
"These are actual masks used by the engineering team to train the neural network to protect against them in Face ID" (Apple)
Posted on 11/12/2017 4:49:25 PM PST by Swordmaker
Questions & Answers
(Updated November 11, 2017)
Q: How Face ID was set up?
A: It learns from human face, just like normal.
Q: Were you able to use the mask to unlock the iPhone immediately after freshly enrolling the real face? The reason I ask is that, according to Apple's whitepaper, Face ID will take additional captures over time and augment its enrolled Face ID data with the newly calculated mathematical representation. Can you describe precisely how you went about conducting this experiment?
A: It does not matter whether Apple Face ID "learns" new images of the face, since it will not affect the truth that Apple Face ID is not an effective security measure. However, we knew about this "learning", thus, to give a more persuasive result, we applied the strict rule of "absolutely no passcode" when crafting the mask.
Q: Can you explain why your hack worked but similar attempts (like Wired magazine's) failed?
A: Because... we are the leading cyber security firm ;) It is quite hard to make the "correct" mask without certain knowledge of security. We were able to trick Apple's AI, as mentioned in the writing, because we understood how their AI worked and how to bypass it. As in 2008, we were the first to show that face recognition was not an effective security measure for laptops (related links can be found at the end of this writing).
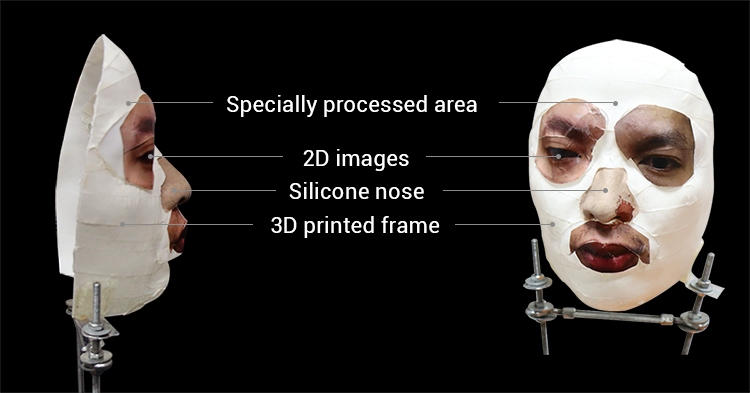
Q: How did Bkav develop the mask (for example why you use silicone for the nose, why 3D printing for some areas while special processing for others, etc.)?
A: You are right. Many people in the world have tried different kinds of masks but all failed. It is because we understand how AI of Face ID works and how to bypass it. As stated above, we were the first in the world to show that face recognition was not an effective security measure for laptops.
Q: Is 3D creation and printing difficult?
A: Not at all. It is quite simple, will be even more simple in the future. We might use smartphones with 3D scanning capabilities; or set up a room with a 3D scanner, a few seconds is enough for the scanning.
An easier way is photograph-based, artists craft a thing from its photos. Take the nose of our mask for example, its creation is not complicated at all. We had an artist make it by silicone first. Then, when we found that the nose did not perfectly meet our demand, we fixed it on our own, then the hack worked. That's why there's a part on the nose's left side that is of a different color (photo attached). So, it's easy to make the mask and beat Face ID. Here, I want to repeat that our experiment is a kind of Proof of Concept, the purpose of which is to prove a principle, other issues will be researched later.
Q: Are the dimensions of a person's face needed? How would those be obtained without a target sitting for them?
A: The 1st point is, everything went much more easily than you expect. You can try it out with your own iPhone X, the phone shall recognize you even when you cover a half of your face. It means the recognition mechanism is not as strict as you think, Apple seems to rely too much on Face ID's AI. We just need a half face to create the mask. It was even simpler than we ourselves had thought.
Apple has done this not so well. I remember reading an article on Mashable, in which Apple told that iPhone X had been planned to be rolled out in 2018, but the company then decided to release it one year earlier. This shows that they haven't carried out scientific and serious estimation before deciding to replace Touch ID with Face ID.
The 2nd point is, in cyber security, we call it Proof of Concept, which is useful for both sides, the hackers and the users. The hackers, they can find out a simpler way to exploit users' device based on such PoC. While with users, if they know about such possibility, they will not use the feature to keep themselves safe.
Just like the KRACK attack, it is not easy to be successfully exploited but users are urged to update the patch ASAP, because the threats are real. With Face ID's being beaten by our mask, FBI, CIA, country leaders, leaders of major corporations, ect. are the ones that need to know about the issue, because their devices are worth illegal unlock attempts. Exploitation is difficult for normal users, but simple for professional ones.
