Posted on 11/18/2018 3:57:10 AM PST by vannrox

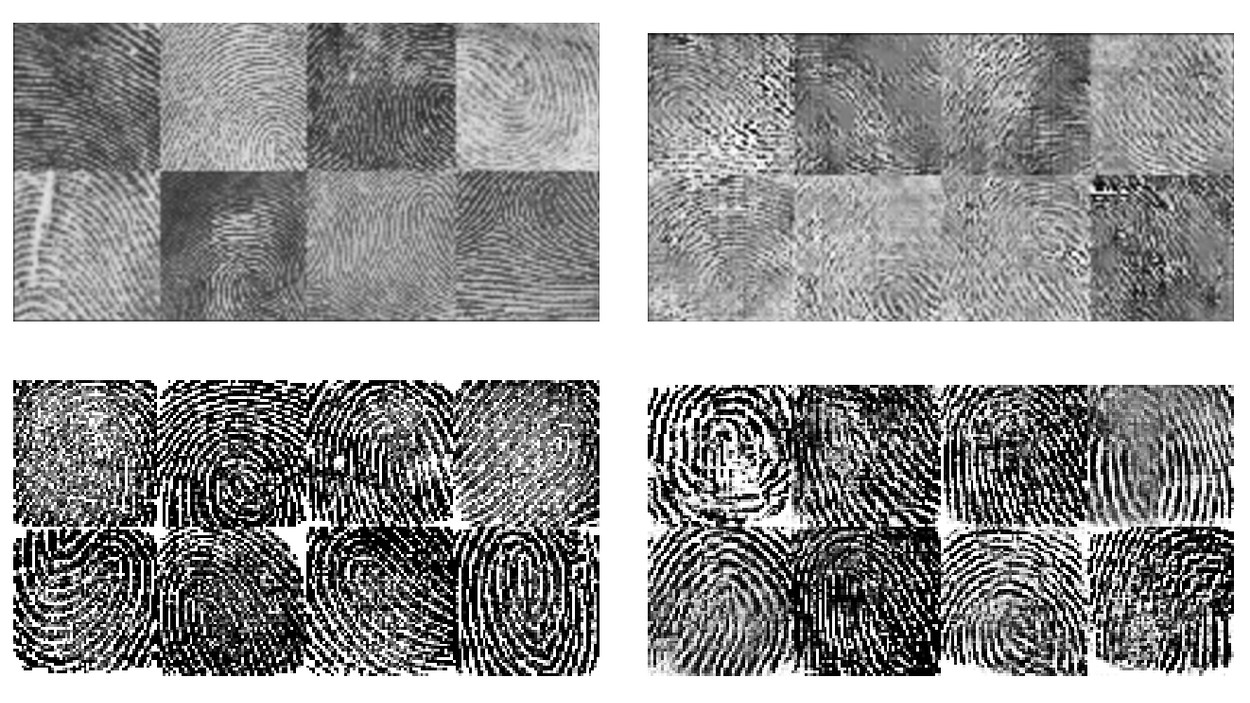
Researchers at NYU and U Michigan have published a paper explaining how they used a pair of machine-learning systems to develop a "universal fingerprint" that can fool the lowest-security fingerprint sensors 76% of the time (it is less effective against higher-security sensors).
The researchers used "generative adversarial networks" (GAN) to develop their attack: this technique uses a pair of machine learning systems, a "generator" which tries to fool a "discriminator," to produce a kind of dialectical back-and-forth in that creates fakes that are harder and harder to detect.
The output was a fake fingerprint designed to attack the capacitive sensors in smartphones and other devices; these sensors work from partial prints that can be rotated out of their original orientation and still unlock the device, and are thus the easiest to fool.
Smartphones generally operate at the second tier of security, in which they are expected to generate false positives 0.1% of the time; and at this level, the researchers were able to spoof the sensors 22% of the time.
Recent research has demonstrated the vulnerability of fingerprint recognition systems to dictionary attacks based on MasterPrints. MasterPrints are real or synthetic fingerprints that can fortuitously match with a large number of fingerprints thereby undermining the security afforded by fingerprint systems. Previous work by Roy et al. generated synthetic MasterPrints at the feature-level. In this work we generate complete image-level MasterPrints known as DeepMasterPrints, whose attack accuracy is found to be much superior than that of previous methods. The proposed method, referred to as Latent Variable Evolution, is based on training a Generative Adversarial Network on a set of real fingerprint images. Stochastic search in the form of the Covariance Matrix Adaptation Evolution Strategy is then used to search for latent input variables to the generator network that can maximize the number of impostor matches as assessed by a fingerprint recognizer. Experiments convey the efficacy of the proposed method in generating DeepMasterPrints. The underlying method is likely to have broad applications in fingerprint security as well as fingerprint synthesis.
DeepMasterPrints: Generating MasterPrints for Dictionary Attacks via Latent Variable Evolution [Philip Bontrager, Aditi Roy, Julian Togelius, Nasir Memon and Arun Ross/Arxiv]
Researchers Created Fake 'Master' Fingerprints to Unlock Smartphones [Daniel Oberhaus/Motherboard]
bkmk
my phone has an iris sensor...

