credit: WhatsApp
Posted on 04/11/2016 7:09:26 PM PDT by Swordmaker
A cross-platform messaging app owned by Facebook leapfrogs iMessage; Apple should step up and join it.

Apple’s security and encryption strategies have received a lot of attention lately, from the way in which iOS devices’ data are locked down to how Apple doesn’t have the encryption keys the iMessage and FaceTime systems employ to secure its users’ communications to how Secure Enclave keeps our secrets secret. But WhatsApp, an app-based text, video, and voice service with a billion users, took the spotlight Tuesday with the news that its users have end-to-end encryption as well.
WhatsApp has a couple of legs—and maybe an arm or two—up on Apple, which has designed iMessage and FaceTime to exclude itself from the equation. Both Apple and WhatsApp, acquired by Facebook in 2014, can’t gain access to the encryption keys used to secure communications sessions. But WhatsApp’s approach and user interface go even farther, in ways that Apple should be considering—and, for all we know, may be building into their operations right now.
The impact of WhatsApp’s shift is broad, because its apps are available across all major and some minor mobile platforms, and it’s used broadly on both flagship and less-expensive phones found across the developing world in dictatorships and emerging democracies, as well as countries with ostensibly long-upheld freedoms. It’s a competitor to iMessage as a system, even though it works on iOS devices.
The Electronic Frontier Foundation (EFF) collaborated back in 2014 to create a scorecard for messaging systems that I continue to refer to regularly. It’s been kept up to date, including the latest WhatsApp improvements. The team that created this guide had seven criteria that provide users a basis for trust.
Some systems had poor marks and remain laughably bad, including Skype—it seems secure, but has so little outside oversight and design problems that it’s effectively impossible to know if it’s trustworthy. It doesn’t mean it’s broken, but we just can’t know whether it is nor be sure that any given session hasn’t been suborned.
Apple scored well enough, with 5 out of 7 marks for FaceTime and iMessage, though another checkmark appears overdue for removal based on research by Johns Hopkins security academics that was released on March 21. Apple’s four legitimate marks cover encryption in transit, encrypted messages that the provider lacks the ability to decrypt, proper documentation of how its system works, and an outside audit has been performed in the last 12 months, whether the results are public or not. (Google doesn’t place well at all with its chat and hangouts system.)
In three regards, Apple falls down. First, there’s no way for parties using the system to confirm independently that there’s no one eavesdropping on the encrypted session. Second, Apple doesn’t open its encryption code to outside review. And finally, even though the EFF currently displays this checkmark for Apple, the Johns Hopkins work shows that past communications in iMessage, if captured in encrypted form, could be decrypted later by encryption keys that remain available. This is called “forward secrecy.” (The paper notes, among other things, that the researchers have demonstrated “an active attack on iMessage encryption that exposes current iMessage users to decryption of past traffic.”)
WhatsApp’s new update, based on code adapted from and with the help of Open Whisper Systems, was a significant move forward for that ecosystem, and trumps Apple on two counts. While based on open-source code, WhatsApp doesn’t yet make its implementation available for others to scrutinize.
Is it a competition to get all the green checkmarks and even exceed expectations? Sure, it can be, if that prods Apple to catch up. There’s no financial reward directly attached, but it would move Apple closer to its stated goals of keeping its users secure and itself completely out of the message chain. This is a corporation bragging-rights battle that benefits us all.
Forward secrecy is extremely important in any cryptographic system. By creating new keys that all parties agree to use on a frequent basis and destroying the old ones, any intercepted “ciphertext” is vastly harder to unscramble, even if a snooper was sucking down data from the moment two or more parties started a conversation for the first time.
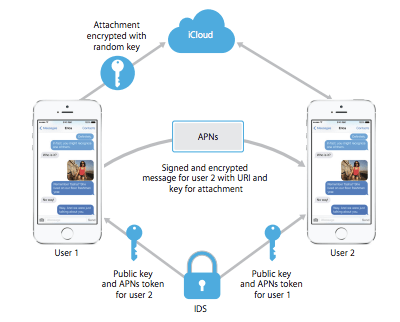
WhatsApp’s implementation creates a new key for every single message. A white paper released by the firm notes, “The Message Key changes for each message transmitted, and is ephemeral, such that the Message Key used to encrypt a message cannot be reconstructed from the session state after a message has been transmitted or received.”
