Skip to comments.
Mac, Windows QuickTime Flaw Opens 'Month Of Apple Bugs'
Information Week ^
| Jan 2, 2007 03:04 PM
| Gregg Keizer
Posted on 01/03/2007 11:04:31 AM PST by newgeezer
The exploit could be used by attackers to compromise, hijack, or infect computers running either Windows or Mac OS X.
The Month of Apple Bugs project kicked off Monday by posting a zero-day vulnerability in Apple's QuickTime media player. It also posted an exploit that could be used by attackers to compromise, hijack, or infect computers running either Windows or Mac OS X.
The Month of Apple Bugs (MoAB), which will announce a new security vulnerability in Apple's operating system or other Mac OS X software each day in January, is a follow-on to November's "Month of Kernel Bugs" campaign, and is co-hosted by that project's poster, a hacker who goes by the initials "LMH," and a partner, Kevin Finisterre, a researcher who has posted numerous Mac vulnerabilities and analyses on his own site.
The debut vulnerability is in QuickTime 7's parsing of RTSP (RealTime Streaming Protocol); the protocol is used to transmit streaming audio, video, and 3-D animation over the Web. Users duped into clicking on an overlong rtsp:// link could find their PCs or Macs compromised. It also may be possible to automatically trigger an attack simply by enticing users to a malicious Web site.
"Exploitation of this issue is trivial," said LMH in the vulnerability's write-up on the MoAB Web site. The associated exploit code has been tested on Mac OS X running on Intel-based systems, and works against QuickTime 7.1.3, the current version of the player, LMH and Finisterre said.
Other security researchers rang alarms Tuesday. Danish vulnerability tracker Secunia, for example, pegged the bug as "highly critical," the second-from-the-top threat in its five-step score, and Symantec alerted customers of its DeepSight threat network of the vulnerability.
An Apple spokesman declined to confirm the vulnerability, or, if it was legitimate, when the flaw might be fixed. In an e-mail, he said that "Apple takes security very seriously and has a great track record of addressing potential vulnerabilities before they can affect users. We always welcome feedback on how to improve security on the Mac."
LMH, who didn't immediately reply to several questions sent via e-mail, said on the MoAB site that Apple's Mac OS X operating system was chosen as the target for the month of vulnerabilities because "we like to play with OS X, we enjoy hate e-mail, and it's not as crowded as (random software vendor), yet. Thus, it's really comfortable for research and there's so much to be worked out."
He also said that Apple -- and other vendors whose Mac OS X applications might be the focus of a bug posted during the month's run -- would not be notified in most cases before the information went live, and dismissed that practice. "The point is releasing them without vendor notification. The problem with so-called 'responsible disclosure' is that for some people, it means keeping others on hold for insane amounts of time, even when the fix should be trivial. And the reward (automated responses and euphemism-heavy advisories) doesn't pay off in the end."
LMH, Finisterre, and commercial security vendors recommended that users cripple QuickTime's ability to process rtsp:// links. In Windows, launch QuickTime, select Edit|Preferences|QuickTime Preferences, click the File Types tab, expand Streaming, and clear the box marked "RTSP stream descriptor." In Mac OS X, select System Preferences|QuickTime|Advanced|MIME Settings|Streaming|Streaming Movies and clear the "RTSP stream descriptor" box.
Apple's QuickTime was last in the news during December, when a bug in the player was exploited by fraudsters on MySpace. That vulnerability remains unpatched.
LMH expects to see more QuickTime attacks now that his newest flaw has gone public. He said, "It's a matter of time to see this getting abused in the wild."
TOPICS:
KEYWORDS: apple; bugs; moab; security; threadjester
Navigation: use the links below to view more comments.
first previous 1-20 ... 261-280, 281-300, 301-320 ... 541-557 next last
To: for-q-clinton
I bet the truth lies someone in between both of your's and ge's description I've provided the links, while all he has done is repeatedly lie. And you should know by now it's not going to stop.
