Image: Malwarebytes
Posted on 06/15/2018 3:34:22 PM PDT by Swordmaker
“Grayshift has gone to great lengths to future proof their technology and stated that they have already defeated this security feature in the beta build.”

Apple confirmed to The New York Times Wednesday it was going to introduce a new security feature, first reported by Motherboard. USB Restricted Mode, as the new feature is called, essentially turns the iPhone’s lightning cable port into a charge-only interface if someone hasn’t unlocked the device with its passcode within the last hour, meaning phone forensic tools shouldn’t be able to unlock phones.
Naturally, this feature has sent waves throughout the mobile phone forensics and law enforcement communities, as accessing iPhones may now be substantially harder, with investigators having to rush a seized phone to an unlocking device as quickly as possible. That includes GrayKey, a relatively new and increasingly popular iPhone cracking tool. But forensics experts suggest that Grayshift, the company behind the tech, is not giving up yet.
“Grayshift has gone to great lengths to future proof their technology and stated that they have already defeated this security feature in the beta build. Additionally, the GrayKey has built in future capabilities that will begin to be leveraged as time goes on,” a June email from a forensic expert who planned to meet with Grayshift, and seen by Motherboard, reads, although it is unclear from the email itself how much of this may be marketing bluff.
“They seem very confident in their staying power for the future right now,” the email adds.
(Excerpt) Read more at motherboard.vice.com ...
OK, so eliminate the hour. Make it necessary for the phone to be in unlocked state when attaching a USB device.

If you want on or off the Mac Ping List, Freepmail me.
Might not be a bad idea.
The Russians have already probably figured out a way to hack it.
I don’t use a passcode with my iphone. so what does this mean for me?
At my company Apple needs to be contacted. They get back to us in 2 to 10 days. Grayshift does this in 10 minutes or less...
You don't trade nude photos with Anthony Weiner? Probably means you don't have data to speak of on your phone.
Most of us with smart phones have financial info like account numbers, credit card numbers, and other contact info relevant to our well-being. I would not want anyone to be able to drain my bank accounts, or mess with my financial well-being. Nor would I want anyone pretending to be me trying to interact with my family and friends. Imagine what a bad person could do if they spoofed being you?
At my company Apple needs to be contacted. They get back to us in 2 to 10 days. Grayshift does this in 10 minutes or less...
However, if one uses a six digit numeric passcode, it takes more than an hour for any of the unlocking schemes to find the passcodes. The iOS device's Lightning port will stop passing data after an hour, thereby stopping the unlocking device dead in its tracks. The only devices still vulnerable would be those they could get a search warrant within an hour that had only a four digit passcode.
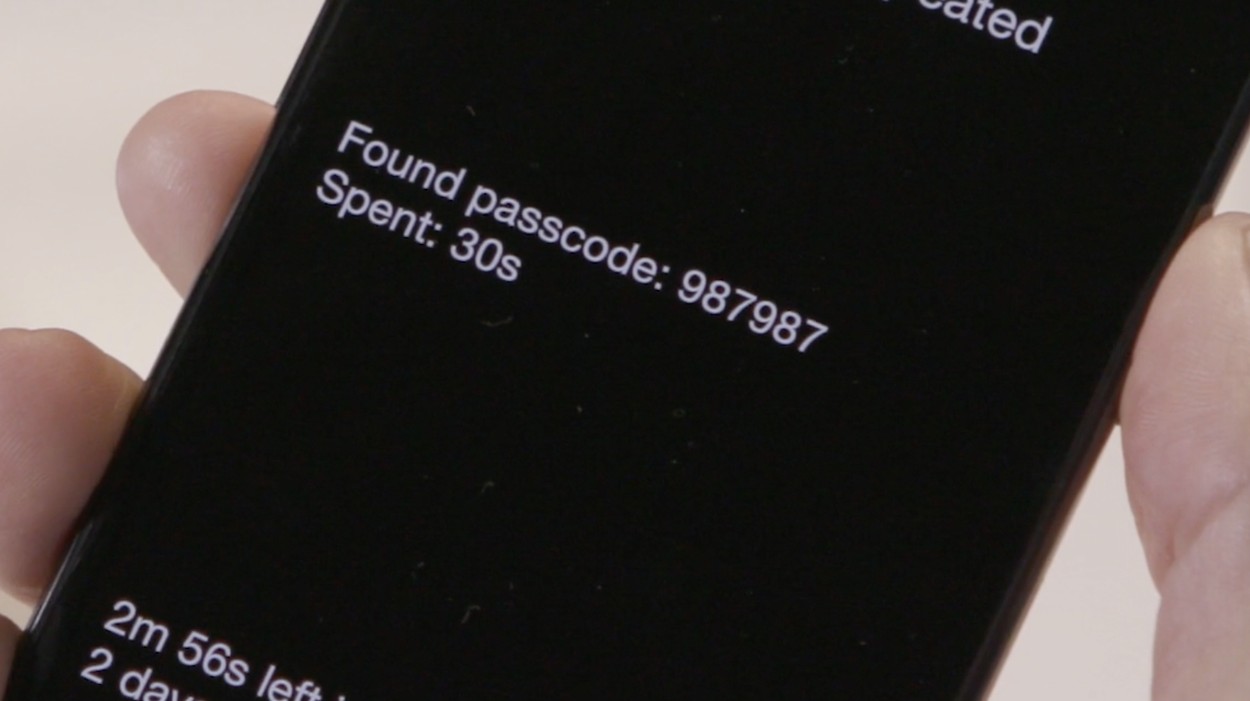
Times to crack an iPhone Passcode using brute force with GreyBox:
Best choice is to select complex passcode and use a mix of numbers, upper and lowercase letters, and symbols. For example: T5#v@&8>
