Posted on 08/15/2022 7:25:26 AM PDT by Red Badger
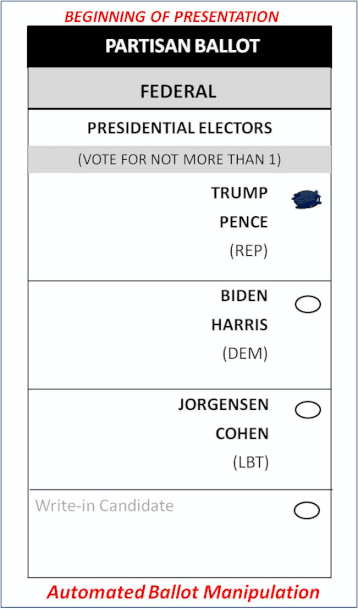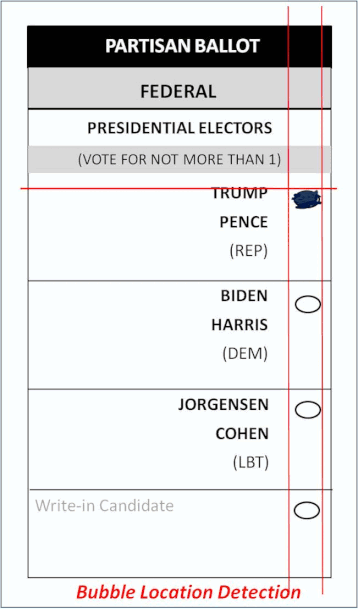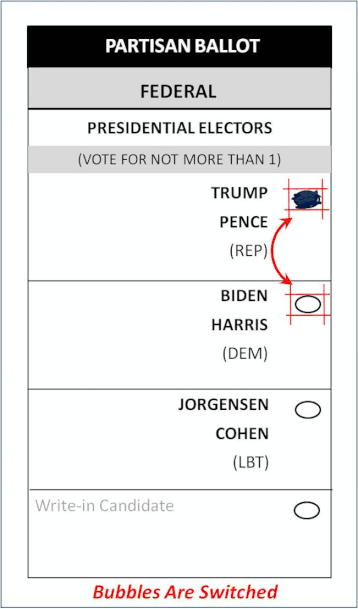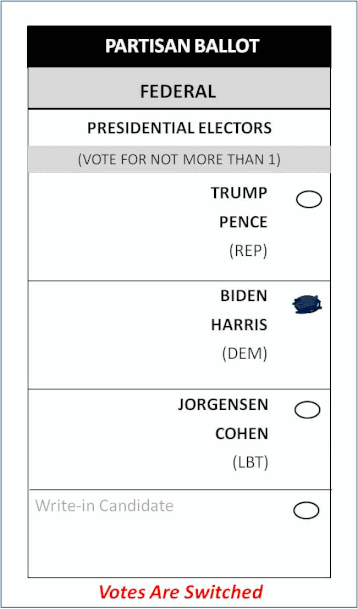
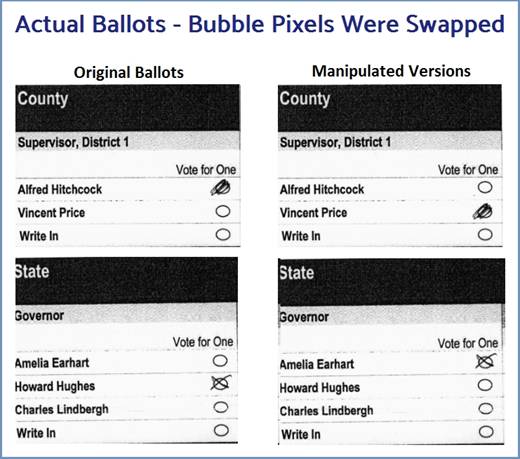
There’s an election hack built before the 2020 election that can instantaneously swap the bubbles on your ballot. The “filled in” bubble of your candidate is moved to the hackers preferred candidate, and swapped out with that empty bubble. The change is made before the “ballot Image” is stored to the election server, and before it’s tabulated. By using the voter’s own marking style & penmanship, these changes are undetectable to the human eye.
Here’s the scenario. Using a blue pen you fill in the “Trump” bubble on a ballot. Election officials insert this ballot into a tabulator. Those pixels surrounding the Trump bubble are swapped in milliseconds with the empty Biden bubble pixels. After these changes are made, the ballot image is saved to the EMS, and the candidate selections update the election totals. If an election jurisdiction uses their digital “Ballot Images” to conduct an audit, they WILL NOT find these changed ballots.
Gateway Pundit created the below animation to provide a visual how this election attack works (or view here). Any real election attack using this method has no visual component. It operates behind the scenes, completely hidden.

