Posted on 08/18/2013 8:48:59 PM PDT by LibWhacker
I’ve cobbling this entry together between uptime and downtime over the last couple of weeks so bear with me on this one. I think there’s a fundamental misunderstanding of how counter-insurgency intelligence and exploitation systems work so I’m going to touch on them a bit in this entry. It’s by no means comprehensive as that would take an entire volume to document. So what I’m going to attempt to do here is give the reader some insight into how an insurgency is identified, exploited, and targeted using a fairly simple and brief scenario.
Make no mistake that over the last decade plus the DoD, DoJ, DHS, NSA, and CIA have definitely learned their lessons. From shortly after 9/11 when the new lessons of counter-insurgency still lay ahead to the recent (last few years) capture and killing of Al Qaeda’s top officers the concepts and techniques of counter insurgency targeting have been vastly refined. Lessons learned not only on the battlefield but in the ops center have developed intelligence exploitation systems that are genuinely lethal due to their ability to be comprehensive and timely. Instead of sitting here typing out how these systems work I’m going to throw out a bit of a scenario for you. Not every system is represented but hopefully I’ll depict enough of them to give you an appreciation of just how dangerous they can be.
In this scenario we’re going to assume to perspective of the lead intelligence officer in a built up area with a fairly large population. Austin TX sounds good at this point. Anyway the country has de-stabilized to the point that National Guard units have deployed but martial law hasn’t been declared yet. Over the last few weeks we’ve been faced with a frequent insurgent attacks against logistics columns traveling up and down I-35 in areas around Georgetown and Salado. Additionally this (or other groups) have attacked the infrastructure junctions and in that area as well.
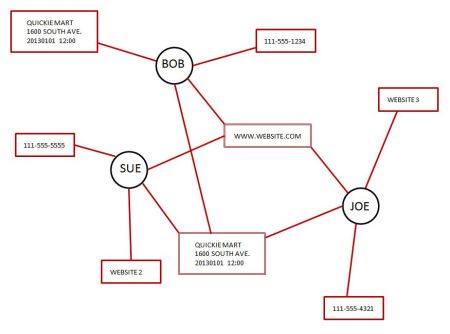
We just happened to get lucky (from our perspective anyway) and kill one of the insurgents and have possession of his body. He had no identification, the serial number on his rifle had been removed, and he had even gone to the trouble to remove his own fingerprints (talk about dedication). Those are some significant hurdles to overcome figuring out who this guy is right? Yeah, but not something we can’t work around. A quick phone call to the field gets us a good high resolution frontal image of the DIs (dead insurgent’s) face. The case officer uploads that image into a work file and sends it off to multiple agencies, say the DoJ (FBI specifically), DHS, and the State Fusion Center (there are more but let’s keep it simple). The Fusion center comes back a few hours later and identifies the individual as Bob Jones of Llano TX. How did they do that? By loading the pic of the DI into a biometric facial recognition program and running a comparison to Texas’s drivers license photo database. If they hadn’t gotten a hit it could have been compared to other states databases as well. It would have taken more time but eventually would have given us the identity. Now we have a starting point.
First thing we do is get a quickie warrant and pull all of Bob’s home and cell phone records for the last 90 days. Then we’ll identify every call he made or received in a certain radius say 200 miles. These calls automatically get categorized into business numbers and residential numbers. All calls will be looked at however we’re going to jump into the residential numbers first. In that pool we’ll separate the numbers into known and assumed family (by last name, tax returns, public records databases, etc.) and unknown reason contacts. In the last 90 days there have been roughly 300 calls to personal numbers which belong to a pool of 125 individuals. These 125 are now our short list for the time being.
Now we have an identification and an address it’s time to generate physical warrants. So the local boys go and raid Bobs home and take any and everything electronic, anything that remotely looks like correspondence, and any credit/debit cards or checkbooks. They even go so far as to search vehicles. But here’s an oddity: Bob’s truck isn’t at his house. And we know his make, model, and plate number by querying the state registration database and we put out a watch for the vehicle. Note at this point we’re not trying to build a case against Bob – **** he’s dead. We’re looking for cross referencing information to identify other remembers of his group. Once those items are collected they are handed over to a team of forensic technicians which begin to dissect the information and cross check other databases. Within 24 hours we have a comprehensive list of who he sent and received emails from, the IPs and cookies of the websites he’s visited, any purchases he’s made online and quite a few of the offline ones as well. Remember this isn’t all encompassing but intended to give you an idea of how it works.
