
Posted on 11/09/2017 10:44:10 AM PST by mojito
....On April 29, 2016, when the DNC became aware its servers had been penetrated, an emergency meeting was held between the Chairwoman of the DNC, Debbie Wasserman-Schultz, DNC’s Chief Executive, Amy Dacey, the DNC’s Technology Director, Andrew Brown, and Michael Sussman, a lawyer for Perkins Coie, a Washington, DC law firm that represented the DNC. Sussman took control of the meeting, setting out the DNC’s agenda when it came to dealing with the cyber attack on its server. The three most important questions, Sussman declared, were what data was accessed, how was it done, and how can it be stopped? The one question Sussman, a former federal prosecutor who focused on computer crimes, did not ask was, who did it?
It took the DNC four days to decide to bring in an outside vendor to investigate the breach of its servers. In the end, it was Sussman who made the call to...CrowdStrike. The call was made on May 4; by May 5 CrowdStrike had installed its FalconHost software that had triggered the Russian attribution.
[....]
For more than 30 days CrowdStrike had exclusive control over the DNC server. During this time, CrowdStrike made an attribution of Russian involvement that has been shown to be fundamentally flawed, and oversaw the transfer of politically sensitive documents, some of which may have been tainted by CrowdStrike’s own actions, to parties who subsequently leaked this material in a politically impactful manner....The data that would shed important light into the most significant claims of Russian involvement in the 2016 US Presidential election...remains out of the hands of those conducting the investigation.
It is difficult to avoid the conclusion that CrowdStrike, by irresponsibly and deliberately attributing the DNC cyber attack to Russia, is involved in deception on a scale that is hard to measure.
(Excerpt) Read more at medium.com ...
Wasn’t there something about Scott Ritter and pictures with underage girls, or inviting girls to meet him at Dairy Queen or something?
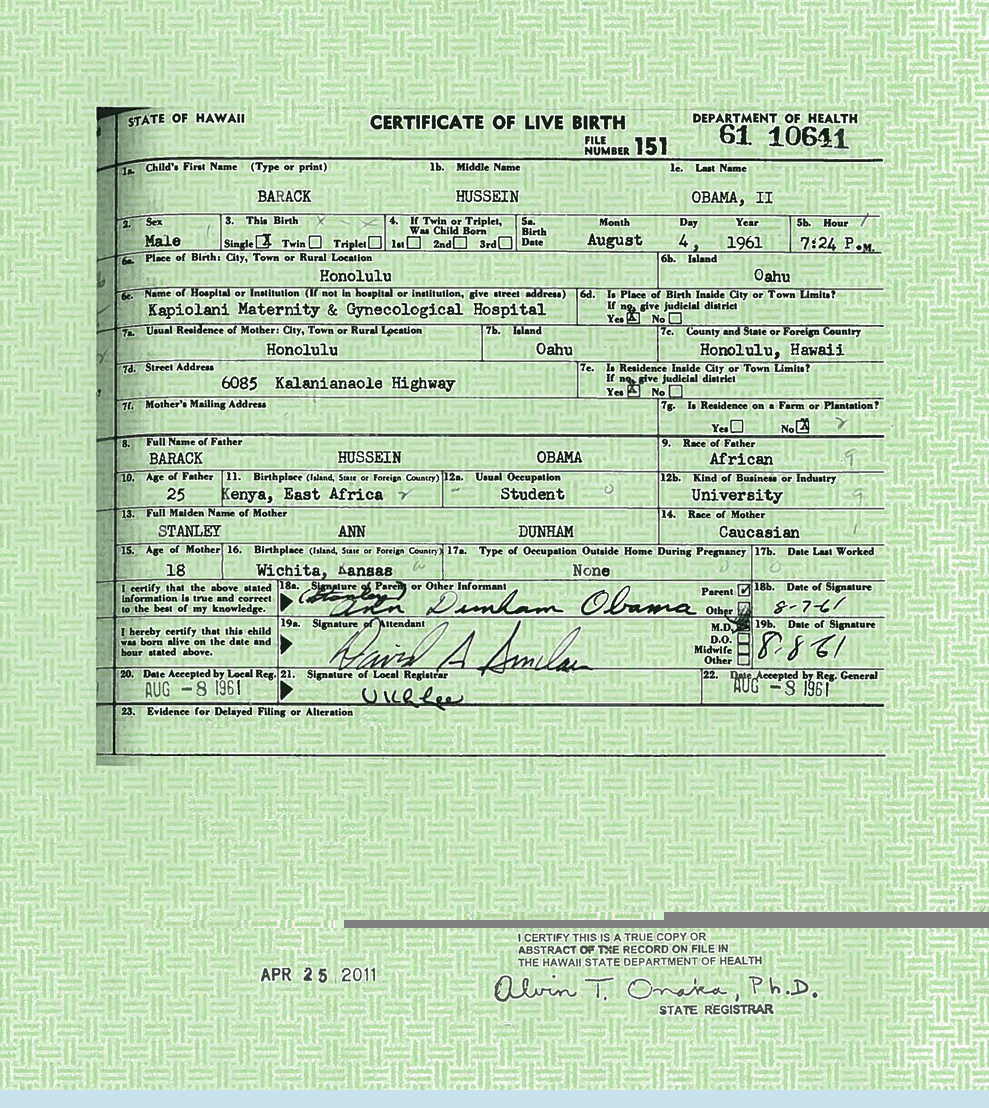
I’m trying to figure out why the word Kansas would be subjected to two different typewriters? Were they trying to cover the fact that the original birthplace was Wichita, Kanada? Whoever made this startling typewriter revelation is working with impaired cognitive skills or is paranoid which also implies the former. This is the sort of conspiracy revelation which earns the caption “Tin Foil Hat” and does a disservice to actual conspiracy research which does not draw inferences from the realm of the demented.
Did Ritter ever get involved with North Korean nukes?
The Burger King where Scott Ritter arranged to meet an underage girl is about 2 miles from my house. His arrest was a big story locally, but hardly touched by the mainstream media as Ritter was, then, a hero to the left.
It was written off by some as possibly entrapment.