To conduct this type of an election attack, bad actors just need a sample ballot. These are published well ahead of all elections. The sample ballot is used to located the exact bubble positions. The ballot is segmented into a grid, or “bounding boxes“. Vertical and horizontal lines sweep the ballot to precisely locate the targeted candidate’s bubbles. Bounding boxes are made around each bubble. Extra white space is added around the bubbles to account for penmanship that strays outside the bubble. This becomes the template for that election. The pixels inside these boxes is what they swap.
Prior to the election, the attacker specifies the template, which races they want to affect (Pres, Senate, etc), and by how much. While ballots are being scanned, this malicious software keeps a running tally of the “real” ballot results. Ballot images are changed on the fly to achieve the desired election outcome. To avoid detection, attackers can specify just enough manipulated images to win the race, but not by alarming amounts. The only way to catch this hack is to compare the original paper ballot to the ballot image.
Awhile back two University of Michigan students successfully wrote this malicious software using only 398 lines of code. Their “Automated Ballot Manipulation” video and 18 page whitepaper show the details. Undergrad Jeremy Wink and grad student Kart Kandula developed it while at UofM’s Security Lab. They were under the supervision of election expert J. Alex Halderman. Using the voters own handwriting markings to alter ballots is a truly devious approach. Depending on the computer, the entire process takes about 40 milliseconds (.04 seconds). It leaves no image artifacts behind, so the changes are undetectable.

The students tested it against EAC certified scanners. They also tested it against all six different ballots styles used in America. These come from manufacturers Dominion, ES&S, Clear Ballot, Diebold, and two styles from Hart InterCivic. The ballot styles for Dominion machines were the easiest to change. The Hart eScan ballots were the most difficult. The software can move all shapes used on election ballots including bubbles, circles, boxes, rectangles, ovals, etc.

This sophisticated software algorithm scores and rates the marked bubbles as Sensed, Ignored, or Marginal. Some voters might make excessive scribbles, or stray into the letters of a candidate name. If the pixel area can’t be perfectly swapped leaving no artifacts, the algorithm skips that ballot and moves onto the next one. Configuring the software settings very high, so it leaves no trace evidence, they were able to change votes on at least 50% of all ballots.
To illustrate an illegal election operation the two men created an attack package called “UnclearBallot”. They disguised the attack by inserting malicious code into the “Windows Driver” that allows the scanners to communicate with the election system. They created a “microdriver” that essentially “wraps” around the original driver. This is what changes the ballots. But their malicious software can run in any environment. It doesn’t have to be a driver. It can be rewritten for a machines firmware, installed on an Election Management Server (EMS), and so on.

