Luke Slytalker & The Force

We’ll just get right to the meat& potatoes—I found a thing. Happening currently. Embedded PGP Encryption Key???
Inside of Jeffrey Epstein photos, uploaded by the NYPost.
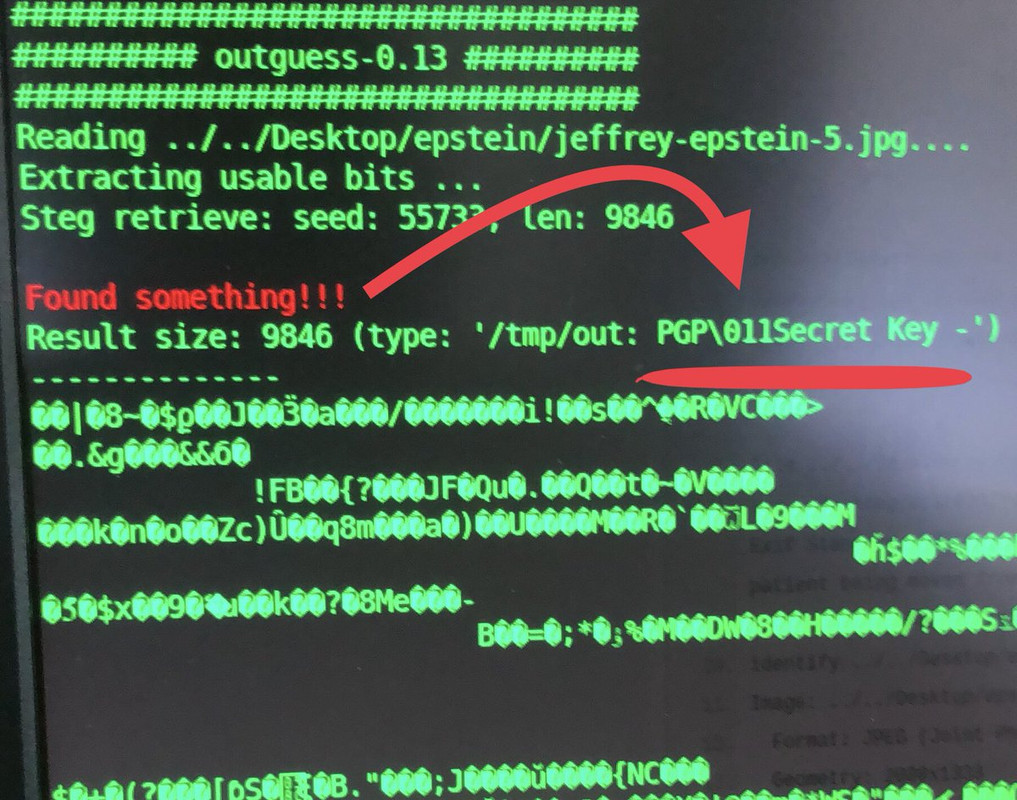
I’ve been sitting on this for a little bit, but when I saw that Jean Luc Brunel has “disappeared” now as well... I guess it’s time to release this.
BTW—was the NY Post the first to break this about Brunel?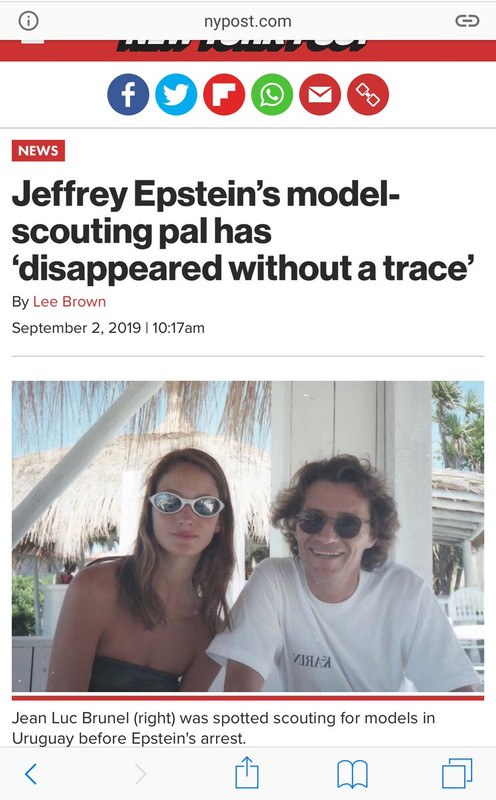

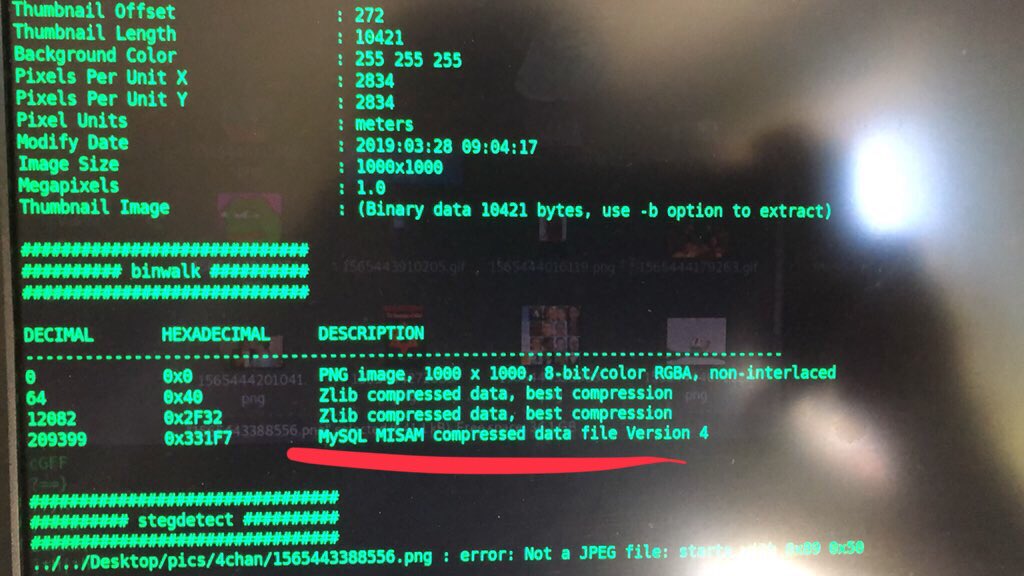
So here’s the backstory— I had ran some Stego scans on the Ghislaine Maxwell photos from the NYPost article about her being spotted at In-n-Out. There was some odd hex seemingly embedded into the file. I’m not used to seeing this, so I looked for other instances I could remember.
