Posted on 10/14/2015 1:42:29 PM PDT by Swordmaker

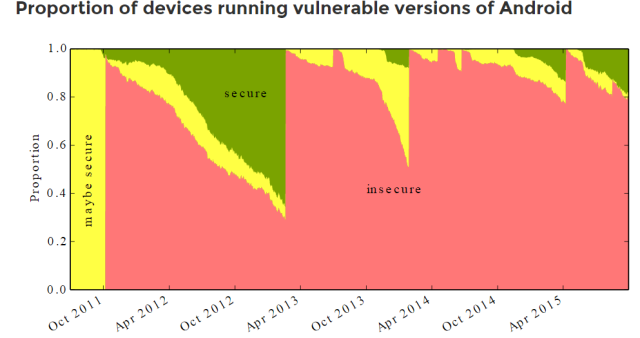
University of Cambridge study finds 87% of Android devices are insecure

No, just an Android user.
I was being provocative in the spirit of competition. Sheesh.
From your link:
AS LONG AS hackers have sold their secret hacking techniques known as zero-day exploits to government spies, they’ve generally kept that trade in the shadows. Today it’s come into the spotlight with the biggest bounty ever publicly offered for a single such exploit: $1 million for a technique that can break into an iPhone or iPad running Apple’s freshly released iOS 9.The biggest bounty ever. . . that should tell you something about the security of the iPhone's operating system.
As far as component level intrusions, finding those exploits is extremely difficult. This is why the highest security needs shouldn't use Chinese components. You can't trust them. Encryption is meaningless at that point, the hacker is already in and the user is totally unaware.
Only what is needed at the moment is unencrypted on the device, Paco. . . and if you think that a dedicated minor chip, most of which are not made in China, can hide sophisticated functionality to send data hidden amongst other data with the scrutiny it gets, you are delusional. The Chinese are not the ones who make the chips. . . They assemble the devices while the chips are made in Korea, Japan, Taiwan, or the US. They may burn EPROMs, but if a manufacturer allows malicious code in, that's a failure of their quality control, not sneaky hacking.
As my cyber security expert colleague tells me, hackers work smarter not harder. They don't want to decrypt anything. They use tools that steal data after it's been decrypted. Granted, AES will slow down or stop the "script kiddies" from gaining access but won't deter the pros.
Non-electronic hacking is a "sneaky," way cool method of hacking. It picks up vibrations on so-called smart phones and leaves no fingerprints.
The point is, people think they're secure and they're not.
You just showed me you really don't know what you are talking about with that comment that AES won't "deter the pros."
Of course they don't want to decrypt anything. . . they can't. This idea that even the "pros" can do it is delusional. I know what I am talking about here, Paco. NOBODY can decrypt an AES encryption without the key. It simply is not possible.
A mere 16 character, complex key entangled with the UUID of the device results in a 140 character key for the encryption. . . and without the key it would take 5.62 undecillion YEARS to decrypt using the only means possible, a supercomputer trying every possible key by brute force.
I've argued this "non-electronic hacking myth" before with people who claim it is possible. . . First of all, it is not "non-electronic" and any idea that someone can extract viable data from "vibrations" on smartphones is purely myth. Data is dense and vibrations are NOT dense. . . and therefore cannot carry any data worth anything of value. Someone is pulling your leg.
Someone was trying to claim they could read the radio signals from the wires leading from the screen to the interpreter and thereby extract the passcode being input when a user unlocked his smartphone or later other passwords. . . from a distance. BullSH!t. The traces on the screen, or ribbon cable is not long enough and the power is not strong enough to generate a signal that can be isolated and extracted from all the background noise of the electronics in the phone to find any usable data.
Other proposals are to intercept the phones before delivery and insert chips to extract decrypted data and then send it to a secret website or email it to a malicious destination. This was supposedly the method used against Angela Merkel, the German Chancellor. Again, easily discovered by monitoring the output of the device because any such added electronics have to use the existing radios. This is your scenario, only the chips are modified at manufacture. Except that Apple, for example, intercept random products from the line and tears them down and tests them out the kazoo in their own labs for compliance to their engineering, including going through ever chip in them. Again, you are proposing a MYTH.
Now you can stay paranoid if you like, but frankly, that is what it is. Paranoia. There is a reason why the government is pissed of at Apple for not allowing them to have a backdoor into their devices. . . because there is not one.
He gives seminars to the FBI and other gov't security agencies on cyber security, has testified over 100 times in federal court on IP/IT cases. He gets called when the cases are huge and major liability and money is at stake. He is a colleague and personal friend with Major General Dale Meyerrose, the author of the military standards for security still being used today.
He has multiple patents in technology, invented a new technology platform (patent granted in December 2014), works heavily in regulated industries with his secure technology platform.
As for vibration hacking, he says that phone accelerometers are used and 4GS phones make this easier. It is a mechanical process. There is a training and attack phase to the process.
If Apple doesn't have a back door, you're right, that's great.
Btw, I'm not paranoid...yes I am, no I'm not, yes I am, not I'm not... ;o)
So, tell me, how is he going to get his software on the iPhones 4gs (sic)—there is no such iPhone, Paco, the last iPhone with a gs designation was the iPhone 3gs —in the first place to activate the accelerometers to send or receive such data? To do that, you first have to have access to the iPhone, which means you don't need the hack in the first place!
As one of the articles on accelerometer hacks for tracking says:
Of course, to do this hackers would need to figure out a way to remotely access the accelerometer and access its data. The most likely way would be to have users unknowingly download a malicious app that would then tap into the phone's sensor. When successfully done, it's difficult to detect if someone has hacked into an accelerometer — although one can usually tell by a heightened battery drain.
The phones they are invariably talking about are Android phones or jailbroken iPhones. . . not unjailbroken iPhones.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.