To: TigerLikesRooster
Another CIA tool let loose.
2 posted on
06/28/2017 9:53:38 PM PDT by
jospehm20
To: TigerLikesRooster
A code segment altered for destroying data:
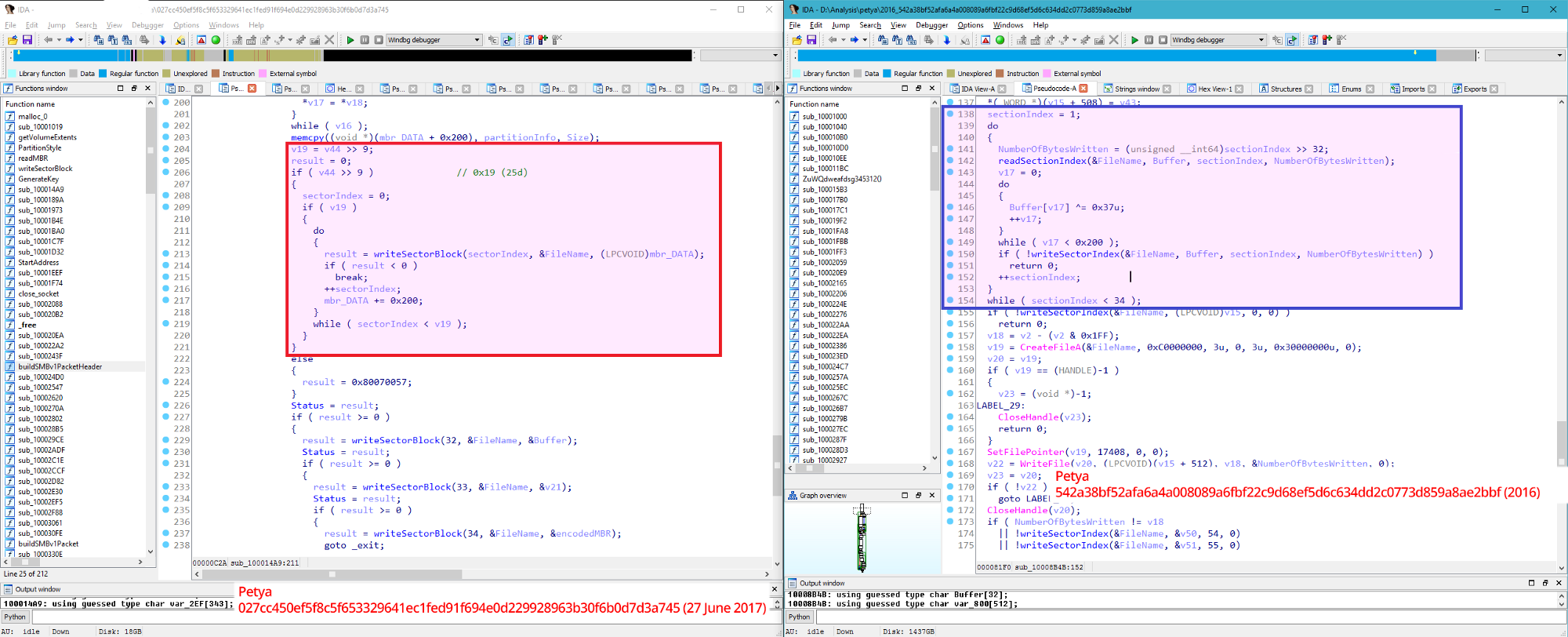
4 posted on
06/28/2017 9:56:49 PM PDT by
TigerLikesRooster
(dead parakeet + lost fishing gear = freep all day)
To: TigerLikesRooster
Could be Russia. Or the US Deep State destroying incriminating evidence of its own crimes, under the cover of worldwide cyber chaos.
5 posted on
06/28/2017 9:56:50 PM PDT by
rfp1234
(DinosorosExtinction)
To: TigerLikesRooster
So, if it destroys the master boot record, use a utility to copy your disks master boot record to file so you can restore it later.
To: TigerLikesRooster
Interesting. Thanks for posting.
15 posted on
06/28/2017 10:34:32 PM PDT by
PGalt
To: TigerLikesRooster
FYI: turn OFF JavaScript, the most evil entity known to computing.
NEVER open email attachments. The info can always be conveyed another way.
Turn OFF HTML when downloading/reading email. This not only disables scripts, it provides privacy by not "phoning home" through embedded images.
NEVER install any application unless you are willing to bet your cyber life/security/privacy and everything else on its source. Installing an application gives the keys of your kingdom to that application. You've been warned.
17 posted on
06/28/2017 10:43:04 PM PDT by
867V309
(Lock Her Up)
To: TigerLikesRooster
Hillary Clinton on line 2....
To: TigerLikesRooster
Can they just target Mueller and his minions?
22 posted on
06/29/2017 12:03:44 AM PDT by
Paladin2
(No spelchk nor wrong word auto substition on mobile dev. Please be intelligent and deal with it....)
To: TigerLikesRooster
24 posted on
06/29/2017 12:13:10 AM PDT by
TChad
To: TigerLikesRooster
From the article:
In almost all other aspects, Tuesday's malware was impressive. It used two exploits developed by and later stolen from the National Security Agency. It combined those exploits with custom code that stole network credentials so the malware could infect fully patched Windows computers. And it was seeded by compromising the update mechanism for M.E.Doc, a tax-filing application that is almost mandatory for companies that do business in Ukraine.
31 posted on
06/29/2017 3:21:04 AM PDT by
dynachrome
(When an empire dies, you are left with vast monuments in front of which peasants squat to defecate)
To: TigerLikesRooster
Clinton Foundation has a lot of cash to help pay for such work around the globe to meet their ends.
38 posted on
06/29/2017 3:52:26 AM PDT by
CincyRichieRich
(We must never shut up. Covfefe: A great dish served piping hot!)
To: TigerLikesRooster
Now referred to as Hillaryware.
41 posted on
06/29/2017 4:12:59 AM PDT by
Lockbox
To: TigerLikesRooster
Anyone who does this should become prime target #1 for the entire planet, and hunted down and summarily executed.
It will teach a lesson for the others.
Anyone who SPOTS a vulnerability and reports it, should get a huge reward.
This completely changes the motivation to find and act on them.
55 posted on
06/29/2017 7:08:45 AM PDT by
Mr. K
(***THERE IS NO CONSEQUENCE OF REPEALING OBAMACARE THAT IS WORSE THAN OBAMACARE ITSELF***)
To: TigerLikesRooster
You cannot destroy data if it has been backed up. If you don’t back it up, you don’t care about it.
60 posted on
06/29/2017 7:31:45 AM PDT by
AppyPappy
(Don't mistake your dorm political discussions with the desires of the nation)
To: TigerLikesRooster
I suspect our own NSA-CIA with one of their cyber-children having been developed by contractors and it “escaped”.
65 posted on
06/29/2017 9:03:56 AM PDT by
Wuli
FreeRepublic.com is powered by software copyright 2000-2008 John Robinson