Here’s the thing, later he performed a lewd act in his house while on a web cam with a minor on the other end. He was again charged. Again, it was big news locally, I messaged here about it back then -but again it wasn’t covered by the mainstream media.
I have NO doubt Scott Ritter is a pedofile.
Bookmark
Very informative read. I have always been suspect of the Russian hacking conclusion based on the work of 1 entity. That coupled the DNC refusal of the FBI performing their own investigation tainted the narrative even more.
“At first the DNC tried to get the FBI to make the attribution call, figuring that it would garner more attention coming from the US government. But when the FBI wanted full access to the DNC server so that it could conduct a full forensic investigation, the DNC balked.”
Gee, I wonder why they would balk at federal investigation if they were really the target of foreign espionage?
Very interesting material. Ritter’s report is well done, even if heavily reliant on what rival cyber experts say about each other.
Some questions in my mind: How did the DNC become aware of the intrusion in April that triggered the rest? Who/what/when/how might be revealing. I’m sure they say some junior IT person stumbled across it. Yeah right.
How do we know that CrowdStrike wasn’t in on this from the start? Alperowitch, according to Ritter, is a big advocate of entering computers and taking files, in “self-defense”. Surprise! Cozybear and Fancybear entered the DNC’s computers and stole files. CrowdStrike’s magic software detected it all in moments. As your Item 1 suggests, perhaps they then extracted and promulgated the files themselves for a variety of motives. Unleashing a craze over cyber security, and getting massive free publicity couldn’t have been too bad for business. Has anyone noticed that Alperowitch’s vaunted concept of chasing down stolen files and zapping them seems either not to have been deployed or a complete failure?
Is there a common ingredient between the DNC and DCCC? Yes — Debbie Wasserman Schultz, who is known to be a major client of the Awan ring of Pakistani IT crooks. Mebbie the target was Debbie? Or was she just conveniently inept?
He also inexplicably did a 180 and started claiming that Iraq had no WMD whatever, that it had all been destroyed by Clintons sporadic air strikes on Iraq, which he did whenever he needed a public distraction from his personal problems. He also was caught in flagrant delicto with a 13-year-old girl. Why has he suddenly taken a go at journalism. Does he think credibility scabs over and heals with time? Even so, the article is probably truthful.
And somehow all the intelligence agencies were in agreement that it was them Russkies what dood it, without ever seeing the server. CrowdStrike is so credible as all that?
Ukraine has a rep of being the native country of a lot of professional assassins.


