Skip to comments.
New privilege escalation exploit discovered in OS X Yosemite, also affects just-released 10.10.5
Apple Insider ^
| August 16, 2015
| By Sam Oliver
Posted on 08/16/2015 10:01:46 PM PDT by Swordmaker
Just days after patching the DYLD_PRINT_TO_FILE vulnerability with a new OS X point release, Apple's desktop operating system has been hit with yet another zero-day exploit that would allow an attacker to gain root access without using a password.
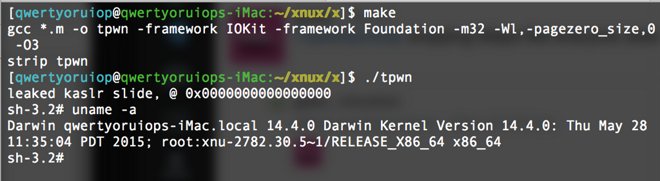
Luca Todesco on Twitter
The exploit was discovered by Italian developer Luca Todesco, who relies on a combination of attacks — including a null pointer dereference in OS X's IOKit — to drop a proof-of-concept payload into a root shell. It affects every version of OS X Yosemite, but seems to have been mitigated in OS X El Capitan, which is nearing release.
Todesco did not disclose the problem to Apple before sharing it publicly early Sunday, so it remains to be seen how quickly the company will respond.
Many computer security researchers condemn such reckless action, arguing that companies should be given time to issue patches for bugs that could harm consumers, while others have become frustrated at the slow pace of response. Apple has a somewhat checkered past with OS X security updates, but has shown improvement in recent months — the company patched the DYLD vulnerability less than a month after disclosure.
Apple has also taken steps to harden its operating system against attacks, announcing that OS X El Capitan would ship with a new security feature called "rootless." Rootless is designed to restrict third-party applications from modifying certain parts of the system — even if they are running as root — in a manner similar to the more aggressive sandboxing in iOS.
TOPICS: Business/Economy; Computers/Internet
KEYWORDS: apple; applepinglist; ios; osx; osxelcapitan; osxyosemite
To: ~Kim4VRWC's~; 1234; Abundy; Action-America; acoulterfan; AFreeBird; Airwinger; Aliska; altair; ...
A new Zero Day vulnerability and EXPLOIT allows user escalation on SOME OS X Macs was announced Sunday Morning without notifying Apple in advance by an Italian developer—who should have his developers' permits pulled for that little demonstration of asshattery! However, as I said, and have researched, it only affects a very small sub-set of OS X Macs, those which have had the Developers' Kit installed, because for it to work it has to invoke "a null pointer de-reference in OS X's IOKit — to drop a proof-of-concept payload into a root shell. . ."
However, this IOKit, which is part of the Developers' Kit is not installed on the average users' OS X Mac. I did a complete search for the relevant file on my Mac and it was not found. I have not installed the Developers' Kit or XTools. Ergo, it cannot work on the average Mac.
That does not absolve him of his egregious behavior in releasing his find into the wild prior to giving the publisher time to correct the problem which is the industry practice. — PING!

Apple OS X ZERO DAY Security
Ping!
If you want on or off the Mac Ping List, Freepmail me.
2
posted on
08/16/2015 10:11:22 PM PDT
by
Swordmaker
( This tag line is a Microsoft insult free zone... but if the insults to Mac users continue...)
To: All
Of course the developers who tested the proof of concept code found it worked on their machines . . . but they had Xcode and the Developers' Kit installed on their Macs they tested it on. You also need to run it on as a user. . . So the worst that could happen is that you download a Trojan File with this script appended. . . and be persuaded through social engineering to install and run it. As always, OS X recognizes and warns users through Gatekeeper about all known Trojans and variants before download, installation, and running any of them.
Surf safely. . .
3
posted on
08/16/2015 10:16:57 PM PDT
by
Swordmaker
( This tag line is a Microsoft insult free zone... but if the insults to Mac users continue...)
To: Swordmaker
“Italian developer Luca Todesco...” Brilliant guy.
4
posted on
08/16/2015 10:18:12 PM PDT
by
Falconspeed
("Keep your fears to yourself, but share your courage with others." Robert Louis Stevenson (1850-94))
To: Swordmaker
It should be noted that Apple quietly updates their own anti-malware program inside MacOS X to fix this problem. They’ve done this multiple times to fix known MacOS X vulnerabilities.
5
posted on
08/16/2015 10:43:37 PM PDT
by
RayChuang88
(FairTax: America's economic cure)
Disclaimer:
Opinions posted on Free Republic are those of the individual
posters and do not necessarily represent the opinion of Free Republic or its
management. All materials posted herein are protected by copyright law and the
exemption for fair use of copyrighted works.
FreeRepublic.com is powered by software copyright 2000-2008 John Robinson


