Posted on 05/13/2017 10:11:46 PM PDT by BenLurkin

No, that's not correct. The attacking software probes for SNMP v1 on listening computers and exploits the bug. There is no user involvement at all.
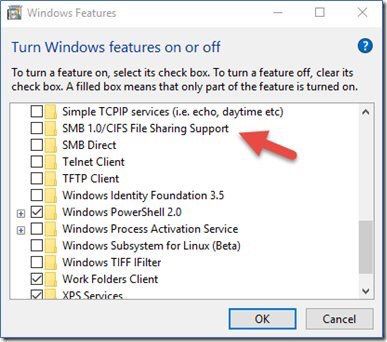
Sorry, that should say SMB v.1 not SNMP.
Anti-virus can't stop the attack. The attacking software connects directly to the vulnerable service and all that anti-virus does is stop execution of downloaded malware, clicking on attachments, etc. The only way to stop the attack is to stop incoming connections with a firewall. Windows firewall will do it, either stopping all incoming connections or just port 139 which has the vulnerability. You can also turn off SMB v1 compatability which stops it. Or apply the patch. I never patch so I have to do one of the other things to stop it.
Yep, that’s right. I did that (disabled SMB v.1) But I also stopped incoming connections, then realized I needed one. So I stopped incoming to port 139 instead using Windows firewall.
It was also mentioned close down port 445.
SMB (over TCP 445) is not something most businesses have wide open to the Internet. There’s no evidence that the infection is spread through direct injection via SMB exposed to the Internet. The infection has to be introduced into an environment and can spread from there. If SMBv1 is available (and MS17-010 is not distributed), it makes lateral movement all that much easier.
There are 2 compromises here: SMBv1, addressed by MS17-010, and WannaCry(pt). WannaCry(pt) is your typical run-of-the-mill ransomware with logic built into it to look for SMBv1 to compromise. That’s new. Otherwise, the infection has to start by someone stupid enough to let it loose in an environment, and I stand by my original post.
My thoughts exactly.
I have multiple back ups of every file.
..........just saw this this Sunday morning!
What my tech guy told me to do is just “turn it off” and it will go away. In my case, this threat was precisely known to him and all IT guys/gals. Namely, the culprits put a window saying EMERGENCY...........call Microsoft. Well, I bit and called the number. They sounded totally legit and even with background noise etc etc. But they were not Microsoft. They were crooks.
They will claim otherwise and give you "proof" that you have been hacked which is all lies. I have salvage computers that they were let into via someone turning on remote desktop. But it's not easy or pretty (I often end up with broken drivers as I try to remove various infections).
...........very good info to know. I’m a self taught guy and can use them well as long as they work and no outsider rocks the boat. I did suspect BS when this happened and though I did call the number (it looked so authentic), and I did talk to someone (she sounded REAL), I did not give them CC info or let them take over my computer.
All I did was turn it off and unplug it until I could talk to my teckie!
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.