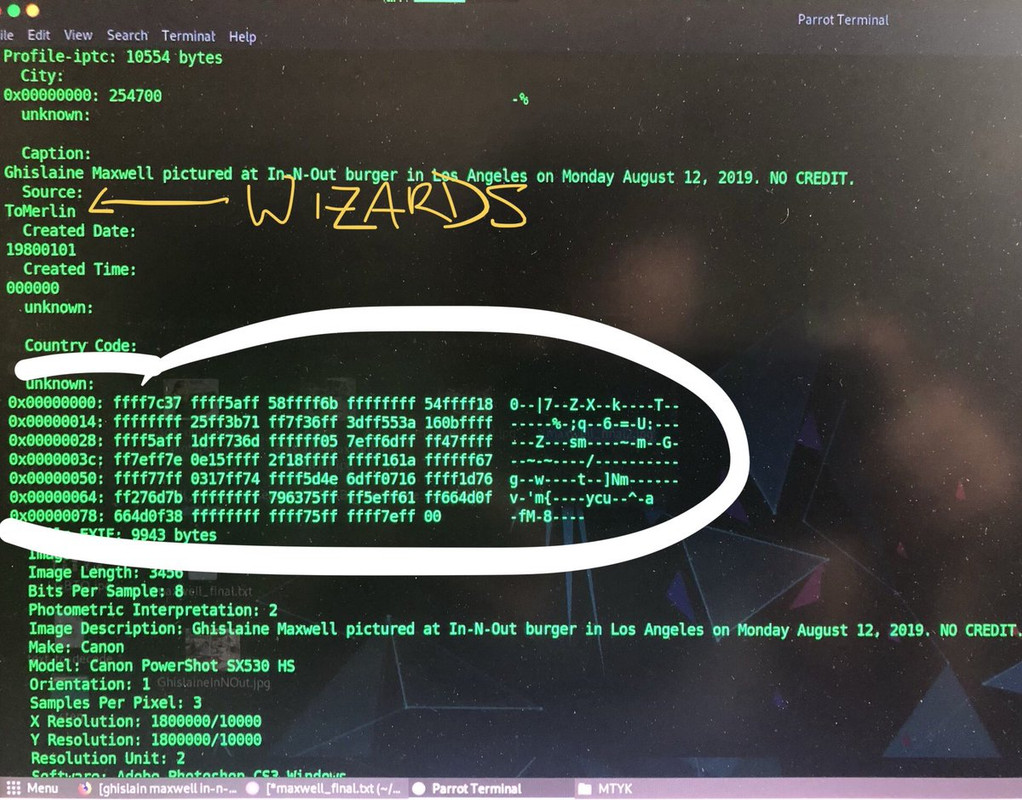
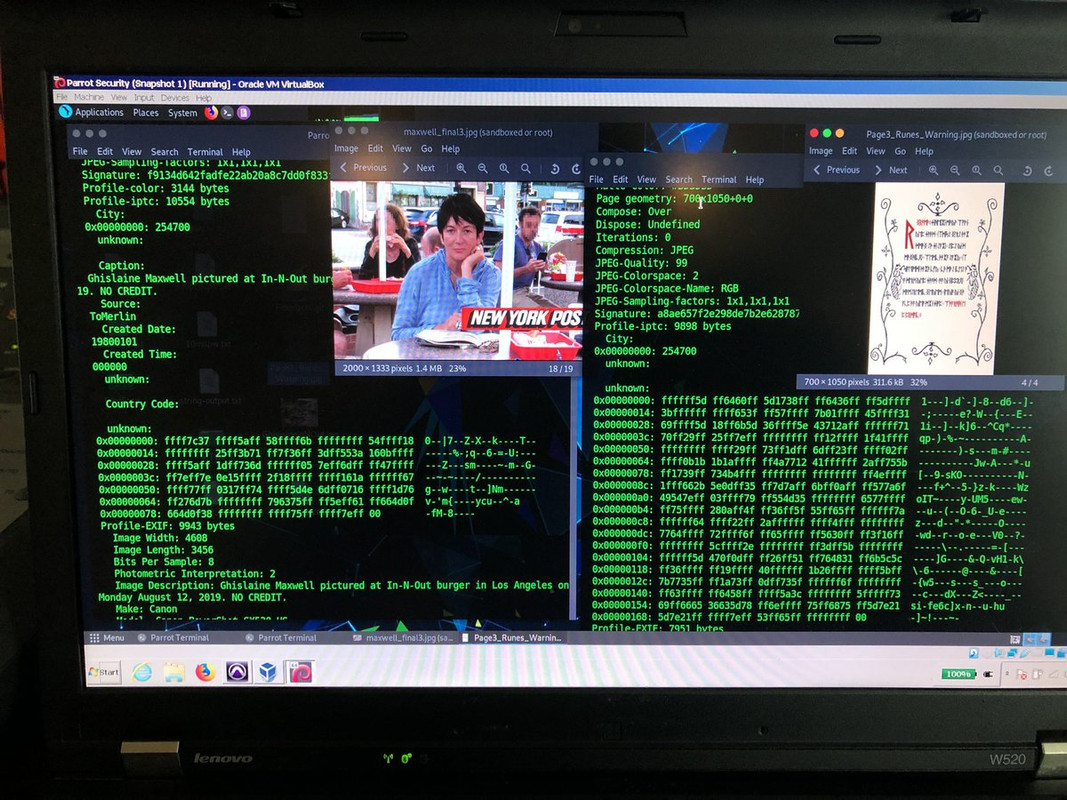
This side-by-side is a scan I ran on the Maxwell pic which I pulled off the NYPost CMS/content management system.