All of this information gets laid out into what we’ll call a virtual “starfish” with each bit of info representing a point. We’ve got systems running the phone records down to individual names associated with those accounts referenced by physical location and date, systems referencing any known purchases referenced by location and date, and any and everything else we can dump into the system to expand the starfish. Once this part is done it’s time to start looking at known associations. We do this by take the folks we’ve already identified and trying to determine their association with good old Bob. For the sake of simplicity we’ll start on phone records – those 125 individuals. Those individuals names now generate their own starfish. As the multitude of systems begin to return information on each individual those starfish grow as well. at 36 hours to keep things simple we’ll reject all information on those other starfish if they do not correspond to any of the kegs on the starfish that represents Bob. That narrows down things considerably. Now it’s time for some human review (most of the action up to this point has been fairly automated. So we get a couple of analysts to start scrutinizing the associated information points between Bob and the other 125 folks we’re looking at. Some of the info can be dismissed fairly easily however other pieces have to be physically researched and even though it’s done via network it still takes some time. A couple of days later the analysts come back with a narrowed list of 16 people that could still be considered suspect however Bob had no contact with those people within 14-21 days of the attack in which he was killed. How did they arrive at the 16 people? Remember when the forensic team tore apart Bobs computer? They took his known data (his IP) and ran it across the stored multiple metadata databases to identify which websites he had been visiting. Of those websites a dozen were considered radical or fringe (at least under TPTBs definition of such). they then ran a cross check against those 125 folks from the phone records and 16 other people on our list had visited some of those websites.
What we have so far isn’t sufficient enough to start kicking doors in and shooting dogs so we’ve got to dig deeper. And for that we turn to financial transactions. Breaking them down into periods working outwards from the attack we find that Bob bought gas in Florence TX the evening before the attack. So now the Florence local boys get a call to specifically look for his vehicles. While that is going on we’re going to start looking at the transactions of those 16 other folks and compare them to Bobs. One thing that is puzzling is the fact that Bob didn’t have any phone or email contact with our new 16 person short list in the period immediately preceding the attack. Attacks are typically coordinated so there had to be some form of communication. By scrutinizing Bob’s debit purchase records we find that he had bought a “disposable phone” at the local big box store one day before his last contact with any of the 16 individuals we’re looking at. Getting the number to that phone isn’t hard at all with a quick warrant for the metadata for that carriers phones that were activated within a 36 hour period in Bob’s area. But for timeliness we’re also going to scrutinize those other 16 individuals transactions for the same type of purchase – disposable phones and we come up with nada for them.
The carrier returns the information from the warrant we wanted and two numbers show up as having been activated in the big box store parking lot within that time frame. A quick cross check shows one of the numbers has no association with any of our existing data however one has a call to his personal cell phone. Bingo we now have his number. And we can go back and get all of the metadata for that number including numbers called/received, location, time, and length of call. The phone data itself is built into a starfish of its own and cross referenced against any known contacts Bob had. The vast majority of it turns out to be other disposable phones which result in financial transaction dead ends (probably paid for by cash) but two do get a hit. The first is a call to Bob’s younger brother. The second is a call made from a diner near Georgetown the night before the attack. Bob’s younger brother now joins our short list simply due to association. Another quickie warrant and we’re going to get his brothers phones and computers and any correspondence. And we’re also going to start looking at the financial transaction and phone records of the other folks on the list to see if we can establish a point in time at that gas station or diner for any and all activity. Bob’s brothers stuff goes off to the forensics team for dissection and we wait for the data for the day preceding the attack. As that data comes in its correlated to Bob’s info and we come up with two positives. Bob’s younger brother called his house from that location at the same time Bob was there and a large meal charge was purchased on a debit car belonging to one of the 16 folks on our short list.
Meanwhile Bob’s vehicle has been found outside of Georgetown in a wooded area and the forensics folks descend on it to photograph and catalog everything – tire tracks, fingerprints, footprints, you name it. All of this info begins to get processed and correlated as it comes in to try and establish links to our known associations with bob. We get a hit off of this. A pair of shoeprints that match the size and model of a pair of another one of Bob’s known associates. How do we know they own those? Financial transaction records show they were bought a month prior to the attack with a debit card (hint – next time you buy a pair of shoes at Wally World look at your sales ticket – the model and size are listed).
Now we’ve got 2 hot suspects. More warrants, more seizures, more forensics. And now comes the time for interrogation. Bob’s brother is brought in and leaned on – hard. He’s good but the interrogators are better. These aren’t your run of the mill local PD Detectives – there are professional psychologists trained and experienced in mental and physical manipulation. Here’s some insight for you: If you’ve never been interrogated every second of it serves a purpose. The long waits are designed to build up anxiety. The sometimes cordial manner of the interrogators contrasted to the often brutal treatment from guards is designed to gain your confidence and make you feel more secure.