While an 8 digit number has 10,000,000 possible combinations of a set of ten numbers of 0 to 9 in each position, 108, a combination of letters, numbers and the characters available on the iOS keyboard is much larger. There are 223 numbers, upper and lower case alphabetic characters plus foreign characters, and symbols available from the virtual keyboard on an iOS device. Thus the potential passcode combinations are 2238, or slightly more than 6.1 quintillion possible passcode combinations.
Given the 92 days worst case scenario to crack an 8 digit numeric passcode, a complex alphanumeric plus symbol passcode using the GreyBox would require a mere 152.8 BILLION years to crack. . . even now.
But 8 digits is overkill for what's really necessary. . . I think the time to crack a six character complex passcode would be sufficient. That has only 123 Quadrillion possible passcodes which the Greybox would need to crack. That would take only 1.5 million years or so to crack the average case six character passcode, not even the worst case passcode of 7 million years. . . before Apple does the upgrade at the end of this month.
A five character complex passcode has ~551,470,000,000 possible passcodes. That would take about 13,800 years in the worst case scenario or around 6,500 years in the average case.
Use that and I don't think we'd have much to worry about before the authorities or bad guys get at our private stuff.
The Russians haven't before. Both of the solutions here have come our of Israel.
If you don't you should. Without a passcode and someone steals your iPhone or you lose it, they have access to everything. You can't lock it or brick it.
BS. Minnesota_Bound. Grayshift only sells to law enforcement. . . they don't sell to "companies."
I manage a company that calls Apple and we are connected immediately, never a hold, or a wait of more than a couple of minutes to talk to a human being in the US.
Grayshift doesn't NEED to call back if you've bought their product. It's either in your police department, or it's on line for you.
Quit lying.
Onlu use 6 digits on both my phones BUT 4TH wrong entry bricks the phone permanently....you learn to pay attention
Secondly, i can remote wipe either in about 30 seconds from any other phone
The Russians use free lance hackers. They must not have the Israeli hackers on their payroll yet.
That description of the passcodes was simply elegant. Other than account numbers etc, I don’t have anything fun to steal. No naked 13 year olds on Epstein Island, no delivery records of my cocaine shipments, no connections to the Baeder Meinhoff gang, etc.
So I don’t see the FBI needing to attack my phone, but those passcodes are simply elegant.
Unless of course saying something defiant or scornful or rude on FR becomes a crime. Then I’ll be on the run I guess.
Exactly. Or allow the user to make it a selectable, shorter time. Like when the screen saver kicks in.
We do not use Grayshift nor did I say. If you read the article you would have understood this.
I'm still failing to understand why Apple would provide the ability to pass in the unlocking password via USB, rather than manually at the screen. Or why Apple would continue to allow password attempts at USB speed after a small number of attempts.
I’m not sure why Apple allows any access when the phone is locked. When I plug my phone in, I have no access to any files on the phone until I unlock it. Then, the internal/external SD cards show up in my computer.
Disclaimer: Opinions posted on Free Republic are those of the individual posters and do not necessarily represent the opinion of Free Republic or its management. All materials posted herein are protected by copyright law and the exemption for fair use of copyrighted works.