
Posted on 05/15/2018 1:05:04 PM PDT by Swordmaker

Here’s how to protect yourself from the EFAIL vulnerability in Apple Mail on both iOS and macOS. These temporary fixes come after the new vulnerability was discovered that allows hackers to derive decrypted plaintext from encrypted emails. For the attack to work, the third party must be in possession of your encrypted S/MIME or PGP emails.
Although Apple’s likely to offer a fix to this vulnerability sooner rather than later, there are things you can do now to make your email more secure.
The Electronic Frontier Foundation (EFF) was the first to discover this vulnerability.
As previously mentioned, the first method involves removing the GPGTools/GPGMail encryption plugin from Apple Mail on macOS. To do so:
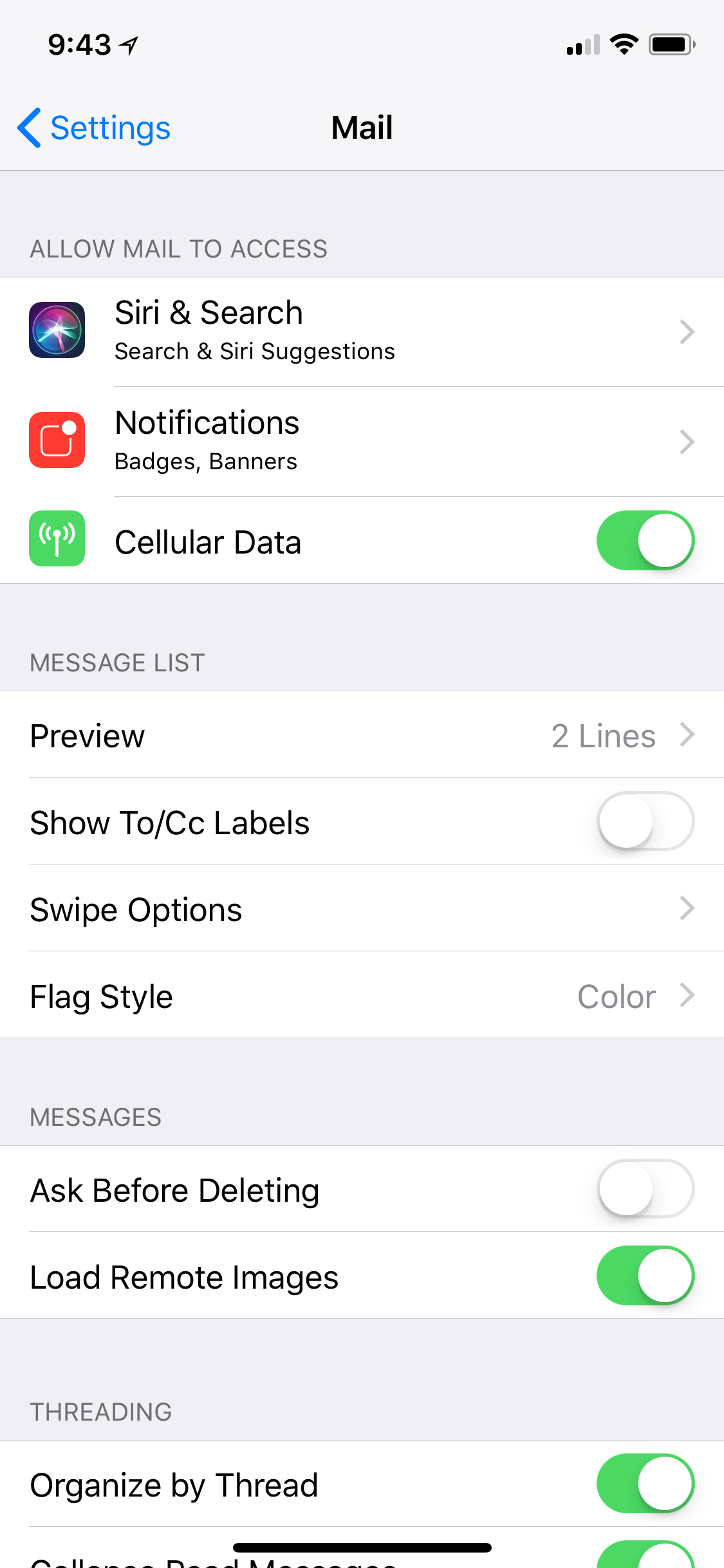
On iOS, you’ll need to just change the setting called “Load Remote Images.” To do so:
Keep in mind this vulnerability is most likely to occur in an environment that relies on S/MIME and PGP encrypted email communications to talk in private. The average Apple Mail user is almost certainly not using any of these tools.
You can read the technical details about the vulnerability from the EFF website.
We’ll let you know when Apple pushes out a fix for this issue. In the meantime, let us know what you think about this newly discovered vulnerability in Apple Mail and other email clients by leaving a comment below.
Thanks. BTTT.

If you want on or off the Mac Ping List, Freepmail me.
Bookmark
There's not much more on revealing plaintext of other emails other than the one sent by the attackers. The rest of the paper seems to leave that as an exercise, and just a possibiity. Other sources like SANS commentary says "Notably, the attacker needs full access to the target user's email account,..." presumably through some other flaws or vulnerabilities. It's pretty useless to simply expose the plaintext of an email sent by an attacker back to the attacker. The attacker obviously wants other plaintext of other emails in the user's inbox and there's no explanation in the academic paper of how to do that.
As a PGP user, I rate this concern "unverified". In any case, I never turn on (or always turn off) HTML fetching such as external images. It destroys privacy, wastes bandwidth, and the downloaded window dressing is totally useless.
My email client (thunderbird) doesn’t load remote images unless I tell it to do so. Love the Enigmail plugin for PGP/GPG
Bookmark
Hi Sword, it’s been awhile since we last communicated. I’m getting used to the Macbook laptop but still using the mini iPad and iPhone almost seamlessly. Only observation is the battery needs recharging once during the day if certain programs are used. Not a complaint, just an observation.
Lately, I’ve been reconsidering my gmail account and started paying for Hushmail. Have you any thoughts about Hippa compliant email services? Thanks. Hope you and the gf are well,
TW
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.