Posted on 05/16/2003 10:12:25 AM PDT by Fractal Trader
The average American moviegoer taking in the Matrix Reloaded this weekend will likely be wowed by the elaborate action sequences and dazzling special effects. But hackers who've seen the blockbuster are crediting it with a more subtle cinematic milestone: it's the first major motion picture to accurately portray a hack.
That's right: Trinity uses a 'sploit.
A scene about two thirds of the way through the film finds Carrie-Anne Moss's leather-clad superhacker setting her sights on a power grid computer, for plot reasons better left unrevealed.
But at exactly the point where audiences would normally be treated to a brightly-colored graphical cartoon of a computer intrusion, ala the 2001 Travolta vehicle Swordfish, or cheer as the protagonist skillfully summons a Web browser and fights valiantly through "404 Errors," like the malnourished cyberpunk in this year's "The Core," something completely different happens: Trinity runs "Nmap."
Probably the most widely-used freeware hacking tool, the real-life Nmap is a sophisticated port scanner that sends packets to a machine -- or a network of machines -- in an attempt to determine what services are running. An Nmap port scan is a common prelude to an intrusion attempt -- a way of casing the joint, to find out if any vulnerable service are running.
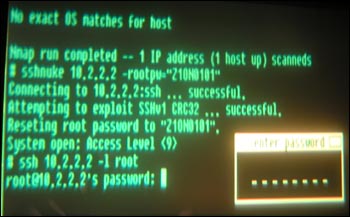
That's exactly how the fictional Trinity uses it. In a sequence that flashes on screen for a few scant seconds, the green phosphor text of Trinity's computer clearly shows Nmap being run against the IP address 10.2.2.2, and finding an open port number 22, correctly identified as the SSH service used to log into computers remotely.
"I was definitely pretty excited when I saw it," says "Fyodor," the 25-year-old author of Nmap. "I think compared to previous movies that had any kind of hacking content, you could generally assume it's going to be some kind of stupid 3D graphics show."
But the unexpected nod to hackerdom doesn't end there. Responding to the Nmap output , Trinity summons a program called "sshnuke" which begins "[a]ttempting to exploit SSHv1 CRC32."
Discovered in February, 2001 by security analyst Michal Zalewski, the SSH CRC-32 bug is a very real buffer overflow in a chunk of code designed to guard against cryptographic attacks on SSH version one. Properly exploited, it grants full remote access to the vulnerable machine.
"I think there are at least two public exploits in circulation right now," said Zalewski, in a telephone interview. "They just got released about a month after the advisory. And I know there are some that are not public."
The actual program Trinity uses is fictitious -- there no "sshnuke," yet, and genuine exploits sensibly drop the user directly into a root shell, while the big screen version forces the hacker to change the system's root password -- in this case to "Z1ON1010." (Note the numeral in the place of the 'I' -- more hax0r style.)
But then, the film does take place hundreds of years in the future. Is Zelewski surprised to see unpatched SSH servers running in the year AD 2800? "It's not that uncommon for people to run the old distribution," he says. "I know we had a bunch of boxes that were unpatched for two years."
Fyodor notes that the filmmakers changed the text of Nmap's output slightly "to make it fit on the screen better," but he's not quibbling over the details. The white hat hacker's stardom even gave him new appreciation for the speed of the Internet's underground. After seeing the film late Wednesday night, Fyodor put out a request to an Nmap mailing list asking for someone to get him a digital still of the program's three-seconds of fame. He expected it to take hours, or days.
"Twenty minutes after I send it, I'm getting a bunch of screens shots, some of them have suspicious Windows Media Player outlines to them," he says. "Now I've got screen shots, Divx copies of the movie, all sorts of stuff." If the Matrix borrows from real life, the Internet, it seems, already has the Matrix.
Well I guess that shatters my image of War Games.
/ tin foil on
WANT TO PLAY A GAME?
Indeed. I'd kind of like to see his cross-compiler, myself. Or maybe it was a script - anyone know if aliens use VB or Outlook?
Kind of like all phone numbers in movies and TV shows start 555 (there no public phone number that start with that)

Is this real, or is it a game?
What is the difference?
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.