The image on the right half is a picture from the “unsolved” #Cicada3301 Liber Primus puzzle of 2014. You can see a similar set of hex embedded into the Cicada image.
A little bit ago, @csthetruth said I should check out the pics of #Epstein in the Orange color jump suit after his “suicide”. I found that the NYPost hosts their content directly on a Wordpress subdomain (http://thenypost.files.wordpress.com ) and their domain points there.
A little bit ago, @csthetruth said I should check out the pics of #Epstein in the Orange color jump suit after his “suicide”.
I found that the NYPost hosts their content directly on a Wordpress subdomain (https://t.co/fF445qNPcY) and their domain points there.— Luke Slytalker & The Force (@_Luke_Slytalker) September 4, 2019
I scraped all the images I could find with a /Jeffrey-Epstein-*.jpg wildcard and got a ~dozen pics. One thing stood out was multiple copies of the same image. This is unnecessary & a waste of space. Wordpress can auto scale/crop/etc, so multiple versions would be redundant.
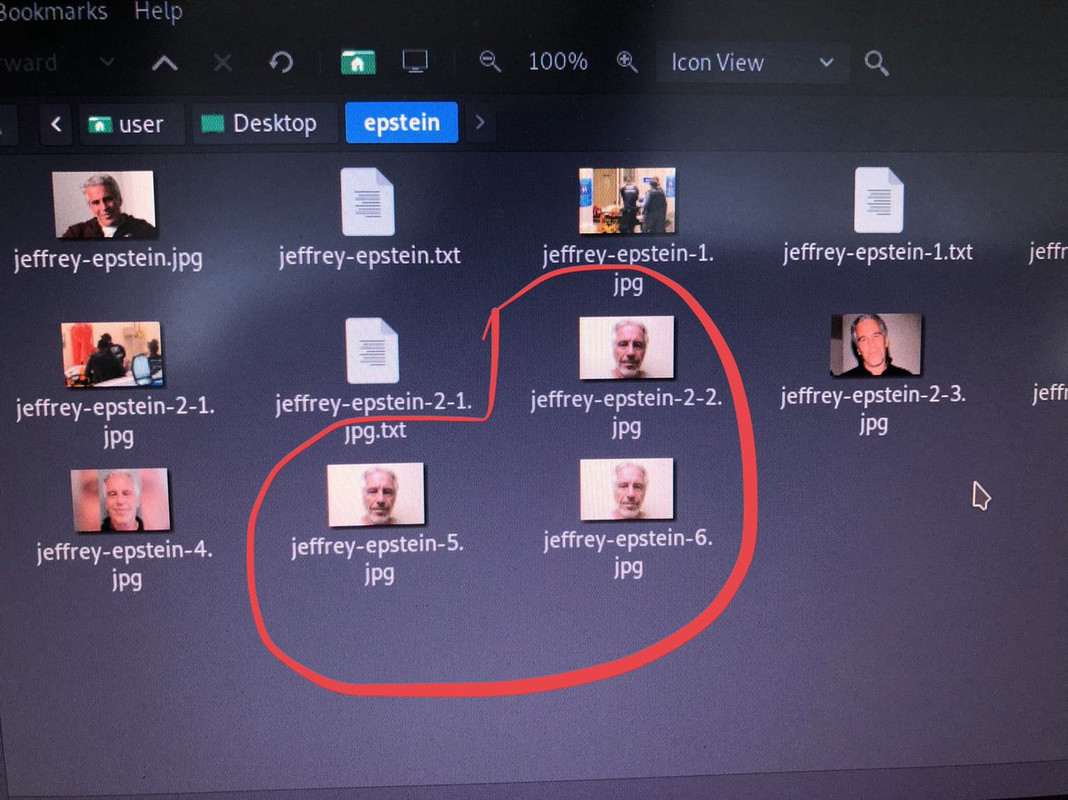
Usually, multiple images would make sense when you have maybe a high res & a thumbnail version, but the “smallest” of the file sizes was over 500kb—definitely not a small JPG. Even stranger, the other 2 images were BIG: 1.6Mb and 1.8Mb.
That didn’t make sense.
So, I scanned those pics first—the context of there being 3 “duplicate” images was bugging me.
