Do you know the top, most famous, currently used project management tools? Nmap is the network security equivalent.
As I told GE when giving him hints to solve my test (yes, I did help him, gave him the tools to find the truth), the author's name, "Fyodor," is so popular it actually shows #1 in Google, ahead of the famous Russian author Fyodor Dostoyevsky. Do you know what it takes to get to #1 in unpaid Google ahead of such a famous name? A Google for "network scanner" also has nmap on the third site hit, #2 if you're looking for a free one, #1 if you're looking for an open source one.
Here are some basic facts you can confirm with anyone in the field:
- Almost anybody in UNIX who knows security knows about nmap, and GE claims both UNIX and security knowledge.
- If you don't use UNIX but otherwise run network security, you know nmap because it's one of the most popular tools hackers use to scan a potential target network. It's also a fairly popular tool to scan your own network to find potential vulnerabilities.
- If you just generally know about hackers (as GE claims to know), then you should know one of the most famous white-hat hackers in the world, Fyodor.
The military (which GE supposedly works for) DEFINITELY knows nmap. It's in the information assurance literature that all people in GE's supposed position should read (some of it is required reading for everyone in such a position). But is AR lying? Do you think I may be lying? Does the government really know about nmap? A picture is worth a thousand words:

Lt. Gen. Keith B. Alexander, director of the National Security Agency, and William Marshall, another NSA official, give President Bush a tour of the super-secret agency's headquarters in Fort Meade, Md. Photo Credit: By Evan Vucci -- Associated Press
You can even use nmap as a plug-in to the #1 tool on that list, Nessus, although the Nessus plug-in architecture makes that undesirable. Now Nessus suggests you run nmap and pump the results into Nessus. Of course, I can back that claim up.
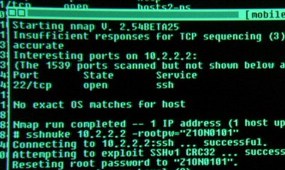
Trivia: Nmap even had a scene in Matrix Reloaded, being properly used (a rarity in Hollywood computer depictions) to take advantage of an actual known SSH vulnerability.
Now you have proper context of the issue.