To: antiRepublicrat
he dug his own hole from there. LMAO, so says the guy who has been busted for lying for months. For what purpose? His defense of foreign hackers who were ripping Apple's OSX. And he's been lying ever since.
To: N3WBI3
I was not there and I am completely ignorant around the origins of nMap Perfect proof of his ridiculous lie, he was frantically trying anything he could come up with to glorify Russian hackers, and the best he could do was claim an American was a Russian hacker then continue lying about it for months.
To: antiRepublicrat
Just putting down his lies is becoming a full time job. ROFL, you already tried to claim I had lied on this thread, when all it has turned out to be is more lies from you and your normal endless defense of radical leftists and hackers.
To: Golden Eagle
Me not hearing of someone does not mean they are not famous in hacker or security circles.
285
posted on
01/08/2007 6:16:41 PM PST
by
N3WBI3
("Help me out here guys: What do you do with someone who wont put up or shut up?" - N3WBI3)
To: N3WBI3
Me not hearing of someone does not mean they are not famous in hacker or security circles. I know, but that is his excuse for his lie, that we should have known. Perfecty demonstrates how ridiculous not only his original lie was, but his supposed excuse for making it in the first place.
To: Golden Eagle
Someone who is a security expert should have know the orgin of the most used tools..
287
posted on
01/08/2007 6:29:36 PM PST
by
N3WBI3
("Help me out here guys: What do you do with someone who wont put up or shut up?" - N3WBI3)
To: N3WBI3
Go back to the original thread, he didn't even identify "nmap", he went way out on a limb claiming a Russian Hacker created some tool used the DoD, the obvious purpose so he could defend the Russian hackers in that thread, when in fact it was an American. He's too low for words to describe, a Russian hacker loving sellout is a start.
To: Golden Eagle
ROFL, you already tried to claim I had lied on this thread You claimed you "exposed" my test. First lie. I told you in that Clinton thread you linked to.
You claimed my continuation of the test was in defense of Russian hackers. Second lie.
You claimed my excuse for the test was then in defense of "Green Party leftist Richard Stalllman." Third lie.
You said that I was trying to make excuses for Russian hackers. Wow, partially true in that I do not believe copyright should be able to extend into abuses of established law. However, I did successfully defeat your unsupported claim that they were criminal using actual law, and you then used personal attacks to avoid admitting you were wrong. And you repeated that unsupported claim in this thread. Fourth lie.
Also in your quotes of what I posted, you eliminated the context, especially eliminated the exclamation marks that show I was being sarcastic. Mischaracterization of another FReeper's post = fifth lie.
I can't believe I actually once defended you having a philosophical approach to purchases.
To: for-q-clinton
I keep waiting for masses to switch to Apple so they stop picking on Windows OS. I never understood those that use Mac and have a good thing saying "come on over here". I'd rather swim with fewer peeing in the pool but have to use Microsoft for specialized business software requirements requiring security devices.
Everyone else - Go Apple!
To: antiRepublicrat
I told you in that Clinton thread you linked to. LMAO! YET ANOTHER LIE! This guy is unbelievable in how he refuses to quit lying, all in the defense of leftists and foreign hackers.
I linked it because you claimed he was Russian, here is your exact quote, when you came to the defense of you leftist buddy FLAMING DEATH who was stuck trying to claim a Russian wrote Multics, antoher ridiculous lie from you Russian hacker loving sellouts:
Nmap is included in the distro, and we all know that was written by a Russian hacker.
That is YOUR quote. That was the first time it was mentioned in that thread. And you were still claiming he was Russian, just like you had in other threads, for months.
To: antiRepublicrat
You claimed my continuation of the test was in defense of Russian hackers. Second lie. Second lie of yours, not mine. In your last post! You were there on the Clinton thread defending FLAMING DEATH's claim a Russian wrote Multics, which of course is a lie as well, I just linked the thread again above so you can quit lying now. I think that guy is actually an American citizen too, you pathetic traitors is dispicable, if you're even Americans to begin with.