Q: What technologies and techniques were employed to make the 3D model associated with the 3D-printed portions of the mask?
A: We used a popular 3D printer. Nose was made by a handmade artist. We use 2D printing for other parts (similar to how we tricked Face Recognition 9 years ago). The skin was also hand-made to trick Apple's AI.
Q: What's the approximate cost of the mask?
A: ~ 150 USD
Q: How long did it take to construct the mask, including the time to develop 3D models and other assets associated with its production?
A: We started working on it, including 3D models and other assets, right after receiving iPhone X on Nov 5.
Q: Who would be the target for this kind of attack?
A: Potential targets shall not be regular users, but billionaires, leaders of major corporations, nation leaders and agents like FBI need to understand the Face ID's issue. Security units' competitors, commercial rivals of corporations, and even nations might benefit from our PoC.
Q: The clip is not clear enough. Your clip and answers have not included all details. Can you record another clip of this experiement with more details?
A: I want to repeat that our experiment is a kind of Proof of Concept, the purpose of which is to prove a principle, other issues will be researched later.
Q: Is this a kind of deframing your competitor?
A: This is the work of our cyber security domain. As you have learnt from above answers, from 2008 when Bkav had not developed Bphone (Bkav.com/Bphone), we were the first company in the world to show that face recognition was not an effective security measure for laptops, right after Toshiba, Lenovo, Asus, etc. used this technology for their products (related links can be found at the end of this writing).
Q: According to Bkav, up to now which security measure is the most secure?
A: As for biometric security, fingerprint is the best.
-------------------------------------
Face ID beaten by mask, not an effective security measure
Vietnam, November 10, 2017 - At iPhone X launch event, Apple's Senior Vice President Phil Schiller claimed that Face ID can distinguish human's real face from masks thanks to its artificial intelligence (AI). "They (Apple engineering teams) have even gone and worked with professional mask makers and makeup artists in Hollywood to protect against these attempts to beat Face ID. These are actual masks used by the engineering team to train the neural network to protect against them in Face ID. It's incredible!", Phil Schiller said (Apple's Keynote September 2017, from 1:27:10 to 1:27:26). However, one week after iPhone X officially went on sale, Bkav security experts from Vietnam show that Face ID can be fooled by mask, which means it is not an effective security measure.

Below is the video that demonstrates how Face ID is beaten:
(You can as well watch the video on YouTube —How Face ID be beaten by a mask
Mr. Ngo Tuan Anh, Bkav's Vice President of Cyber Security, said: "The mask is crafted by combining 3D printing with makeup and 2D images, besides some special processing on the cheeks and around the face, where there are large skin areas, to fool AI of Face ID".
So, after nearly 10 years of development, face recognition is not mature enough to guarantee security for computers and smartphones. In 2008, Bkav was the first company in the world to show that face recognition was not an effective security measure for laptops, right after Toshiba, Lenovo, Asus, etc. used this technology for their products. You can find out more details in the links below (note: Bkis is the former name of Bkav):
1. Laptop face-recognition tech easy to hack, warns Black Hat researcher (Computerworld)
2. Face recognition bypass demonstration clip by Bkis at Black Hat Conference
3. Vietnamese security firm: Your face is easy to fake (CNET)
We will publish the research which helps us to craft the mask that beats Face ID in the next writing.
Bkav
About Bkav:
Established in 1995, Bkav Corporation (www.bkav.com) is the leading firm in network security, software, smartphone manufacturing (Bkav.com/Bphone) and smarthome. Bkav is the first company in the world to discover the vulnerability in face recognition log-on in laptops right after this technology started to be popular. Before, the technology was trusted to be highly accurate and was used in products of many technology companies around the world like Toshiba, Lenovo, Asus, and so on.
Bkav is known as the security firm to discover the first critical flaw in Google Chrome just days after its launch in 2008. Bkav was also the firm to trace the master server in Britain of unprecedentedly massive DDoS attacks targeting US and Korean governments' websites in July, 2009.
First of all, their VP of Cyber Security is swiping up immediately as soon as the enter passcode screen appears when the iPhone X comes on . . . but THAT IS NOT WHAT HAPPENS when an iPhone X comes on.
The passcode screen appears only when you want to enter the passcode if you are not going to open it without FaceID by swiping up and then waiting from the normal lock screen after it does not recognize your face. It does NOT appear just when you start the iPhone X. It will only appear when there is a problem with FaceID or you have not trained the iPhone X for FaceID.
