it possible to track down who's behind the installations -- just follow the money trail, as captured by the "partner IDs" within the various software installation procedures. When one program installs another, the second generally pays the first a commission, using a partner ID number to track who to pay. These numbers make it possible to figure out who's profiting from the unwanted installations and, ultimately, where the money is going.
As I started to follow the money trail, I was surprised to see that some of these programs receive funds from respected online merchants. The spyware installations added new toolbars to my computer's browser and new icons to my desktop. If users click through these links, then make purchases from the specified merchants, the merchants pay commission to the affiliates who placed these toolbars and icons on users' PCs. Even large, otherwise-reputable companies pay commissions through these systems, thereby funding those who install unwanted software on users' computers. In my testing, I received affiliate links to Amazon, Dell, Hotwire, Match.com, Travelocity, and others. Many of these links pass through affiliate tracking networks LinkShare and Commission Junction. Of course, the merchants may not have intended to support spyware developers; they may have approved the affiliates without fully understanding the affiliates' practices. In future work, I'll look in greater detail at which merchants pay affiliate commissions to which spyware distributors, and I'll also further document which merchants purchase advertising from companies whose software sneaks onto users' computers.
Other companies partially responsible for these practices are the providers of the unwanted software -- who pay commissions to those who cause their software to be installed on users' computers. Some of the programs I received come from big companies with major investment backing: 180solutions received $40 million from Spectrum Equity Investors; DirectRevenue received $20 million from Insight Venture Partners; and eXact Advertising (makers of BargainBuddy and BullsEye) received $15 million from Technology Investment Capital Corp. With so much cash on hand, these companies are far from judgment-proof. Why are paying distributors to install their software on users' computers without notice and consent?
The problematic installations resulted most directly from the "feature" of Windows Media Player that lets media files open pop-up web pages. But most users will only receive the contaminated files if they download files from P2P filesharing networks. Of course, rogue media files are but one way that P2P networks spread spyware. For example, users requesting Kazaa receive a large bundle of software (including Claria's GAIN), after poor disclosures that bury key terms within lengthy licenses, without even section headers to help readers find what's where. Users requesting Grokster receive unwanted software even if they press Cancel to decline Grokster's installation (details).
Ed Bott offers an interesting, if slightly different, interpretation of these installations. Ed rightly notes that users with all the latest software -- not just Windows XP Service Pack 2, but also Windows Media Player 10 -- won't get the tricky pop-ups described above. Ed also points out that Windows Media Player displays of ActiveX installation prompt pop-ups are similar to deceptive methods users have seen before, i.e. when web sites try to trick users into installing software. True. But I think Ed gives too little weight to the especially deceptive circumstances of a software installation prompt shown when users try to watch a video. For one, legitimate media players actually do use these prompts to install necessary updates (i.e. the latest version of Macromedia Flash). In addition, the unusually misleading (purported) product name and company name make it particularly easy to be led astray here. Users deserve better.
If I start having problems with Word, I'll just switch to OpenOffice. And if I start having problems with Windows, I might switch to another OS.
The article does mention users of P2P networks who use an unpatched Internet Explorer and WM 9 Players are more vulnerable to this rogue download. But the fact this ready exploit exists means every one should keep up their guard and lock down IE, use an alternative browser (like Firefox) where possible and turn off the automatic notification feature in WMP. No one wants to have to clean up a crippled computer loaded with tons of unwanted scumware.
I installed OpenOffice on both of my computers. I like the GUI better than MS Office and all of the outputs open in Office (on my company notebook).
As for the spyware that is the subject of the original post? Some people seem to automatically click the "yes" and "Install" button whenever a dialog box pops up on their screens.
Cybernetic mayhem is generally targeted at four kinds of things, i.e. windows itself, ms word, outlook, and the internet explorer. To the extent that you can avoid any of those things, you're safer and better off. I do all of my email and most of my web browsing on a linux machine, and avoid ie and outlook altogether.
Admin authority is a Windows user default. Create another ID and change it to non-admin and use only that lesser ID.
I most assured this is the case. I worked a little with LinkShare and FTD.com affiliate programs. FTD was very concerned about trademark violators and web content.
Its due to a poor DRM design by Microsoft. Ironically, as Eric L. Howes has observed P2P users illegal MP3 files are more secure than MS's own WM files! Its a commentary on the state of the industry that no one wants to make DRM secure for consumers who browse to listen and watch on the web. Enough of these abuses and people may get turned off to multi-media content altogether.
There's a lot of rip-off software on the web too. Most of it useless.
Even reading articles on FR, the package will block out material from questionable sources and all sorts of places I really don't want to receive data from. Neat stuff.
Its still a resource hog. Until PeerGuardian 2.0 is released, I'm running Protowall. Its from Bluetack.co.uk.
I'll have to check. I hadn't noticed any degradation of performance, but then I'm not doing everything I normally do on this machine yet. I'll check it out. For all that I do it seems to work out fine. What I'll do in the future is shut it all down for stuff I do off line and see if there's a difference. Live and learn...
One of the biggest offenders in malware-infected Windows Media files is LoudEye, which, by the way, provides the system that runs the MSN music store.
LoudEye (Symbol LOUD) is a public company. These guys a riding for a particularly hard fall.
Wow. You all seem to know a lot about this stuff. I've had my computer crash back in July of '04. I was getting ready for a major presentation, The First World Congress on Agroforestry. The computer crashed a week before ....man was I mad...new Dell too. Won't get into some of the 'award winning service' issues, but maybe you could answer a simple question now.
Last week I upgraded to a high speed DSL service. I run Ad Aware at the end of each session, mostly cookies show up. And Norton Internet Security System runs constantly. I've not had any real problems since July, until the scheduled scan with Norton yesterday. I didn't know what to do with the spyware detected. Ad Aware didn't catch it. The reason I didn't was it was installed with the software for the DSL. I know this 'cause it wasn't in the list of programs before installation. Norton says it's Visual IP Insight(SBC) and should be removed although it's low risk.
I was told by the provider that my first 10 days on DSL service would be tracked in order to determine my internet habits and tune up the DSL. I tend to believe them as service is from SBC.
Can I delete this IPInsight or should I?
Since I have been posting at FR, I have seen a huge jump in spam offering me green cards to work in the USA. I am an American citizen and don't need a green card, but of course my Canadian IP and residence and my frequenting of American political websites tags me as someone who wants to move to the USA ... I get up to 4 spy cookies from FR every time I sweep with ADAWARE after I've been here.
Last time I looked, intentionally spreading computer viruses on the internet is a crime.
It is surprising how many (even FR-eepers) refuse to install and run
1. A virus checker (there are free ones)
2. Spyware checkers/eliminators (there are free ones)
3. Intrusion-prevention programs that try to keep malware from taking over or running unauthorized executables (there are free ones)
4. Email previewers (there are free ones)
5. Firewalls (there are free ones)
Many prevention programs are available and several good ones are free.
===
If you aren't running these, you are part of the problem, people!
Define "Spy Cookies".
Cookies are generally speaking text files YOU have given the website you are visiting permission to log on your machine to help remember who you are and what you have done. The key here is that YOU ALLOWED the cookies. Without them, I would have no idea that you responded to this little reponse.
Spyware is much different than a few cookies.
If you don't want cookies, turn them off.
Update SpyBot too. They are adding new checks every day. Currently more than 24,000.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.