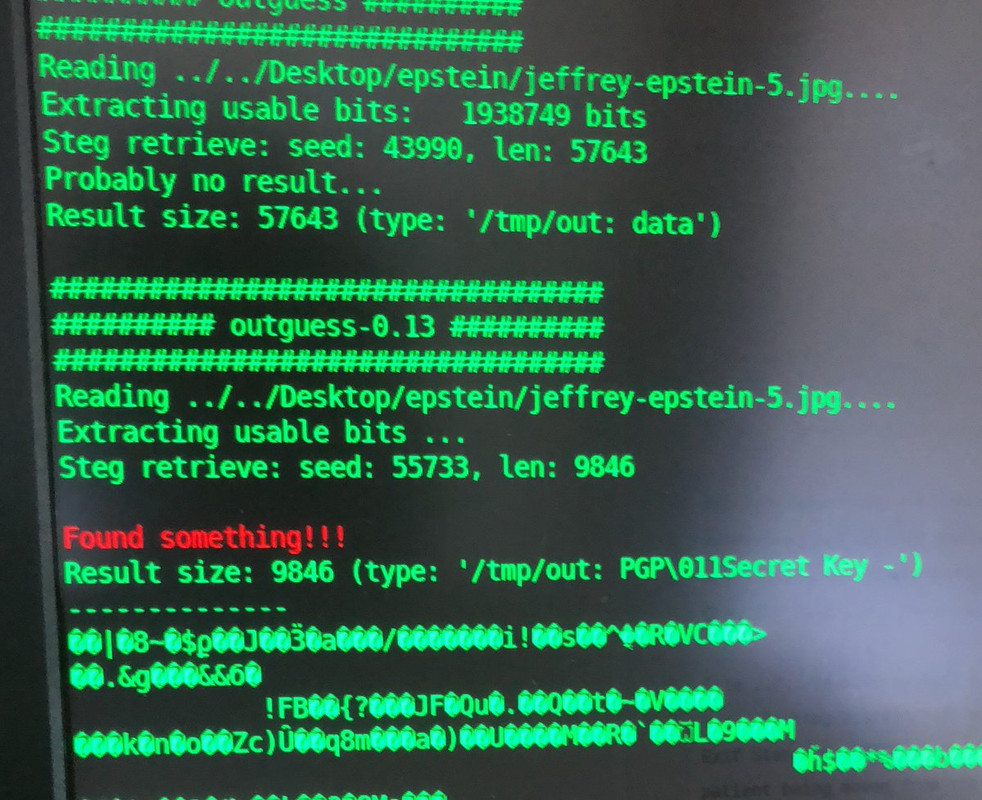
To my surprise, not only did ALL 3 of them have a little bit o fishyness to them (some hex and stuff in the EXIF), but one of the files seems to have a PGP key embedded using OutGuess!!
Again, I mentioned earlier OutGuess being used (In-n-OUT burger made OutGuess the first tool I wanted to run). If you’re a follower of the “Q boards”, you probably know there are numerous instances of #steganography being used.
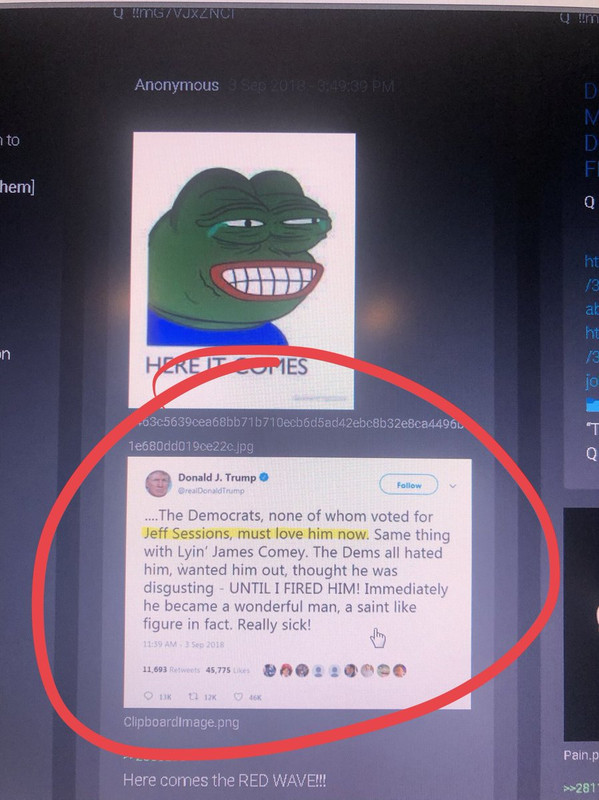
Here’s some possible appended data on a Q post:
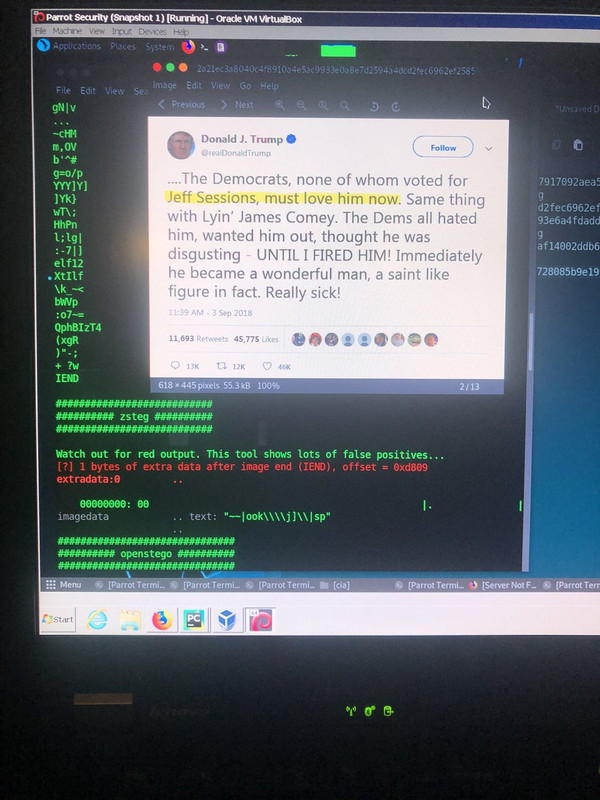
@GitmoChannel says he has found indication of F5 Stego in a number of images on the “Q boards” as well.
If you remember last July, there was a photoshopped pic of Sarah Silverman that alluded to using PixelKnot (F5 Stego). Point being—Steganography is pretty common.
