Skip to comments.
This Massive Chinese Cyberattack on Our Networks Is a Disaster of Unimaginable Proportions
Hotair ^
| 10/07/2024
| David Strom
Posted on 10/07/2024 8:22:44 PM PDT by SeekAndFind
Using a security loophole that allows the US government access to anybody's electronic traffic, Chinese hackers gained access to an unknown quantity (perhaps all) of internet traffic on American networks. In an exclusive report in Saturday's Wall Street Journal the secret breach was revealed.
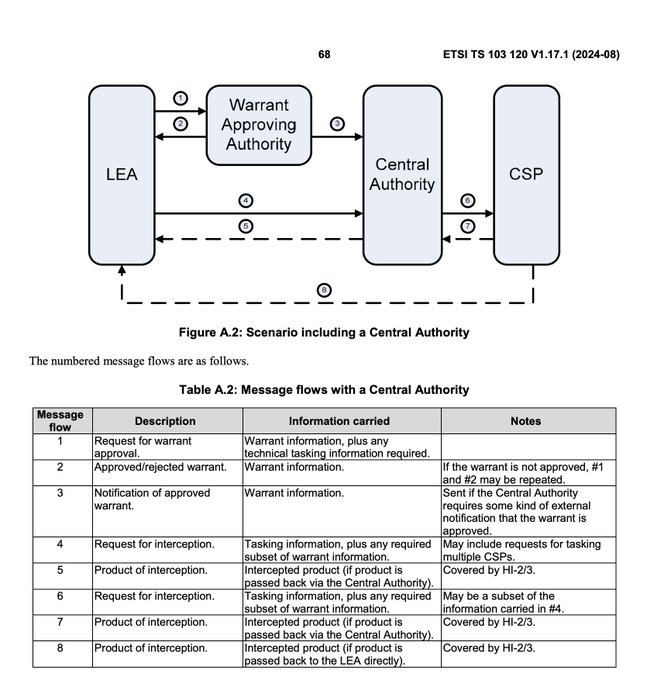
The attack SOUNDS like the hackers could potentially have access to everything that crosses certain networks by using backdoor access that the US government mandates to permit wiretapping when authorized by a warrant. In other words, there is a built-in insecurity to the networking systems in order to allow government officials to tap your data. The Chinese got access to the backdoor.
A cyberattack tied to the Chinese government penetrated the networks of a swath of U.S. broadband providers, potentially accessing information from systems the federal government uses for court-authorized network wiretapping requests.
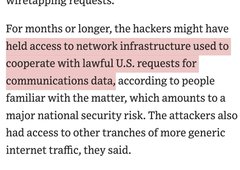
For months or longer, the hackers might have held access to network infrastructure used to cooperate with lawful U.S. requests for communications data, according to people familiar with the matter, which amounts to a major national security risk. The attackers also had access to other tranches of more generic internet traffic, they said.
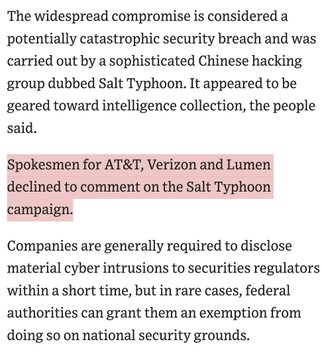
Verizon Communications, AT&T and Lumen Technologies are among the companies whose networks were breached by the recently discovered intrusion, the people said.
The widespread compromise is considered a potentially catastrophic security breach and was carried out by a sophisticated Chinese hacking group dubbed Salt Typhoon. It appeared to be geared toward intelligence collection, the people said.
The wording here is a little vague, and I think intentionally so, about whether the Chinese had access ONLY to data that the US government was wiretapping. That seems impossible, given that the access to wiretapping abilities is not limited to splicing wires or something like that. It is a function of software, and that software was hacked. In this case the Chinese could access whatever they chose. No doubt that didn't include everything, since there would be no way to store and make sense of it all, but as with our own government they could target whomever they wanted using the security hole built into the system.
The surveillance systems believed to be at issue are used to cooperate with requests for domestic information related to criminal and national security investigations. Under federal law, telecommunications and broadband companies must allow authorities to intercept electronic information pursuant to a court order. It couldn’t be determined if systems that support foreign intelligence surveillance were also vulnerable in the breach.
