Posted on 08/27/2024 4:58:51 AM PDT by ShadowAce
Microsoft is known for their signature, “my way or the highway” approach when it comes to their offerings, with the Windows operating system being the most prominent one among those.
Many in the FOSS community disagree with that approach, with a strong rejection of such practices, suggesting people go for more open options for their operating systems and applications, and I agree with them.
Unfortunately, that same approach has now affected many Linux distribution users, who were sent scampering searching for a fix to a problem caused by a Windows update (who would've expected that?).
 Source: paku1234
Source: paku1234First spotted by Ars Technica, a monthly Windows update pushed on August 13 that included a fix to a two-year-old vulnerability, CVE-2022-2601, with an 8.6 CVSS severity rating, caused dual-boot systems with Windows and Linux distros to not boot.
That fix was meant to tackle an issue with the GRUB bootloader, which allowed malicious actors from carrying out-of-bound writes, and possibly bypass secure boot.
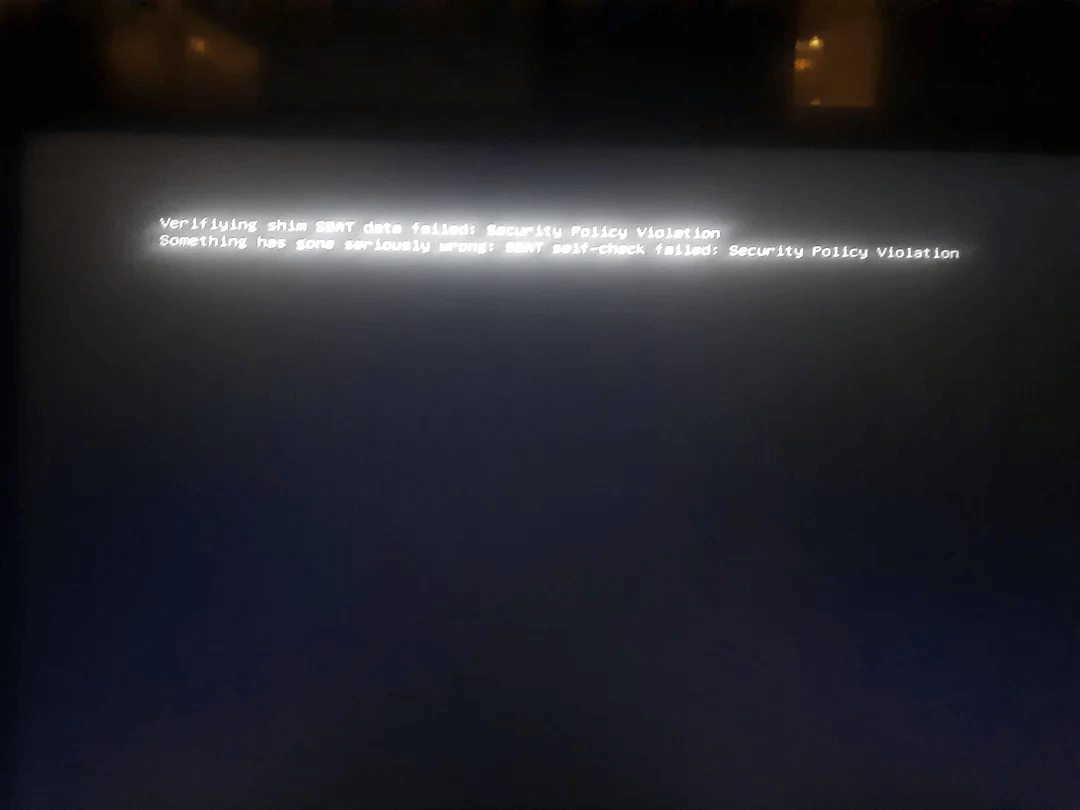
But, it caused some collateral damage in the process. After updating, many users, including users of Ventoy, and Ubuntu 24.04, reported that they were shown the following error:
Verifying shim SBAT data failed: Security Policy Violation
Something has gone seriously wrong: SBAT self-check failed: Security Policy Violation
This update installed an SBAT, which is an acronym for Secure Boot Advanced Targeting, a Linux-focused method for discarding various components in the boot path using generation numbers embedded into the EFI binaries. (apologies for the jargon)
However, this mechanism was meant to run with devices only running Windows, and, according to Microsoft, this should not have caused any issues on dual-boot systems, at least on newer Linus distributions.