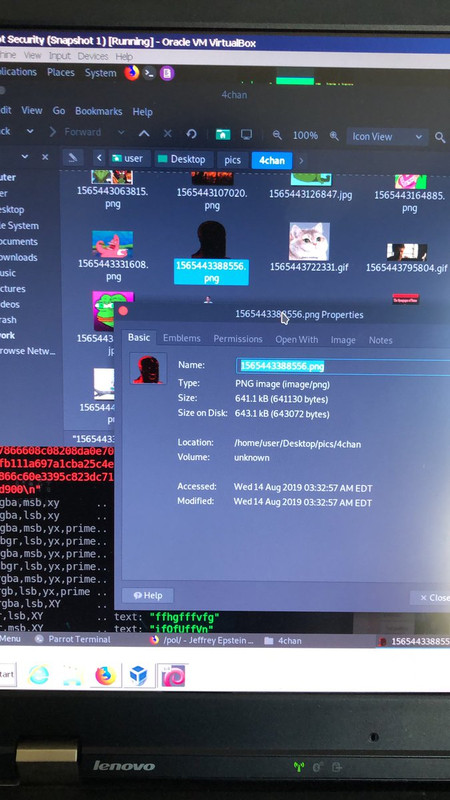
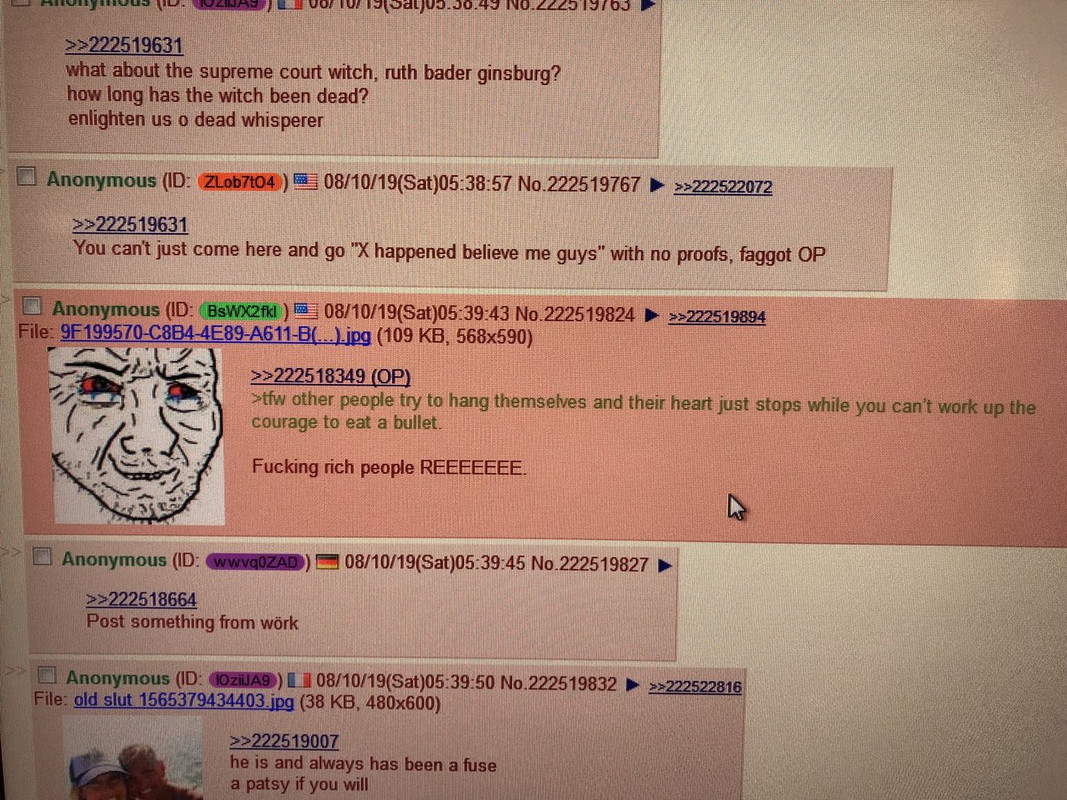
Here are some more 4chan/8chan examples of seemingly “normal” pics, blending into the thread. (Coded messages/conversations)
You’d never know if you weren’t specifically looking for it...