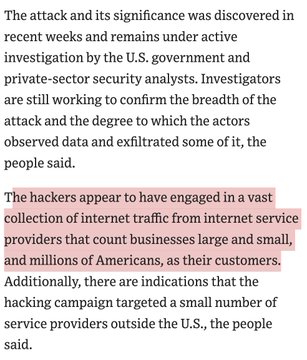
The attack and its significance was discovered in recent weeks and remains under active investigation by the U.S. government and private-sector security analysts. Investigators are still working to confirm the breadth of the attack and the degree to which the actors observed data and exfiltrated some of it, the people said.
The hackers appear to have engaged in a vast collection of internet traffic from internet service providers that count businesses large and small, and millions of Americans, as their customers. Additionally, there are indications that the hacking campaign targeted a small number of service providers outside the U.S., the people said.
A person familiar with the attack said the U.S. government considered the intrusions to be historically significant and worrisome.
Again, with the weasel words. To me, this sounds catastrophic for anybody targeted. The Chinese had access to anything from anybody they targeted across these networks. Think of all the sensitive data YOU send over the internet, such as financial information, and multiply that a millionfold for the companies and government.
I say weasel words because, if I am reading between the lines, basically everything that travels over the internet (presumably the most sensitive government information uses a closed system, although I don't know that at all) was wide open to the Chinese. Wide open.
“It will take time to unravel how bad this is, but in the meantime it’s the most significant in a long string of wake-up calls that show how the PRC has stepped up their cyber game,” said Brandon Wales, former executive director at the Cybersecurity and Infrastructure Security Agency and now a vice president at SentinelOne, referring to the People’s Republic of China. “If companies and governments weren’t taking this seriously before, they absolutely need to now.”
Salt Typhoon has been active since 2020 and is a nation-state hacking group based out of China that focuses on espionage and data theft, particularly capturing network traffic, Microsoft said in a research note written in August. “Most of Salt Typhoon’s targets are based in North America or Southeast Asia,” Microsoft said, noting that other cybersecurity companies call the group GhostEmperor and FamousSparrow.
Could any of the recent outages in service, particularly on Verizon, be related to this attack? I do not know, but if so it wouldn't necessarily have to be a direct result of a cyberattack to disrupt the system. It might be possible that efforts to update the security of routers and other equipment might be related. That is just speculation on my part, though.
It seems to me that the story downplays how significant this attack was. It sounds catastrophic to me, and it was directly caused by government mandates to require a security loophole.
Mandates so strict that the French arrested the CEO of Telegram, Pavel Durov, to enforce their demand for access to his platform. No doubt the US pushed for this as well as the French.
Spies used to risk their lives or imprisonment in order to get blurry photos of classified information. From half a world away, the Chinese got access to almost everything for months...or longer.
This should be one of the biggest stories right now, not Kamala Harris' appearing on a sex podcast and Howard Stern.
Our leaders are not serious people.
TOPICS: Crime/Corruption; Foreign Affairs; Government; News/Current Events
KEYWORDS: bidencrimefamily; china; crookedhackers; cyberattack; hacking; internet
Navigation: use the links below to view more comments.
first 1-20, 21-22 next last
To: SeekAndFind
To: SeekAndFind
So, here's the deal: We've got the U.S. government doing its thing, you know, keeping tabs on folks through these court-authorized wiretaps. It’s "for our own good," they say. The same arguments come up when they say they need backdoors into all encryption. “Save the children!” they cry in order to absolutely decimate your privacy.
To: SeekAndFind
So, here's the deal: We've got the U.S. government doing its thing, you know, keeping tabs on folks through these court-authorized wiretaps. It’s "for our own good," they say. The same arguments come up when they say they need backdoors into all encryption. “Save the children!” they cry in order to absolutely decimate your privacy.
To: SeekAndFind
Why is this not an act of war?
5
posted on
10/07/2024 8:25:25 PM PDT
by
ifinnegan
(Democrats kill babies and harvest their organs to sell)
To: SeekAndFind
“Our leaders are not serious people. “
Absolute truff.
[I think Trump is series, along with Musk. Not many others though. :-(]
6
posted on
10/07/2024 8:27:38 PM PDT
by
Paladin2
To: ifinnegan
Because of Brain Dead and Kackles.
7
posted on
10/07/2024 8:28:34 PM PDT
by
lightman
(I am a binary Trinitarian. Deal with it!)
To: SeekAndFind
Protecting children from terrorists is what communism is all about but now that the feds have granted themselves access to every bit of information about us well that was not enough so they need to record and store that information so that it can be used against us later.