To: Golden Eagle
traitors ARE dispicable These slimeballs talk in so many circles they even mix me up.
Gold Eagle Out.
To: Golden Eagle; N3WBI3
I know, but that is his excuse for his lie, that we should have known. Perfecty demonstrates how ridiculous not only his original lie was, but his supposed excuse for making it in the first place. My thoughts exactly. And I tried to say that but in a more verbose and confusing analogy. The fact that one doesn't know of nmap's origins and the nationality of their creators is just silly. The fact that one doesn't know who specifically wrote a tool is meaningless. And to be honest if Miss Information, Shadow, Hal, N3wbi3, GE claimed it was written by a specific person--I would take them at face value (well that is until now). Miss Information will be ignored/posted to the link of his lie(s). And if I feel like it I'd look up to see if he's lying again, but that's a bit too much work to just have a discussion/debate in a what is supposed to be a conservative forum. So most likely he won't get a response as that would require either already knowing what he says is true or false or confirming it by researching.
294
posted on
01/08/2007 9:24:49 PM PST
by
for-q-clinton
(If at first you don't succeed keep on sucking until you do succeed)
To: N3WBI3
Someone who is a security expert should have know the orgin of the most used tools.. I call BS on that. I do project management but I don't know who was the pioneer in that field. Does that mean I don't know project management or can't be considered an expert?
I also do a lot of programming I know what/who Ada is but does that make me an expert programmer? although I don't know who created fortran.
295
posted on
01/08/2007 9:27:12 PM PST
by
for-q-clinton
(If at first you don't succeed keep on sucking until you do succeed)
To: antiRepublicrat
You claimed you "exposed" my test. First lie. I told you in that Clinton thread you linked to. You claimed my continuation of the test was in defense of Russian hackers. Second lie.
You claimed my excuse for the test was then in defense of "Green Party leftist Richard Stalllman." Third lie.
See the problem with you admitting to lying is we don't know when you're lying or telling the truth. You never should have lied for months on end to try to score a point because now no one (except your closest brethren) can believe you.
296
posted on
01/08/2007 9:31:14 PM PST
by
for-q-clinton
(If at first you don't succeed keep on sucking until you do succeed)
To: for-q-clinton
I call BS on that. I do project management but I don't know who was the pioneer in that field. Does that mean I don't know project management or can't be considered an expert? Do you know the top, most famous, currently used project management tools? Nmap is the network security equivalent.
As I told GE when giving him hints to solve my test (yes, I did help him, gave him the tools to find the truth), the author's name, "Fyodor," is so popular it actually shows #1 in Google, ahead of the famous Russian author Fyodor Dostoyevsky. Do you know what it takes to get to #1 in unpaid Google ahead of such a famous name? A Google for "network scanner" also has nmap on the third site hit, #2 if you're looking for a free one, #1 if you're looking for an open source one.
Here are some basic facts you can confirm with anyone in the field:
- Almost anybody in UNIX who knows security knows about nmap, and GE claims both UNIX and security knowledge.
- If you don't use UNIX but otherwise run network security, you know nmap because it's one of the most popular tools hackers use to scan a potential target network. It's also a fairly popular tool to scan your own network to find potential vulnerabilities.
- If you just generally know about hackers (as GE claims to know), then you should know one of the most famous white-hat hackers in the world, Fyodor.
Simply put, if GE had been telling the truth about his qualifications, my little test would have fallen flat on its face in the beginning.
The military (which GE supposedly works for) DEFINITELY knows nmap. It's in the information assurance literature that all people in GE's supposed position should read (some of it is required reading for everyone in such a position). But is AR lying? Do you think I may be lying? Does the government really know about nmap? A picture is worth a thousand words:

Lt. Gen. Keith B. Alexander, director of the National Security Agency, and William Marshall, another NSA official, give President Bush a tour of the super-secret agency's headquarters in Fort Meade, Md. Photo Credit: By Evan Vucci -- Associated Press
You can even use nmap as a plug-in to the #1 tool on that list, Nessus, although the Nessus plug-in architecture makes that undesirable. Now Nessus suggests you run nmap and pump the results into Nessus. Of course, I can back that claim up.