Think:
“Data exchange”
“EXPAND your thinking”
“You have more than you know”
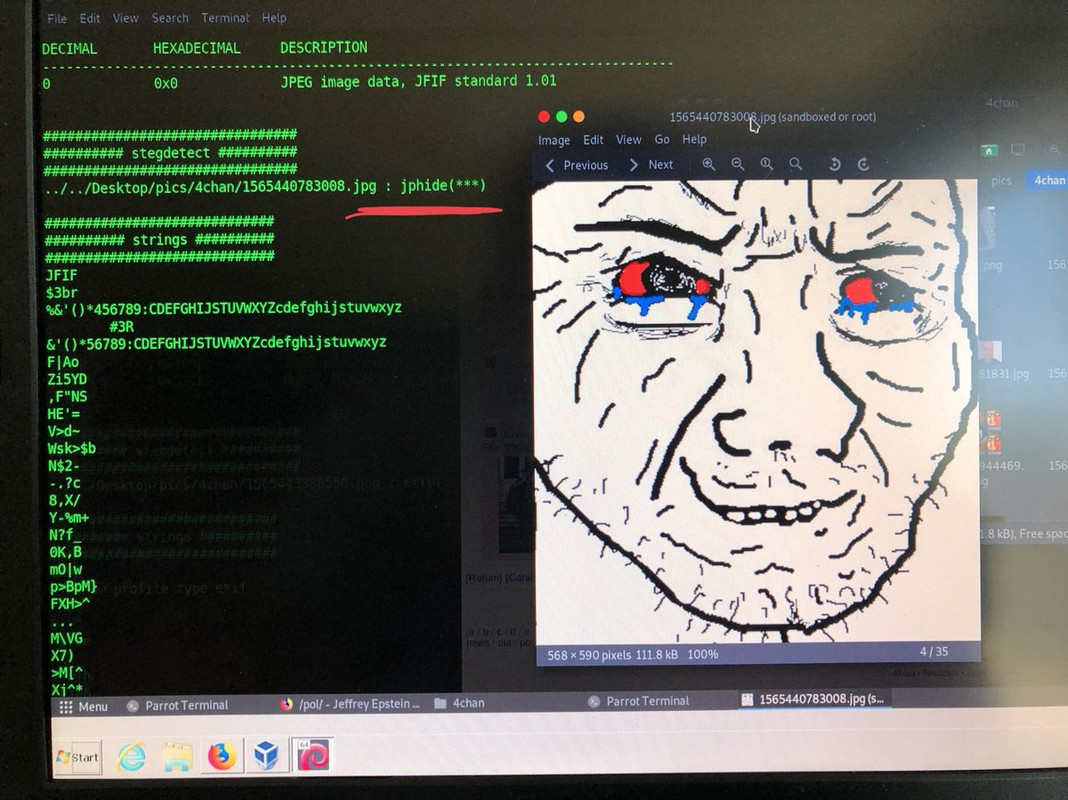
“How do you HIDE a message in CLEAR sight?” (JPHide? Alpha/transparency bits/LSBsteg?)
People are so quick to doubt things because they lack understanding. It’s easier to believe something is false than to realize you are unaware/uninformed.
“Things aren’t always as they seem”
So back to the PGP key—there were some oddities. First, the file is on the large size according to a very astute colleague.
At almost 10k, this is a “big” key file. So, I went to try and locate examples of extra-large key sizes & was able to find an example of 16k key.
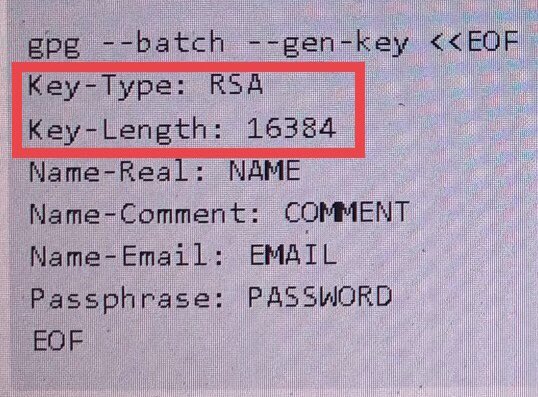
Why would someone want such a super-secret-extra-secure Key?? Uhhh... well, indulge me for a moment and assume you’re a “Mockingbird Media” CIA contractor: You need to setup secret/secure comms with an asset/source/handler The bigger the key, the harder it should be to “crack” 🤷♂️
The key is binary data, but that’s not unexpected. It may even be further encrypted, obfuscated, or even intentionally damaged (to make solving the puzzle harder).

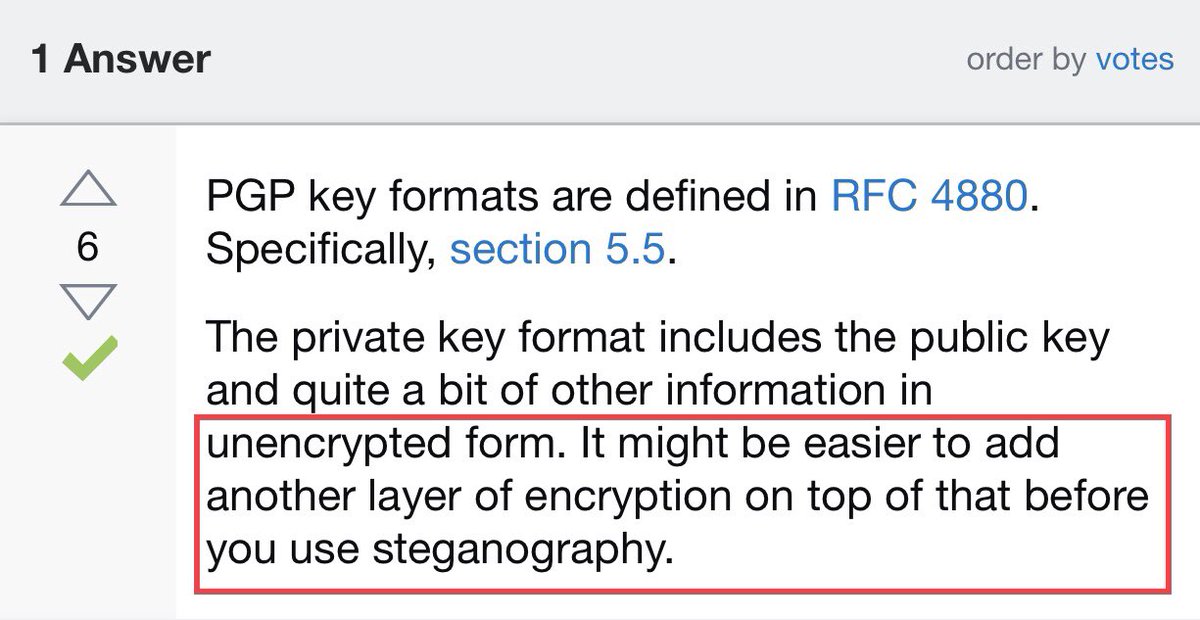

As I was saying about “intentionally damaged”— This is somewhat common in CTF/Capture The Flag challenges involving Steganography. Here is a walk-through Re: a CTF where a .ZIP file was hidden in an image, but the zip was intentionally damaged, requiring you to HEX EDIT to fix it.