At no point in history has any government ever wanted its people to be defenseless for any good reason ~ nully's son
Nut-job Conspiracy Theory Ping!
To get onto The Nut-job Conspiracy Theory Ping List you must threaten to report me to the Mods if I don't add you to the list...

Simple solution.
Don’t store any critical data on your smart device.
I have a little flip phone that I call my *dumb phone*.
All I use it for is calls and texting.
Huh. There are people I know who are appalled and dismayed to learn I don’t have such places as Facebook on my phone. Nor will I. Ever. No twitter, no FB, no snapchat, no passwords. Ever.
I can be in the world and not of it.
...not Of It.
I like it.
Ah well. Now the govt can’t complain about not being able to unlock your phone
I don’t like this idea. Why don’t require an anal probe to open your Smartphone? If we allow stuff like this it’s going to get more and more invasive.
The subcutaneous scanner was defeated a long time ago. It remains to be seen whether GAN generated fingerprints can do the trick tho. OTOH GAN based ad-tech is manipulating millions of people into engagement with clickbait every hour so I wouldn’t bet against it influencing you to act against your own best interests someday soon, heheh....
:o]
Its a good thing to remember!
The TouchID has a false ID rate of one in 100,000. That doesn’t happen if it could be spoofed by lifting fingerprints from any source.
No-s, I posted this claim on FR back in September 2013 when the first crowing, hyped claims came out in Ars Technica about how easy it was to spoof Apple’s TouchID. . . and I also posted the quick retractions which were quickly reported explaining why the original hype was completely bogus. . . so. . .
No, the subcutaneous scanner wasn’t defeated a long time ago. That article was roundly criticized. The German Chaos Computer Club hacker, Starbug’s, so-called defeat hack was totally unreproduceable as a general defeat because they really did not hack it. What they instead proved was that only the owner could unlock an iPhone 5s with TouchID. . . Because it was the Starbug’s own finger that did it.
You cannot use an image of a "lifted" fingerprint to get any data about subcutaneous fat pads. Do you really think that subcutaneous fat pad data can be lifted from a oil impression ". . .fingerprint of the phone user photographed from a glass surface."? It’s impossible, the data is buried too deep for an evanescent oily fingerprint left on glass to show anything about subcutaneous structure buried below the surface. These German hacker guys did not even know WHAT technology Apple was using 48 hours after the TouchID debuted. . . they just got a false positive and rushed to publish their supposed hack.
It worked because the fingerprint they photographed on the glass was from the same finger the German hacker had used to train the iPhone to be unlocked. The same photographed fingerprint would ONLY work when the latex model fingerprint was placed on that originally scanned finger, Starbug’s index finger, the one he used to create the actual lifted fingerprint and which he used to traine the iPhone 5s, and then used to unlock the iPhone, and then only once out of three or four attempts to unlock it with the finger gloved fingerprint. It worked because Starbug’s finger’s fat pads were inside that latex fingerprint glove and matched the map inside the Secure Enclave of iPhone 5s. . . NOT because his fingerprint on the finger glove matched.
It would NOT work with the latex fingerprint "glove" superimposed on any other of the iPhone 6 Starbug’s other nine fingers, or anyone else’s fingers for that matter. It would only intermittently work just on Starbug’s single, already learned index finger when the sensor penetrated deeply enough to read the Starbug’s living fat pads. Why would that be the case? The Germans really did not ask themselves that question. They should have.
Other researchers did ask that question. It turned out that, as pointed out, Starbug was using a scan of his OWN fingerprint over the same finger and the TouchID was reading his subcutaneous fatpads THROUGH the constructed finger glove fingerprint image. . . and correctly reading his own stored TouchID on the device.
Nice try, but that so-called hack was debunked very quickly when no one could replicate as a general hack.
Three years later, in mid-2016, a means was found to spoof the TouchID sensor but it requires about $10,000 of specialized equipment and access to the owners fingers for a couple of minutes to properly scan the fat pads and then build a 3D finger model that simulates a living finger. That does work about one in two tries.
I appreciate the depth of your followup, but you also reference a case where it was cracked. Once cracked, never say never, only difficult. The fact they reproduced the owners finger in the earlier exploit proved it was possible to get access without the owner present, which counts as a successful exploit.
Outstanding intel. A big thank you for your information and contribution.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.