But, as we know already, it did. 😑
Following these revelations, in a statement, Microsoft mentioned that they were aware of “some secondary boot scenarios are causing issues for some customers”, and that they were working with their Linux partners to investigate and address the issue.
Thankfully, the community has come to the rescue, with manutheeng, a member of the Linux Mint forums, finding a solution for Ubuntu in an old post on the Ubuntu forums.
sudo mokutil --set-sbat-policy delete
The above steps should also work with any Ubuntu-based Linux distribution. If that doesn't work, then you might be facing what a Framework laptop user faced.
If dual-boot systems were more common, then this issue would've been treated with more haste, like the CrowdStrike incident that took place last month, but that was not Microsoft's fault.
So, it's better than nothing. 🙂
Ultimately, there's still the matter of Secure Boot being an absolute mess, that has left many people questioning whether this could've been implemented in a better way.
I think that it could've, the PC industry rushed its implementation before it was ready.
Meh. I have a dual boot sytem. Linux Mint 17 or Linux Mint 21. Tossed Winders 10 years ago.
“DOS isn’t done until Lotus won’t run.”
Old saying from early PC days, 40ish years ago.
Some distros are in virtual box and others stand alone on hand me down boxes.
Anything that is labelled “advanced targeting” is not an accident. Yeah, targeting from MS. It offensive not defensive security. This was intentional and violates antitrust.
They think folks are stupid. And that arrogance and deceptive practice is why I told them to take a hike years ago.
I am so glad I still have W7
I have dual boot but windows is not allowed to connect to the web, therefor, not allowed to get updates. It’s a fresh win 7 pro install that is several years old.
I thought it was standard practice to just disable secure boot before installing Linux anyhow?
If my memory is right all the instructions going way back have said to do this first?
Same here.
Runs a couple of CD rom games I play once in a while.
I like the built in chess game that I can almost never beat.
My laptop is too old to have secure boot in the bios so I don’t have any experience with that.
I think I remember having trouble booting from a Linux USB with even the old legacy bios. I had to go turn secure boot off before it would allow me. But it probably depends on the make.
Won’t break my dual boot- windows 7 which i use only in offline mode for windows only programs and games.
This is like a car manufacturer disabling your car because you took it to an independent shop instead of their dealer shop.
How many people would actually put up with that arrogant concept and practice? Apparently a LOT. Because they just keep doing it.
This is like a car manufacturer disabling your car because you took it to an independent shop instead of their dealer shop.
How many people would actually put up with that arrogant concept and practice? Apparently a LOT. Because they just keep doing it.
At this point in my life there are only a handful of use cases for me to run Windows directly on hardware. I don’t play games but that would be one of them. As the author pointed out, Secure Boot is a mess from the ground up and it’s only on locked-down corporate windows workstations where it makes sense. Most hobbyists, developers, and dev-ops folks who using linux on a day-to-day basis aren’t dual-booting and likely have disabled secure boot already.
I recently replaced my laptop and immediately replaced the hard drive with a larger model and installed Linux. The first thing I disabled in the BIOS was the Secure Boot functionality.
My 2 laptops are duel boot Manjaro Linux and Windows 11 but my desktop has a hard drive hot swap bay and and an OS on each hard drive that I swap out as I need them ,LOL
Windows ain’t done till Linux don’t run?
Me too.
This scenario puts the “duel” in “duel boot”!
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.