Anyway prior to interrogating Bob’s brother they build a profile of him and look for any and all means to break him – because that is precisely what interrogation is intended to do – make you talk. We’re not talking waterboarding here. Strong men can keep their mouths shut when being tortured. No we have to get at his psyche. So we gin up some false charge sheets and press releases naming him as a terrorist (which also happen to mention his wife and children’s names), let him know we know he’s associated with the guy that we got the shoeprints, from (everything we can present to make it look like we have a substantial volume of information), and we go a step further and have his kids picked up by human services and placed in foster care on the grounds of child endangerment – all to easily “substantiated” for the time being. One thing we don’t do is touch Bob’s brother’s wife – she’s critical to all of this. But we do freeze his accounts so he can’t afford a lawyer (or anything else for that matter like bail) . We’ve got to make her suffer so we let this run for a week – basically putting her through a mental ****. In the meantime we’re still working on Bob’s brother but after we’ve determined his wife is beginning to get desperate so we allow her to see him. The combination of all of this is what finally breaks Bob’s brother – **** the only person it wouldn’t get to is a true sociopath. So a few days later after we’ve let him mentally wrestle with the prospects of his and his families **** we offer him a deal. We’ll back off the family and return the kids, unfreeze the assets if he’ll talk and take a plea bargain of murder one with life instead of the death penalty. He initially refuses but after another visit by his wife a week or two later (and trust me we’re not letting things get better) he breaks. We’ve now got other names, places, times, and so forth.
With that info it’s wash, rinse, repeat of the entire process with each individual until we run into complete dead ends and wait for the next break – like another corpse. But within the span of a relatively short time we’re able to cripple the insurgency in the area for the immediate future.
Is this realistic? Folks **** like this is happening NOW. Biometric identification is real – you’re drivers license photo and thumbprint is in a database that routinely gets accessed at the state level and is available to the Feds (Fusion Center anyone). Facial recognition is how the Tsarnaev’s were initially ID’d. Your communications meta-data is routinely being stored and accessed by the government. Your financial transactions records are stored by your banks and creditors. All of this info is available through a rubber stamped fill in the blanks warrant.
So what happened? Bob was sloppy. Unreal ******* sloppy. He thought he was taking safeguards by using things like disposable phones but in reality his laziness killed his cell. If he had consistently used cash drawn out of ATMs in his normal routine for his purchases, if he had shown some phone discipline (seriously – that disposable phone ain’t for calling ma), and maybe if he had been a bit more discreet in his using technology the links might not have been established. But one link is all it takes and then the system starts chewing people’s lives up. And those links are how the powers that be identify and pursue their targets. Think your safe online? Even the vaunted TOR has been compromised by the DoJ lately.
These tactics are how insurgencies are broken. They’re what enabled the system to pin Bin Laden down, catch the Tsarnaevs, and identify drone strike targets in the middle east. Networks are deadly to an insurgency. Even operating in meatspace can be deadly without the right precautions. All it takes is for one person to use that phone to call or that debit card to pay and they’ve been nailed in time and space. Sure you may be using your regular phone (and not your disposable one) to call ma but you’re there and the records show it. And if your battle buddy does something similar he’s fixed at that time and place as well – so now both of you are associated. The key is discipline. When you meet you go completely off the grid. Completely. No phone use, no debit card use, nada in and around the geographic area and timeframe you meet. Recon and identify how you could expose yourself. Does a certain route have license plate readers? Then don’t use it. Convenience stores? They all have cameras at the counter and pumps. Nearby ATM machine? Cameras and transaction records. The golden rule at all times (and I mean all times) is to ask yourself:
How will what I’m doing at this second expose myself and others to identification?
In Bob’s case they started with a corpse with no fingerprints. Bob thought he was doing right by sterilizing himself prior to the attack but in reality he left gaping holes everywhere else. That one corpse is what allowed a local insurgency to be broken. The same techniques are used in Afghanistan with significant success despite the lack of things like financial transaction records. It’s used stateside on a daily basis. And all it takes is one sloppy SOB to destroy everything. Whether you’re a four man team, nine man squad, or distributed cells EVERYBODY has to have complete OPSEC uber alles hammered into them and practice it. And the larger your organization the more likely someone is going to get sloppy. Discipline and vigilance is the key not only to success but survival as well. It pays to have rules on who does what, who contracts whom how, and where and when all of this takes place. And those rules have to be understood and enforced.
Till next time stay frosty amigos.

Nut-job Conspiracy Theory Ping!
To get onto The Nut-job Conspiracy Theory Ping List you must threaten to report me to the Mods if I don’t add you to the list...
Yep...
bflr
Thanks null!
I'd like to make a few points here:
1) For the scenario given I could see how detection may have been possible, even inevitable,but
2) Bin Laden was eventually found by monitoring the driver IIRC, and the Tsarnaev claim of how they were 'caught' is completely unfounded. They were NOT detected beforehand, and they were not both found through means reported in this article. One was by searching for the vehicle through reports and the other was basically by widespread martial law-type canvassing, and lastly,
3) The article discusses 'insurgencies, insurgents, etc.' An insurgent is a foreign fighter of a group introduced into an area. How do these methods stack up against a 'revolutionary' network of citizens?
A fascinating post. It reads like a chilling parallel world.
Btw, read my longtime tagline...your cartoon could be me:)
shhhhh....don’t tell anyone
My interpretation of the Tsarnaev claim is only that the brothers were ID’d first with facial recognition, and that that knowledge helped authorities in their subsequent efforts to track them down.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.