Skip to comments.
Beware! Undetectable CrossRAT malware targets Windows, MacOS, and Linux systems
The Hacker News ^
| 1/25/18
| Mohit Kumar
Posted on 01/27/2018 5:47:41 AM PST by markomalley
Are you using Linux or Mac OS? If you think your system is not prone to viruses, then you should read this.
Wide-range of cybercriminals are now using a new piece of 'undetectable' spying malware that targets Windows, macOS, Solaris and Linux systems.
Just last week we
published a detailed article on the report from EFF/Lookout that revealed a new advanced persistent threat (APT) group, called
Dark Caracal, engaged in global mobile espionage campaigns.
Although the report revealed about the group's successful large-scale hacking operations against mobile phones rather than computers, it also shed light on a new piece of cross-platform malware called
CrossRAT (version 0.1), which is believed to be developed by, or for, the Dark Caracal group.
CrossRAT is a cross-platform remote access Trojan that can target all four popular desktop operating systems, Windows, Solaris, Linux, and macOS, enabling remote attackers to manipulate the file system, take screenshots, run arbitrary executables, and gain persistence on the infected systems.
According to researchers, Dark Caracal hackers do not rely on any "zero-day exploits" to distribute its malware; instead, it uses basic social engineering via posts on Facebook groups and WhatsApp messages, encouraging users to visit hackers-controlled fake websites and download malicious applications.
CrossRAT is written in Java programming language, making it easy for reverse engineers and researchers to decompile it.
Since at the time of writing only two out of 58 popular antivirus solutions (according to
VirusTotal) can detect CrossRAT, ex-NSA hacker
Patrick Wardle decided to analyse the malware and provide a comprehensive
technical overview including its persistence mechanism, command and control communication as well as its capabilities.
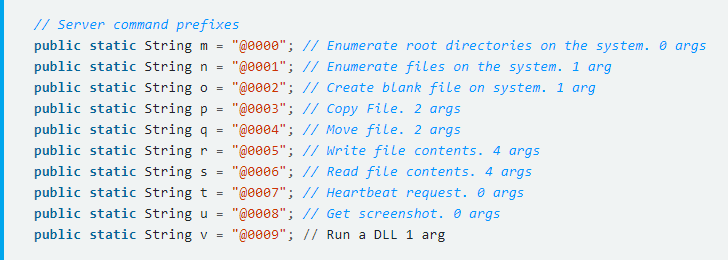
CrossRAT 0.1 — Cross-Platform Persistent Surveillance Malware
Once executed on the targeted system, the implant (
hmar6.jar) first checks the operating system it's running on and then installs itself accordingly.
Besides this, the CrossRAT implant also attempts to gather information about the infected system, including the installed OS version, kernel build and architecture.
Moreover, for Linux systems, the malware also attempts to query systemd files to determine its distribution, like Arch Linux, Centos, Debian, Kali Linux, Fedora, and Linux Mint, among many more.
CrossRAT then implements OS specific persistence mechanisms to automatically (re)executes whenever the infected system is rebooted and register itself to the C&C server, allowing remote attackers to send command and exfiltrate data.
As reported by Lookout researchers, CrossRAT variant distributed by Dark Caracal hacking group connects to '
flexberry(dot)com' on port 2223, whose information is hardcoded in the 'crossrat/k.class' file.
CrossRAT Includes Inactive Keylogger Module
The malware has been designed with some basic surveillance capabilities, which get triggered only when received respective predefined commands from the C&C server.
Interestingly, Patrick noticed that the CrossRAT has also been programmed to use '
jnativehook,' an open-source Java library to listen to keyboard and mouse events, but the malware does not have any predefined command to activate this keylogger.
"However, I didn’t see any code within that implant that referenced the jnativehook package—so at this point it appears that this functionality is not leveraged? There may be a good explanation for this. As noted in the report, the malware identifies it’s version as 0.1, perhaps indicating it’s still a work in progress and thus not feature complete," Patrick said.
How to Check If You're Infected with CrossRAT?
Since CrossRAT persists in an OS-specific manner, detecting the malware will depend on what operating system you are running.
For Windows:
- Check the 'HKCU\Software\Microsoft\Windows\CurrentVersion\Run\' registry key.
- If infected it will contain a command that includes, java, -jar and mediamgrs.jar.