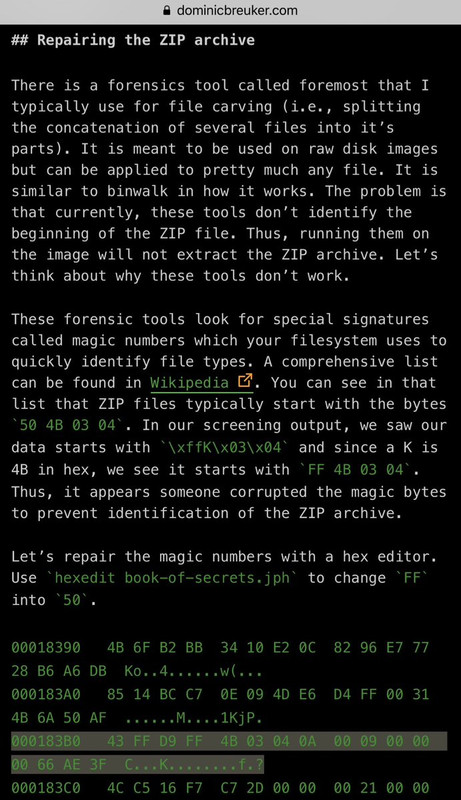
I tried a small handful of things to figure out who the key belonged to & what it was securing, but I’m not a PGP expert. 🔐😬 What next? Do I Binwalk & carve out those bytes? Hex editor? I’m not 100% sure what I’m looking to even fix/check exactly. 🤷♂️
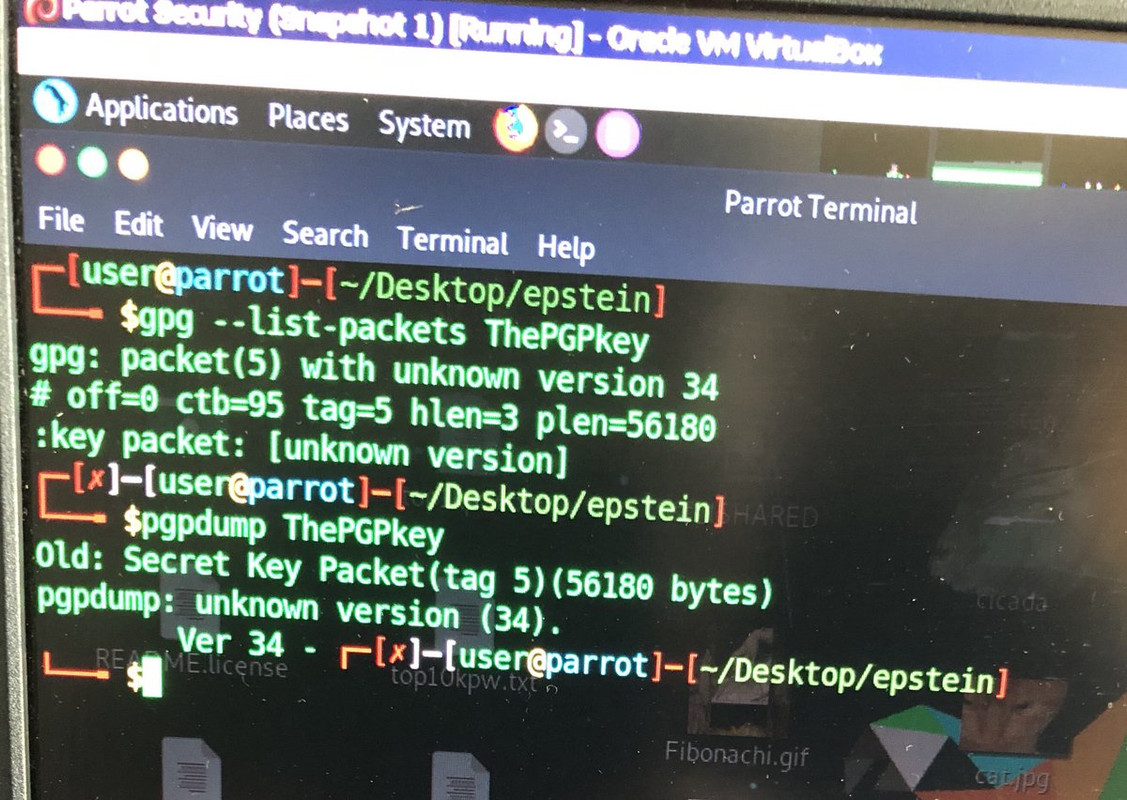
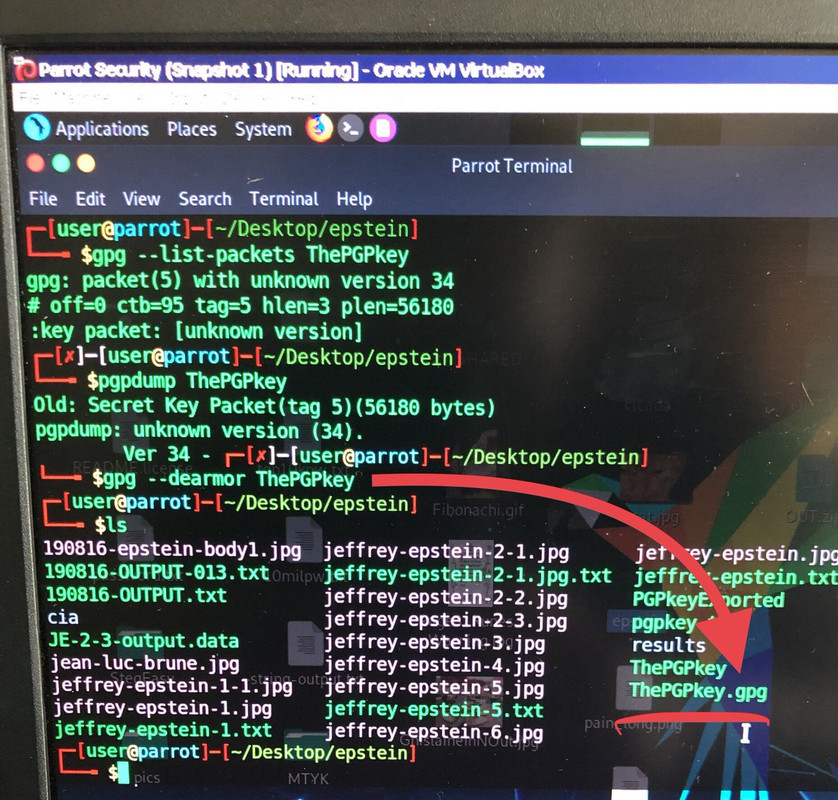

So, here are all the files I grabbed from the NYPost’s own website, outputs from scans, and the PGP Key/pair (binary) extracted out of one of the Jeffrey Epstein images.