There’s no technical reason why Apple couldn’t migrate to a system, and which the Johns Hopkins authors urge. It requires re-architecting the system, which the paper gives many reasons for in general. (And, again, Apple has already very likely been working on improvements of this sort for some time.)
There’s a slightly related aspect not covered in EFF’s scorecard: where and how unencrypted transcripts of messages are stored. Apple archives iMessage conversations from iOS devices as part of iCloud backups, and there’s no way to to disable this. You also can’t delete these transcripts from an iOS device without wiping and restoring the device. iCloud backups are much more simply encrypted, and by obtaining a password or through an offline attack, their contents can be extracted.
WhatsApp doesn’t retain this information off-device by default, and you can wipe previous conversations at will within the app. (You can choose to enable iCloud-based WhatsApp message backup, as well as backups on other platforms.)
Finally, WhatsApp makes it extremely easy for parties in a conversation to verify that there’s no snooper in the system. A man-in-the-middle attack in a cryptographically protected channel uses a well-designed protocol requires the malicious party to essentially cut themselves into the conversation.
Imagine Alice holding a tin can with a string attached that passes from her bedroom window, through a treehouse, to Bob’s window, where he has a matching tin can. Pull it taught, and they can talk. Eve, however, sitting in the treehouse, cuts the string and attaches a tin can on the two ends. She relays Bob to Alice and Alice to Bob, and she’s a very good impressionist. 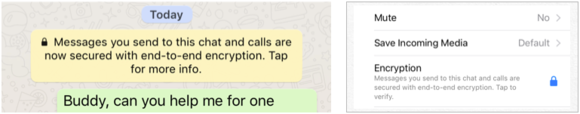
WhatsApp makes it clear that encryption is enabled and that you can check up on whether it’s being intercepted.
In the crypto world, any number of ways can be used to set up session encryption in which two or more parties communicate securely by confirming each other’s information. In a closed system, a provider can use cryptographic signatures combined with information unique to users to prevent, block, or notice any interception. However, if that’s bypassed through a flaw or an inside party with privileged access, users wouldn’t know.

A screen with a security code in a form that can be scanned or read by a person let you verify with another party that nobody has interposed themselves.
Where WhatsApp steps in is through an optional verification step that lets each party confirm that the other has the same session information. While an eavesdropper can create separate sessions in each direction at a carefully selected point on the Internet, they can’t forge the encryption key that’s unique to each user.
WhatsApp has a variety of signals, too. On the Contact Info page, it shows whether someone is up to date with their WhatsApp client and available for a connection. When a session starts, the app notes that the session is encrypted. You can tap either on the contact page or on the security note and get a Verify Security Code screen, which shows both a 2D QR code, and a 60-digit number in groups of five digits.
Two people in the same place can scan the code (either person may do so); people without that phone capability or not correct can read the code off as text. Unlike Eve, the perfect impressionist above, it’s effectively impossible to interpose on demand someone reading digits aloud to another person that is both in real time and sounds like the other person.
If the code doesn’t match, something’s gone wrong. Either the wrong code was picked—the wrong contact or someone has multiple accounts—or a third party has interposed themselves. I asked Moxie Marlinspike, one of the principals at Open Whisper Systems, what someone should do in this circumstance. He replied via Twitter, “The only recourse a user has (in any context where keys don’t match) is to avoid communicating on that channel.”
Of course, there remain aspects of WhatsApp’s ecosystem that are problematic. It’s impossible without constantly audited outside information to be sure that the company hasn’t modified its software to comply with government requests or malicious intent—we can try to assume the latter, but we can’t be assured of the former.
Apple, Google, and other messaging providers should look at WhatsApp’s current high bar and try to leap above it.
Pinging dayglored, ThunderSleeps, and Shadow Ace for WhatsApp cross platform secure messaging App information.
The latest Apple/Mac/iOS Pings can be found by searching Keyword "ApplePingList" on FreeRepublic's Search.
If you want on or off the Mac Ping List, Freepmail me
How does the app Viber compare in terms of encryption and security?
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.