Scott Ritter correctly called the lack of real intel about WMD in Iraq
You can test this by pasting the BC into a Powerpoint page and drawing a vertical line and moving it across the page. You will see a huge number of differences, because the forger, when he/she pasted the contents of each block into each of the form's blocks, they didn't know anything about typewriter character alignment.
Likewise, if you draw a horizontal line and shift it up and down the form, fitting it to underline the text, you will see that they don't line up either. HOWEVER, any old-time typist will tell you that by pushing the "unlock roller" button, you can make micro-adjustments to the character line placement vertically. BUT YOU CAN'T MAKE MICRO ADJUSTMENTS TO THE CHARACTERS HORIZONTALLY.
Your example is too obscure. The elephant in the room is the vertical alignment of the characters.
I remember the Albany am station, which I can hear in Rochester was all over this.
Isn’t Ritter the pedo who picked up kids at his local McDonald’s?
You might be unaware, but a guy/gal named BUCKHEAD got famous and got Dan Rather the negative attention he deserved because whoever did Dan's forgery for him didn't realize that Texas National Guard in W's Guard days didn't have any proportionally-spaced typewriters. (That's probably way too subtle for you, Scooter100, but it literally and directly cost Danno his job because people realized the incontroverible facts behind BUCKHEAD's observation. The same is true with my evidence here, though I chose to post something that hadn't yet been posted elsewhere, not just to repeat the things so many others have already posted on the subject. (What you've posted has been seen elsewhere by many posters.))
When honest, knowledgeable researchers risk their lives and livelihoods to bring their fellow citizens evidence of honest-to-goodness document alteration, it behooves such fellow citizens not to go off half cocked with all that there attempted pejorization.
Knowlegeable, professional types (not of a mind to defend the Deep State perpetrators of these events) have examined the evidence I have accumulated and have uniformly said it appears to have uniquely captured the false characteristics of what happened--lots of lying, a fraud on the citizenry, militarized propaganda for election-related purposes and a hoax.
I've been in aviation over 40 years, being President or CEO of several highly successful aviation companies. The evidence I have amassed regarding the airplane crash that netted the top associate and family of the one of the prime perpetrators of this birth certificate scam, got the response from an FAA Chief Scientist that I should be teaching a course within the FAA regarding accident investigation. A former NTSB Investigator in Charge concurred.
I haven't stuck my neck out beyond what substantive evidence shows.
The excerpted document (Need I say, it?:) of course would not have been subjected to two typewriters in real life, but since you apparently missed it, it is therefore evidence of alteration of the document, which, by Hawaii Statute, means the document is invalid, no matter who might have forged the alteration. This type of alteration would have necessarily been the product of a computer-based "Photoshopping," which is another dimension of fraud, since computers that could do such electronic editing certainly weren't sold in the computer or office marketplace in 1961.
This is about evidence. The black-on-light-blue source image there is the highest resolution image available, likely in all respects identical to what Judith Corley sent over after receiving it from Loretta Fuddy.
The fact that the evidence shows (along with lots of other supporting evidence) two different type fonts on two letters in an obscure place on the birth certificate gives an indication that someone involved with the forgery was participating under duress. That person would likely know that if it ever became known that he or she performed that criminal act, said person would be in lots of trouble.
It would be a reasonable strategy to leave a figurative breadcrumb or two in said document as indicator of wanting the person who ordered the crime to be caught and the worker's duress to be known, such that he or she would not be adjudged a willing accomplice. It would be reasonable that might be taken into consideration by a prosecutor or jury.
You're probably quite aware that your use of the term "conspiracy research" was a set-up created within the CIA to ridicule those with evidence that makes it clear the government has been complicit in illegal ventures. Of course that plays right along with the politics of personal destruction you're trying to seed here, but it won't work. You're just showing people here that you've made your choice to be on the wrong side of things.
He may have been somewhat privy indirectly through the interactions between Iraq-Syria-NK.
He has commented on Nork nukes back in August, blaming the entire problem of their nukes on the US but offering his idea of a solution. Here: http://www.theamericanconservative.com/articles/resolving-north-korea-without-fire-and-fury/
that’s what always made me wonder if that was the reason he never reported the children’s prison until years later when the cat was out of the bag after the US liberated it [why would Iraq have let him see it except perhaps to try to honey trap him?]
When reading Ritter it makes more sense to read him as if he’s an agent of Russia... because he functions that way for all practical purposes. He’s quite the Russian apologist.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.