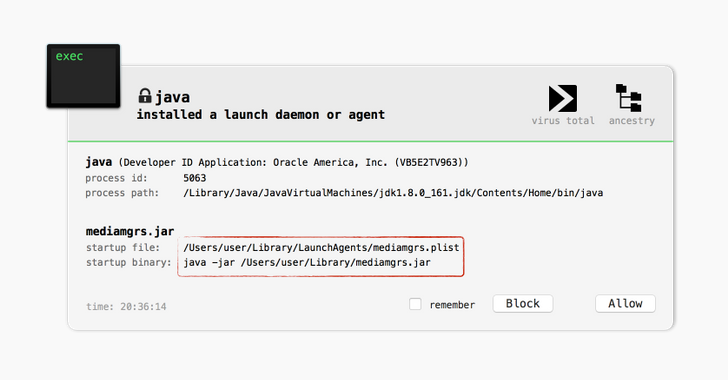
For macOS:
- Check for jar file, mediamgrs.jar, in ~/Library.
- Also look for launch agent in /Library/LaunchAgents or ~/Library/LaunchAgents named mediamgrs.plist.
For Linux:
- Check for jar file, mediamgrs.jar, in /usr/var.
- Also look for an 'autostart' file in the ~/.config/autostart likely named mediamgrs.desktop.
How to Protect Against CrossRAT Trojan?
Only 2 out of 58 antivirus products detect CrossRAT at the time of writing, which means that your AV would hardly protect you from this threat.
"As CrossRAT is written in Java, it requires Java to be installed. Luckily recent versions of macOS do not ship with Java," Patrick said.
"Thus, most macOS users should be safe! Of course, if a Mac user already has Java installed, or the attacker is able to coerce a naive user to install Java first, CrossRAT will run just dandy, even on the latest version of macOS (High Sierra)."
Users are advised to install behaviour-based threat detection software. Mac users can use
BlockBlock, a simple utility developed by Patrick that alerts users whenever anything is persistently installed.
TOPICS: Computers/Internet
KEYWORDS:
In other words, this is a Trojan Horse software that is a Java exploit. Since Java is inherently cross-platform, then there you go...
As an update, the current list of Antivirus software that can detect this malware is:

While I know one of the key features of Linux is that it is less subject to being infected by malware than Windows, it is still very prudent to run an antivirus scanner in the background. The best one I have personally found is Sophos. (You'll notice that in the case of this Trojan, Sophos has already deployed a patch, while the other two popular Linux AVs (ClamAV and Avast) haven't been patched yet)
To: markomalley
“According to researchers, Dark Caracal hackers do not rely on any “zero-day exploits” to distribute its malware; instead, it uses basic social engineering via posts on Facebook groups and WhatsApp messages, encouraging users to visit hackers-controlled fake websites and download malicious applications.”
So if you are on Linux, you have to download it and then type in your root password to allow it to install. What kind of experienced system administrator would do that?
To: proxy_user
So if you are on Linux, you have to download it and then type in your root password to allow it to install. What kind of experienced system administrator would do that? Obviously very few.
How many home users would do that?
You know the answer as well as I do.
3
posted on
01/27/2018 5:57:22 AM PST
by
markomalley
(Nothing emboldens the wicked so greatly as the lack of courage on the part of the good -- Leo XIII)
To: markomalley
It is undetectable yet 2 antivirus programs can find it. There are also ways to manually find it. Not very undetectable now is it?
Who writes this crap?
4
posted on
01/27/2018 5:57:33 AM PST
by
Bitman
To: sauropod
5
posted on
01/27/2018 6:14:54 AM PST
by
sauropod
(I am His and He is mine.)
To: markomalley
Dark Caracal hackers should be systematically hunted down and literally exterminated like the cockroaches they are.
6
posted on
01/27/2018 6:27:12 AM PST
by
lgjhn23
(It's easy to be liberal when you're dumber than a box of rocks.)
To: markomalley
The jar won’t get written to /usr/var unless the user is running the browser as root, or some sudo variation I would think. I can’t imaine an informed Linux user operating that way, but I suppose there might be some one .
7
posted on
01/27/2018 6:43:38 AM PST
by
gcraig
(Freedom is not free)
To: markomalley
While this malware is Java-based, using things like Java and Flash on web pages are rapidly disappearing due to the HTML 5.0 standard, which was finalized in October 2014.
8
posted on
01/27/2018 6:57:44 AM PST
by
RayChuang88
(FairTax: America's Economic Cure)
To: gcraig
I can’t imaine an informed Linux user operating that way, but I suppose there might be some one . The operative word is "informed." I can imagine plenty of "uniformed" users who would do just that.
9
posted on
01/27/2018 7:04:49 AM PST
by
markomalley
(Nothing emboldens the wicked so greatly as the lack of courage on the part of the good -- Leo XIII)
To: markomalley
CrossRAT malware....has a RINO ring to it.