Trivia: Nmap even had a scene in Matrix Reloaded, being properly used (a rarity in Hollywood computer depictions) to take advantage of an actual known SSH vulnerability.
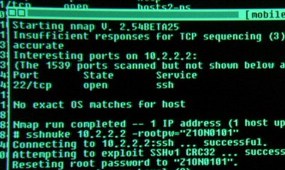
Now you have proper context of the issue.
To: Golden Eagle; for-q-clinton
Me: I told you in that Clinton thread you linked to.
You: LMAO! YET ANOTHER LIE!
Proof. Your response was to blow it off.
Don't claim you knew, because in a later post you say "Now you're claiming he's American, who knows,". You did not know whether to believe he was American or Russian, which means you did not know.
Basic logical concept here: If you did not know he was American, you could not have caught me on it.
Also notice your purposeful attempt at distortion by taking things out of context. I'll go slowly so you can't weasel:
You quote me: "Nmap is included in the distro, and we all know that was written by a Russian hacker"
You say "That was the first time it was mentioned in that thread. And you were still claiming he was Russian."
Timeline:
I revealed my test at post #113.
I revealed that he was American in post #120.
rzeznikj at stout also revealed he was American in post #130.
Your quote above from me was at #229.
The timeline shows two lies from you:
- "That was the first time it was mentioned in that thread" -- lie, mentioned at least in 113, 120 and 130 before you quote me at 229.
- "And you were still claiming he was Russian" -- lie, I stopped claiming he was Russian in 113, and revealed he was American in 120.
So we see you being dishonest, taking things out of context, saying I was trying to deceive when in context it was merely a joke on you. For reference, the full post, in the context of you saying on another thread "
...Ubuntu Linux, developed by a foreigner with ties to the Russian space program":
I'm still trying to understand how Ubuntu can have Russian influences just because the guy who funds the project rode a Russian rocket to get to his vacation on the International Space Station. The Tin Thrush needs to realize that Ubuntu's founder is just a very rich businessman and venture capitalist -- Ubuntu is his way of philanthropy (as opposed to giving money to Planned Parenthood). Oh wait, I know how it has Russian influences! Nmap is included in the distro, and we all know that was written by a Russian hacker.
Remember, stated AFTER I informed you he was American. The dripping, blatantly obvious sarcasm was because of your ridiculous statement that equates to one having Norwegian "ties" if one takes a cruise to the Bahamas.
for-q-clinton, you now see what we deal with. Don't believe me, merely look up the cited posts. I hotlinked them for your convenience. What you see that makes you believe GE is in the right only appears so in the out-of-context settings that GE tries to create.
To: antiRepublicrat
Once again knowing a tool and knowing who wrote the tools are two COMPLETELY DIFFERENT concepts. One is practical for security experts the other is trivia for Trivial Pursuit IT edition.
299
posted on
01/09/2007 11:35:00 AM PST
by
for-q-clinton
(If at first you don't succeed keep on sucking until you do succeed)
To: for-q-clinton
Once again knowing a tool and knowing who wrote the tools are two COMPLETELY DIFFERENT concepts. Don't forget that he also presents himself as a hacker expert. He showed no indication of knowing about either the tool or its author despite his claims of working in a position that pretty much requires that he know about at least the tool.
Navigation: use the links below to view more comments.
first previous 1-20 ... 261-280, 281-300, 301-320 ... 541-557 next last
Disclaimer:
Opinions posted on Free Republic are those of the individual
posters and do not necessarily represent the opinion of Free Republic or its
management. All materials posted herein are protected by copyright law and the
exemption for fair use of copyrighted works.
FreeRepublic.com is powered by software copyright 2000-2008 John Robinson