You wanna know why microsoft needs a nuclear power plant to be brought on line for their data centers? It is to collect and store all that information about us.
That is the big secret in this story.
8
posted on
10/07/2024 8:37:42 PM PDT
by
jdt1138
(Where ever you go, there you are.)
To: ifinnegan
Because Democrats are Marxists and GOP are Quisling traitors.
9
posted on
10/07/2024 8:42:57 PM PDT
by
grey_whiskers
(The opinions are solely those of the author and are subject to change without notice.)
To: SeekAndFind
Using a security loophole that allows the US government access to anybody's electronic traffic Don't EVEN try to tell me that no one ever warned that this might would happen...
10
posted on
10/07/2024 9:26:19 PM PDT
by
logi_cal869
(-cynicus the "concern troll" a/o 10/03/2018 /!i!! &@$%&*(@ -)
To: SeekAndFind
11
posted on
10/07/2024 9:28:01 PM PDT
by
dadfly
To: jdt1138
I think they need all the power to run AI.
Storage and collection is easy.
AI is brute force... and that takes a lot of power. Lots of calculations... brute force.
12
posted on
10/07/2024 10:06:33 PM PDT
by
Sarcazmo
(I live by the Golden Rule. As applied by others; I'm not selfish.)
To: ifinnegan
Ha Ha!
Because the Walz WANTS to lick chinese boots. He is gay for chinamen.
13
posted on
10/07/2024 10:08:28 PM PDT
by
griffin
(When you have to shoot, SHOOT; don't talk. -Tuco)
To: ifinnegan
Why is this not an act of war? finnigan, for the love of God start thinking outside the box. It sounds to me as if the Chinese had some inside help exploiting that "security loophole." But I'm sure this article, and others to follow, would rather Americans like you believe this event was about a "computer hack" rather than sabotage. And remember, I'm here to help you.
14
posted on
10/08/2024 2:02:18 AM PDT
by
JonPreston
( ✌ ☮️ )
To: SeekAndFind
IF THERE IS A MASSIVE LAW SUIT AGAINST MICROSOFT...I SOOOOOO WANT TO BE A PART OF IT.
I USED TO ENJOY GOING ON COMPUTER FOR INFORMATION, BUT SINCE I GOT THIS BIG MAHAFEE ...NEW COMPUTER...I DON’T HAVE CONTROL, NOR CHOICE OF THE “NET”.
I COULD EASILY SAY.....GOODBYE TO COMPUTER WORLD FOREVER.
To: SeekAndFind
The sheer blackmail potential explains a lot about how the elite behave.
Every email, text, and call has been compromised by Biden/harris incompetence
16
posted on
10/08/2024 4:05:19 AM PDT
by
TheThirdRuffian
(Orange is the new brown in)
To: Maris Crane
You might consider switching your computer to Linux.
17
posted on
10/08/2024 4:08:35 AM PDT
by
billakay
To: SeekAndFind
The Deep State (aka USA government) is afraid of the people. This is good. They should be afraid.
The skullduggery committed by these depraved, filthy evil, power crazed globohomo’s in Washington, London, Paris, and Brussels (along with the junior lickspittle partners in Ottawa, Canberra and Wellington) are finally coming to an end, and they WILL be held accountable.
Sever pain and punishment is coming and the entire world is going to feel it.
18
posted on
10/08/2024 4:17:15 AM PDT
by
Flavious_Maximus
(Tony Fauci will be put on death row and die of COVID!)
To: SeekAndFind
“....backdoor access that the US government mandates to permit wiretapping when authorized by a warrant. “
~~~
Riiiiiighhtttt. “Warrant”
Suuuurrreee.
If the chinese hackers had unfettered access to our internet spying apparatus without anything restricting them like pesky little “warrants”, then anyone in the deep-state had access to our internet spying apparatus.
19
posted on
10/08/2024 4:45:58 AM PDT
by
z3n
(Kakistocracy)
To: billakay
Not being that computer savvy, I shall look into it.
I was told there is only Microsoft and Apple.
Some choice.
Navigation: use the links below to view more comments.
first 1-20, 21-22 next last
Disclaimer:
Opinions posted on Free Republic are those of the individual
posters and do not necessarily represent the opinion of Free Republic or its
management. All materials posted herein are protected by copyright law and the
exemption for fair use of copyrighted works.
FreeRepublic.com is powered by software copyright 2000-2008 John Robinson