To: RayChuang88
While this malware is Java-based, using things like Java and Flash on web pages are rapidly disappearing due to the HTML 5.0 standard, which was finalized in October 2014.
java and flash are known bad actors, and anyone still using them is asking for it.
11
posted on
01/27/2018 9:13:44 AM PST
by
867V309
(Lock Her Up)
To: Swordmaker
Heads up!
What do you have on this one?
12
posted on
01/27/2018 9:40:10 AM PST
by
TXnMA
("Allah": Satan's current alias | "Islamists": Satan's assassins | "Moderate Muslims": Useful idiots.)
To: Swordmaker
Simplest check appears to be for
"mediamgrs.plist" in
~/Library/LaunchAgents...
(Mine only has a single file; an additional one would "stick out like a sore thumb"...)
13
posted on
01/27/2018 10:12:30 AM PST
by
TXnMA
("Allah": Satan's current alias | "Islamists": Satan's assassins | "Moderate Muslims": Useful idiots.)
To: markomalley
“As CrossRAT is written in Java, it requires Java to be installed.
...
I haven’t used Java or Flash in years.
14
posted on
01/27/2018 10:17:15 AM PST
by
Moonman62
(Make America Great Again!)
To: markomalley; ~Kim4VRWC's~; 1234; 5thGenTexan; AbolishCSEU; Abundy; Action-America; acoulterfan; ...
This so-called cross platform Trojan that affects macOS, really isn't and is not a worry for 99% of Mac users. Why? Because Java is not installed on macOS by default UNLESS the macOS user opts to use it for a specific piece of software they are running that requires it. It requires the user to actually go and get JAVA and download It, install it, and only then will they be susceptible to this Trojan. . . and THEN, if they are directed by this Facebook website to download an app, macOS WILL warn them they are downloading a Trojan. It will also warn them after they've been stupid enough to ignore and give permission to go ahead and download the Trojan that they are now INSTALLING said Trojan, and then it will warn them AGAIN before it will allow them to RUN said Trojan before it can be run. Each time that warning alert comes up, before they can continue the industrial strength stupid user MUST enter an administrator's user name and password to continue to BE stupid. So this is not much of a problem on a Mac. Other OS users out there, be careful. — PING!

1% of Apple macOS Users
With Java Installed Malware Warning
All Other Mac Users, Don't Worry
Ping!
The latest Apple/Mac/iOS Pings can be found by searching Keyword "ApplePingList" on FreeRepublic's Search.
If you want on or off the Mac Ping List, Freepmail me
15
posted on
01/27/2018 10:29:43 AM PST
by
Swordmaker
(My pistol self-identifies as an iPad, so you must accept it in gun-free zones, you racist, bigot!)
To: TXnMA
Heads up!
What do you have on this one? Thanks for the heads up. . . but it's really not a problem. Apple has not shipped a Mac with JAVA installed since OS X.6 Snow Leopard. OS X.7.2 Lion came with Java on the disk, but all versions of OS X.7.3 and after one had to actually go to the JAVA site and download it to get Java. Apple had determined that Java was a source of too many malware infections to continue to ship it with OS X by default, especially with it enabled.
The only Mac users who may be at risk of these Trojans are those still using OS X.6 Snow Leopard and old who are willing to download and install sketchy applications that someone inveigles them into for social reasons from somewhere other than Apple or other trusted sites. . . or who have install Java because some other piece of software (rare) requires it. (unfortunately, medical / dental software that runs in my office DOES requires it, so it is installed in a few computers in my office. However, my employees do not know the administrator password to install software)
16
posted on
01/27/2018 10:43:08 AM PST
by
Swordmaker
(My pistol self-identifies as an iPad, so you must accept it in gun-free zones, you racist, bigot!)
To: Swordmaker
17
posted on
01/27/2018 1:18:18 PM PST
by
conservatism_IS_compassion
(Presses can be 'associated,' or presses can be independent. Demand independent presses.)
To: Swordmaker
Thanks for the input. 😀😆
18
posted on
01/27/2018 3:36:41 PM PST
by
Mark17
(Genesis chapter 1 verse 1. In the beginning GOD....And the rest, as they say, is HIS-story)
Disclaimer:
Opinions posted on Free Republic are those of the individual
posters and do not necessarily represent the opinion of Free Republic or its
management. All materials posted herein are protected by copyright law and the
exemption for fair use of copyrighted works.
FreeRepublic.com is powered by software copyright 2000-2008 John Robinson