So, here are all the files I grabbed from the NYPost’s own website, outputs from scans, and the PGP Key/pair (binary) extracted out of one of the Jeffrey Epstein images.https://t.co/eIHmVyPSHd— Luke Slytalker & The Force (@_Luke_Slytalker) September 4, 2019
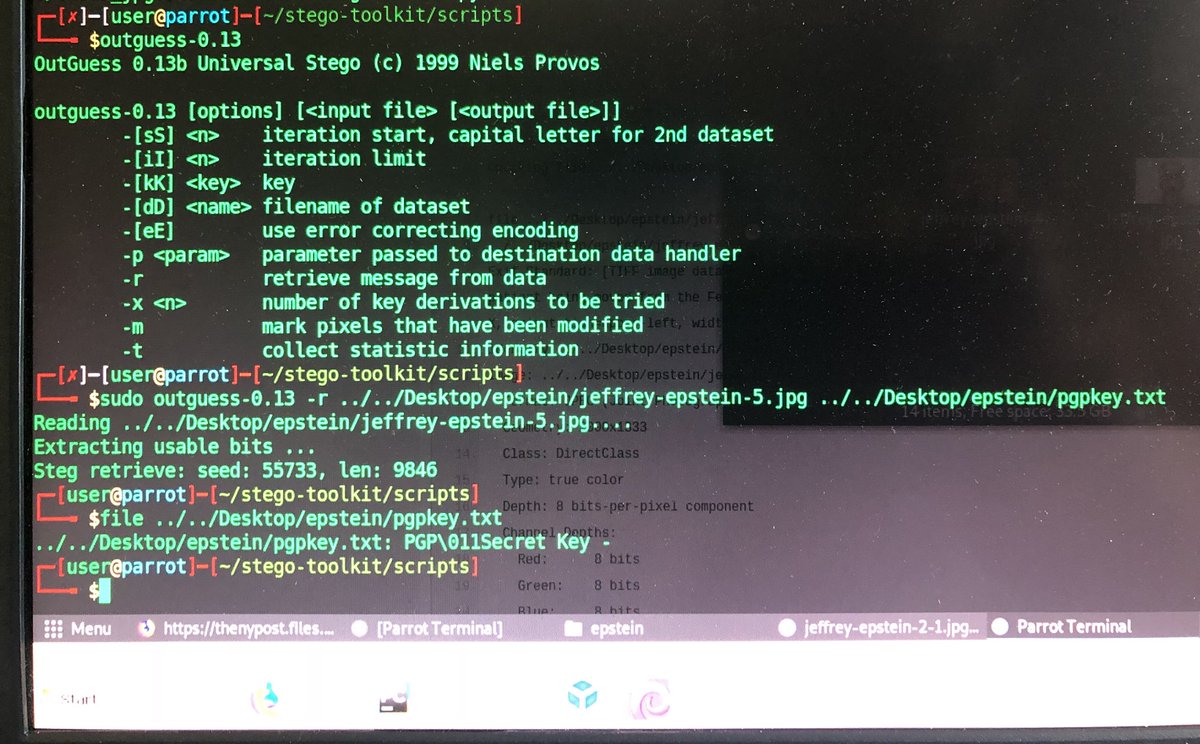
Further info... I ran a number of tests with OutGuess, Steghide, and a few others Steganography tools, then tested the detection & extraction of “controlled” files (ones I KNEW had data, and ones I knew didn’t)
OutGuess would find useable bits to extract, but it would then wrongly assume it was wrong and say “probably no result..”
However, forcing OutGuess to extract will reveal the hidden files that I knew were there (and then running “file ” & have Linux squawk back the Type)
So, what’s it all mean then?
Stego doesn’t happen on accident.
Someone put that PGP Key in there intentionally Someone with access to the NY Post’s website/CMS Seems like spy-craft The implication seems that #OperationMockingbird is at @nypost? 🤷♂️
Edgy Guy [4]
Have you figured out what the key is for? A local folder? A cloud drive?
Luke Slytalker & The Force.
Lazer Blazer
Have you looked into which articles have steno images and is there a correlation to article authors?
Luke Slytalker & The Force
That’s what all you guys are for now. 😉 I need the #hiveMind to jump in and pick up where I left off.
Not sure. That’s why I finally dropped the info. I was done looking into it.
Time for others to pick it up & see what they can add/contribute. 🤷♂️
Deplorable SQ
So my first question would be: If you find multiple pictures with embedded keys, are the keys the same or different. Lazyness would indicate the keys would be the same, but the best security would be if each photo had a newly generated key that would only be used once.