Secondly, I noted is Bkav stated they were going to have a FaceID mask WITHOUT a passcode. SAY WHAT? That is not possible. Apple has programed the iPhone X to not allow a FaceID without a passcode as a safety fall back.
Thirdly, I watched the lock at the top of the screen. . . and it NEVER, EVER ANIMATED the UNLOCK motion of a padlock unlocking. He just quickly swiped up and the ten key unlock screen disappeared to reveal the home screen as if he had actually unlocked the screen. On my iPhone X, if I attempt to swipe up before that padlock unlocks, it is not unlocked. And my lock screen bounces back down. His motion is TOO QUICK to see what is actually happening.
Fourthly, the FAQ above about "covering half your face and it still works" is completely bogus". I just sat here and covered various halves of my face and the lock shook "NO" each time and refused to unlock with each half covered, no matter what half I had covered. So, they lied.
As Judge Judy says, you lie in one part of your testimony, all must be suspect.
Fifthly, the claim that a working 3D mask could be made from a photograph is entirely bogus. No mere artist working from a photo can ever construct a truly accurate 3D image of the real person the photo imaged. It is just not possible. There are just too many variables. Yet, Bkav tosses this off as something easy.
Sixth, the masks that Apple created to do their testing were far more sophisticated than Bkav's mask. These professional mask makers made masks that are indistinguishable from their models, down to the micrometer and they failed to unlock FaceID. Bkav making their mask's nose out of silicone by hand, especially ad hoc, means NOTHING dispositive because the infrared light is not going to treat it differently than it would a real nose, makeup, or any other surface. This is just bogus magician's patter, misdirection, by use of techy terms, just as is the claim of "using an artist to make the skin surface," to sound like it was really important to make a mask that was "so complex" to "fool the AI."
Seventhly, say that again: "Fool the AI"? The "AI" is a fast calculating Neural Engine that can do 600 billion calculations per second to adjust for every possible angle the face may be looking at the sensor and comparing to the reference face data.
Eighthly, one of the things FaceID is looking for is an actual look from the user's eyes toward the sensor. . . something a MASK, especially one mounted as this one is, with fake eyes, cannot do.
Ninthly, the amount of time it would take to make such a mask to target any individual iPhone X user is most longer than the maximum 48 hours FaceID would likely be available to unlock the device on a trial and error testing that such a mask obviously holds. . . during which time it could be disabled in minutes by FindMyiPhone if stolen or lost. Any of the targets they list were arrested, kidnapped, or compromised, etc., they'd be smart to have someone trusted left, say their attorneys, with instructions to brick their iOS devices they have with them. So much for this as a security issue.
Finally, this is a company that is NOT a security firm. They are a company that SELLS a competing ANDROID PHONE. . . one that uses a fingerprint sensor for security, these claims are really suspect. . . and they are attempting to push their phone's security as being much more secure than Apple FaceID.
From all of the above, I think that it appears that what they are doing here is bringing up a static screen shot of the passcode entry screen and merely swiping up to reveal the home screen. The timing is right, the speed is right, and the motive is there.
This is the typical approach of a marketing ploy of a company with something to sell smearing the more secure competitor claiming they've found a way around their competitor's security. . . by spreading Fear, Uncertainty, and Doubt.

The latest Apple/Mac/iOS Pings can be found by searching Keyword "ApplePingList" on FreeRepublic's Search.
If you want on or off the Mac Ping List, Freepmail me
Who would go to the trouble of making such a mask though? And how would they do it without you knowing something was up?
As Wired pointed out in their article on their failed attempts at making a mask to get into the iPhone X, "Who is dumb enough to allow a crook to dump several pounds of silicone mask mould on their face without their cooperation or fail to notice it if they aren't cooperating?"
When they were describing the process, they showed it took several hours to mould the face, then lots more hours of effort to make the masks. . . days in fact. By that time the iPhone X's capability to USE FaceID of its user would have expired.
Thanks for posting this bro.
"We're professionals. Don't try this at home. It won't work for you, because you're not a professional..."
Sounds a whole lot like the propaganda doubletalk I have come to expect from the Norks, specifically the CLFK, himself...
I was struck by that type of answer about why they were successful and Wired wasn’t. . . Paraphrasing here: "We’re professionals. We know things nobody else does, so that makes our mask better. We’re even better than Apple."
I thought it arrogant of him to latch onto the rumored speculation, and that’s all it was, that Apple was really planning on rolling FaceID out next year but rushed it out a year early, unready and incomplete, just so they could include it in the Anniversary iPhone X. Absurd!
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.