They simulated an attack using 181,541 completed paper ballots from Clackamas County. Oregon. They changed the results of ballot proposition. UnclearBallot was configured to only modify marks with a “high confidence” the alteration would not be noticeable. They were able to alter 62,400 ballot images, which is 34%. Afterwards, they selected 1,000 altered ballots at random for examination. Human auditors could NOT detect any evidence of ballot manipulation. Had they lowered the “confidence” settings, they could have changed 89% of the ballots. Only 11% were rejected, had no chance of changes.
What’s most alarming is that Matthew Bernhard was involved, a Research Engineer at the hard left Voting Works. The Center For Democracy and Technology (CDT) created Voting Works, spun it out in 2018. CDT’s major donors are the Soros Open Society, Ford Foundation, MacArthur Foundation, Google, Facebook, Amazon. Others involved in this election project were Chinese speakers Henry Meng, Jensen Hwa, and Kevin Chang. In 2019 CISA and DHS partnered with Voting Works to push their bogus Risk Limiting Audits into many States before the 2020 election. It’s now used by 10 States. Voting Works has been an obnoxious proponent of mail-in ballots.

Students Jeremy and Kart noted there are technologies available that can detect this type of image manipulation on ballots. However, they were unable to find one election jurisdiction using any of this technology. Their team also suspects it would become an arms race. When the software that detects “image manipulation” advances, attackers will obtain it, and alter their malicious code to defeat it.
NOTE: A “driver” allows an external device like a printer or scanner to communicate with the operating system. The driver is the first thing the external device talks to. In a nutshell, the data flows from a scanner, to the driver, to the OS, and then to the hard drive. By putting the malicious code at the very begging of this flow, it can change ballots before the OS even knows about it. The ballot bubbles are changed before the “Ballot Image” gets stored on the election server.
When I see “Jim Hoft”, I don’t bother reading the article.
Technology…. Voting the way the programmers program. Ain’t technology grand !
“Reality exists in the human mind, and nowhere else.”
― George Orwell, 1984
During the recent French elections voters were shown marking paper ballots which were put in little envelopes and then put into a transparent ballot box. Ballots are hand counted with multiple observers. Even President Macron voted that way in his Paris district. If the French can manage an election this way why not in the UD
Or exists in the propaganda the media and elected tell one is the truth
“Nothing was your own except the few cubic centimetres inside your skull. ”
― George Orwell, 1984
“There was truth and there was untruth, and if you clung to the truth even against the whole world, you were not mad.”
― George Orwell, 1984
For that exact reason.
They want ALL ELCTRONIC VOTING so they can STEAL ELECTIONS AD INFINITUM..................
To anyone who had actually programmed for a living, yes computers can do just about anything but walk on water. For our systems here in PA they design the ballot and the scanner/counter matches the design. the ballot changes after every election twice a year, obviously. Best practices and auditing can handle any of these issues, but in many cases are not performed at the election commission or DOS levels. And again the fraud is not by the big bad scanner counting machine but a person a programmer. software compiled hash codes can verify if all software matches. and it should. again. people can commit fraud all along the way. with out audits and best practices you can’t stop them. And Bookvar and the people at DOS in PA resisted the mandatory audit of the SURE systems which clearly outlined problems with the people updated the voter roles. The audit proved that the DOS is incapable of carrying out an election.
Don’t worry, Be happy quotes
“The choice for mankind lies between freedom and happiness and for the great bulk of mankind, happiness is better.”
― George Orwell, 1984
And the majority of mankind never experiences Freedom
“The masses never revolt of their own accord, and they never revolt merely because they are oppressed. Indeed, so long as they are not permitted to have standards of comparison, they never even become aware that they are oppressed.”
― George Orwell, 1984
Is this why we eat Hot Dogs on the 4th ?
Yuck! 🤢................That stuff will kill you!..............
LOL
Is this not just another facet (or similarity) to the so-called ‘ballot adjudicating’ that went on in the last election?... I recall a presentation particularly about this in Antrim, MI where the machines were set to intentionally generate a huge number of ballot errors.... which then forced those ballots to be transferred to ‘adjudication’ where there was no oversight or audit trail.
Doesn't stop you from clicking on the thread and posting your little nugget of wisdom though, does it.
Yes. The way he misrepresents and sensationalizes is pretty disgusting. I’ve been burned too many times.
Amen to that.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.